Simplex Chat is very popular in the Nostr community; whenever someone posts a note asking which chat app is secure, many people recommend Simplex Chat. We also think Simplex Chat is a great app.
So, many people ask what is the difference between Keychat and Simplex Chat? Is Keychat's security as good as Simplex Chat's? Is it really possible to create a chat app as secure as Simplex Chat on Nostr? Why not just use Simplex Chat? Why reinvent the wheel?
A common misconception in the Nostr community is that Nostr is not suitable for private things.
"Nothing about any of the protocols we’ve developed requires centralization; it’s entirely possible to build a federated Signal Protocol-based messenger, but I no longer believe that it is possible to build a competitive federated messenger at all." — Signal Founder Moxie https://signal.org/blog/the-ecosystem-is-moving%C2%A0
This is because the encryption process is completed on the client side, and relays only pass the encrypted messages.
Keychat and Simplex Chat both use the Signal protocol to encrypt messages, so both meet the following security requirements 1-4:
Anti-Forgery
Anti-Forgery ensures that the sender of a message is verifiable and the message has not been tampered with.
End-to-End Encryption
End-to-end encryption ensures that only the sender and receiver can decrypt and read the message content, protecting it from unauthorized access by servers or other network devices.
Forward Secrecy
Forward secrecy ensures that even if the current key is compromised, historical messages cannot be decrypted, since each message uses a new encryption key, which is deleted after use.
Break-in Recovery
Break-in Recovery ensures that if the current key is compromised, future messages cannot be decrypted, and the system can recover from the attack. This feature is also known as backward secrecy.
Metadata Privacy
Protecting the privacy of communication involves more than just protecting the content of messages; it also includes protecting the identities of the communication parties and other data.
Regarding the fifth point, metadata privacy. The designs of Keychat and Simplex Chat are different.
Simplex’s metadata privacy protection scheme
"Simplex chat is the first messenger without user IDs."
“To deliver messages, instead of user IDs used by all other platforms, SimpleX uses temporary anonymous pairwise identifiers of message queues, separate for each of your connections — there are no long term identifiers.”
“Temporary anonymous pairwise identifiers
SimpleX uses temporary anonymous pairwise addresses and credentials for each user contact or group member.
It allows to deliver messages without user profile identifiers, providing better meta-data privacy than alternatives.”
We can understand this mechanism as, if a Simplex Chat user has 10 friends, they have 10 IDs, using different IDs with different friends?
Keychat’s metadata privacy protection scheme
Current chat applications and email have forgotten that an address is not the same as an ID, treating the ID as the address. Emails and current chat applications send messages as [from: Alice's ID to: Bob's ID]. Regardless of how your geographical address changes, when Alice sends an email to Bob, it’s always [from: Alice's ID to: Bob's ID]. This compromises metadata privacy.
However, letters work differently; they are [from: Alice's current geographical address to: Bob's current geographical address].
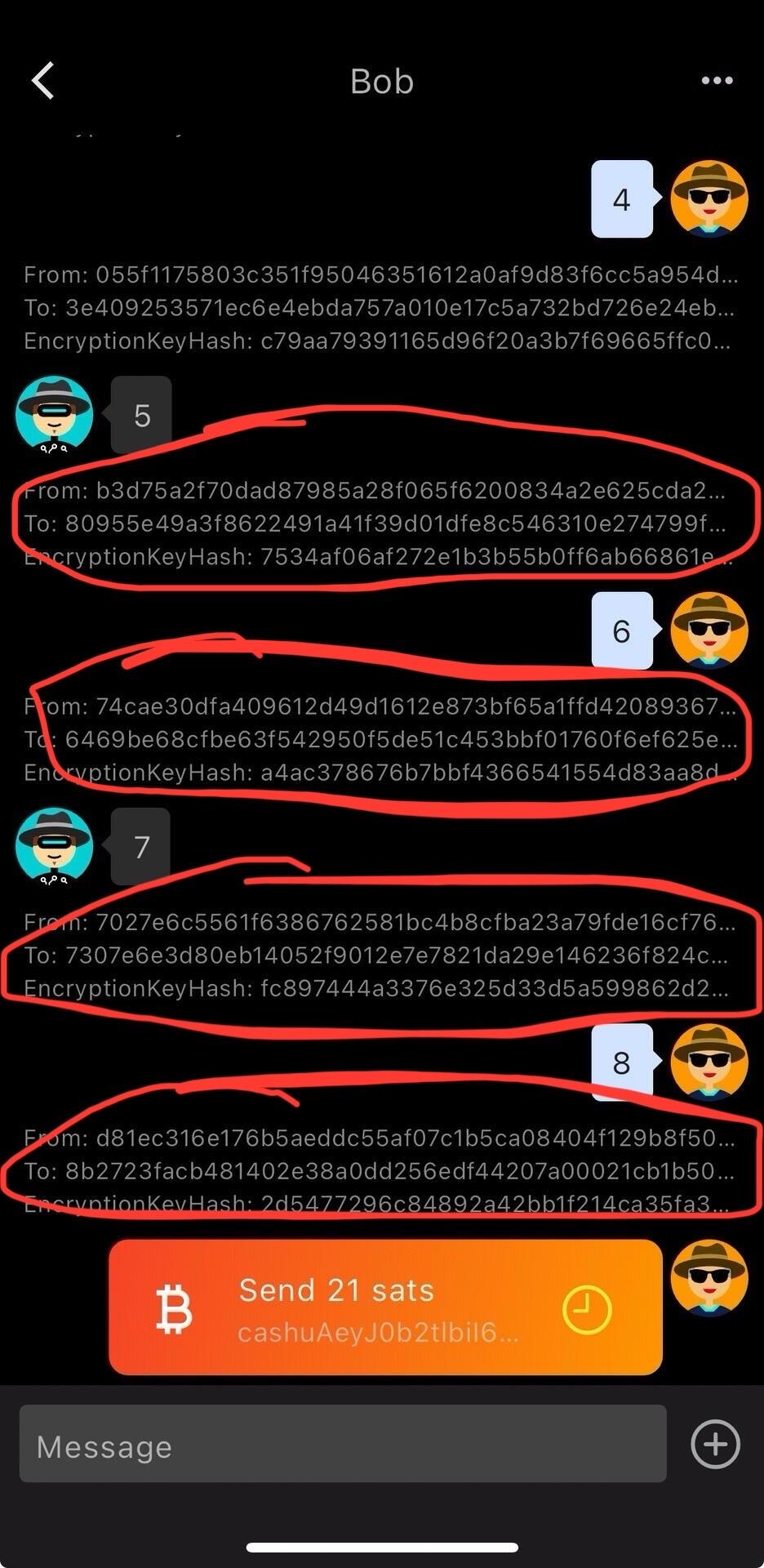
Keychat separates the receiving address and sending addresses from the ID, and the receiving address and sending addresses are also different. Keychat messages are [from: Alice's one-time sending address to: Bob's almost one-time receiving address]. This makes it difficult for outsiders and relay administrators to determine who is sending messages to whom.
Which scheme do you think is easier to understand and better protects metadata privacy?
Finally, Keychat also uses ecash sat as a stamp for messages, with relays funded by stamp revenue to sustain operations.
Login to reply
Replies (26)
Thanks for this explanation. Rebroadcast.
Nice explanation.
Your posts are always very insightful. Huge thanks
Can you comment on how notifications work on Android? I saw a notice about receiving addresses being uploaded to the notification server.
Setting up an ID and receiving a cashu token for stamps instantly (generated in minibits)... It's somehow still shocking how fast, frictionless and permissionless all these features feel.
It's almost so easy that normies aren't going to believe this stuff is novel.
Simplex Chat is very popular in the Nostr community; whenever someone posts a note asking which chat app is secure, many people recommend Simplex Chat. We also think Simplex Chat is a great app.
So, many people ask what is the difference between Keychat and Simplex Chat? Is Keychat's security as good as Simplex Chat's? Is it really possible to create a chat app as secure as Simplex Chat on Nostr? Why not just use Simplex Chat? Why reinvent the wheel?
A common misconception in the Nostr community is that Nostr is not suitable for private things.
"Nothing about any of the protocols we’ve developed requires centralization; it’s entirely possible to build a federated Signal Protocol-based messenger, but I no longer believe that it is possible to build a competitive federated messenger at all." — Signal Founder Moxie https://signal.org/blog/the-ecosystem-is-moving%C2%A0
This is because the encryption process is completed on the client side, and relays only pass the encrypted messages.
Keychat and Simplex Chat both use the Signal protocol to encrypt messages, so both meet the following security requirements 1-4:
Anti-Forgery
Anti-Forgery ensures that the sender of a message is verifiable and the message has not been tampered with.
End-to-End Encryption
End-to-end encryption ensures that only the sender and receiver can decrypt and read the message content, protecting it from unauthorized access by servers or other network devices.
Forward Secrecy
Forward secrecy ensures that even if the current key is compromised, historical messages cannot be decrypted, since each message uses a new encryption key, which is deleted after use.
Break-in Recovery
Break-in Recovery ensures that if the current key is compromised, future messages cannot be decrypted, and the system can recover from the attack. This feature is also known as backward secrecy.
Metadata Privacy
Protecting the privacy of communication involves more than just protecting the content of messages; it also includes protecting the identities of the communication parties and other data.
Regarding the fifth point, metadata privacy. The designs of Keychat and Simplex Chat are different.
Simplex’s metadata privacy protection scheme
"Simplex chat is the first messenger without user IDs."
“To deliver messages, instead of user IDs used by all other platforms, SimpleX uses temporary anonymous pairwise identifiers of message queues, separate for each of your connections — there are no long term identifiers.”
“Temporary anonymous pairwise identifiers
SimpleX uses temporary anonymous pairwise addresses and credentials for each user contact or group member.
It allows to deliver messages without user profile identifiers, providing better meta-data privacy than alternatives.”
We can understand this mechanism as, if a Simplex Chat user has 10 friends, they have 10 IDs, using different IDs with different friends?
Keychat’s metadata privacy protection scheme
Current chat applications and email have forgotten that an address is not the same as an ID, treating the ID as the address. Emails and current chat applications send messages as [from: Alice's ID to: Bob's ID]. Regardless of how your geographical address changes, when Alice sends an email to Bob, it’s always [from: Alice's ID to: Bob's ID]. This compromises metadata privacy.
However, letters work differently; they are [from: Alice's current geographical address to: Bob's current geographical address].
Keychat separates the receiving address and sending addresses from the ID, and the receiving address and sending addresses are also different. Keychat messages are [from: Alice's one-time sending address to: Bob's almost one-time receiving address]. This makes it difficult for outsiders and relay administrators to determine who is sending messages to whom.
Which scheme do you think is easier to understand and better protects metadata privacy?
Finally, Keychat also uses ecash sat as a stamp for messages, with relays funded by stamp revenue to sustain operations.
View quoted note →
It appears I have something else to learn about. I can't keep up on the tech realm it seems.
Simplex Chat is very popular in the Nostr community; whenever someone posts a note asking which chat app is secure, many people recommend Simplex Chat. We also think Simplex Chat is a great app.
So, many people ask what is the difference between Keychat and Simplex Chat? Is Keychat's security as good as Simplex Chat's? Is it really possible to create a chat app as secure as Simplex Chat on Nostr? Why not just use Simplex Chat? Why reinvent the wheel?
A common misconception in the Nostr community is that Nostr is not suitable for private things.
"Nothing about any of the protocols we’ve developed requires centralization; it’s entirely possible to build a federated Signal Protocol-based messenger, but I no longer believe that it is possible to build a competitive federated messenger at all." — Signal Founder Moxie https://signal.org/blog/the-ecosystem-is-moving%C2%A0
This is because the encryption process is completed on the client side, and relays only pass the encrypted messages.
Keychat and Simplex Chat both use the Signal protocol to encrypt messages, so both meet the following security requirements 1-4:
Anti-Forgery
Anti-Forgery ensures that the sender of a message is verifiable and the message has not been tampered with.
End-to-End Encryption
End-to-end encryption ensures that only the sender and receiver can decrypt and read the message content, protecting it from unauthorized access by servers or other network devices.
Forward Secrecy
Forward secrecy ensures that even if the current key is compromised, historical messages cannot be decrypted, since each message uses a new encryption key, which is deleted after use.
Break-in Recovery
Break-in Recovery ensures that if the current key is compromised, future messages cannot be decrypted, and the system can recover from the attack. This feature is also known as backward secrecy.
Metadata Privacy
Protecting the privacy of communication involves more than just protecting the content of messages; it also includes protecting the identities of the communication parties and other data.
Regarding the fifth point, metadata privacy. The designs of Keychat and Simplex Chat are different.
Simplex’s metadata privacy protection scheme
"Simplex chat is the first messenger without user IDs."
“To deliver messages, instead of user IDs used by all other platforms, SimpleX uses temporary anonymous pairwise identifiers of message queues, separate for each of your connections — there are no long term identifiers.”
“Temporary anonymous pairwise identifiers
SimpleX uses temporary anonymous pairwise addresses and credentials for each user contact or group member.
It allows to deliver messages without user profile identifiers, providing better meta-data privacy than alternatives.”
We can understand this mechanism as, if a Simplex Chat user has 10 friends, they have 10 IDs, using different IDs with different friends?
Keychat’s metadata privacy protection scheme
Current chat applications and email have forgotten that an address is not the same as an ID, treating the ID as the address. Emails and current chat applications send messages as [from: Alice's ID to: Bob's ID]. Regardless of how your geographical address changes, when Alice sends an email to Bob, it’s always [from: Alice's ID to: Bob's ID]. This compromises metadata privacy.
However, letters work differently; they are [from: Alice's current geographical address to: Bob's current geographical address].
Keychat separates the receiving address and sending addresses from the ID, and the receiving address and sending addresses are also different. Keychat messages are [from: Alice's one-time sending address to: Bob's almost one-time receiving address]. This makes it difficult for outsiders and relay administrators to determine who is sending messages to whom.
Which scheme do you think is easier to understand and better protects metadata privacy?
Finally, Keychat also uses ecash sat as a stamp for messages, with relays funded by stamp revenue to sustain operations.
View quoted note →
Single use IDs are less anon than making an encrypted note that only Bob can read and posting it right beside your public notes. This way Bob can hide in the annonimity set of all your followers.
Single use IDs are trivially discoverable by relay admins by looking at note retrieval queries. Only Alice and Bob will ever access a single use ID. That's an annonimity set of 2.
I support Keychat development and will continue testing it. It looks like it could mature and become something trustworthy in the Nostrsphere.
However, most, if not all, devs are not qualified to audit their own creations, especially when privacy and security are a must.
This is why specialized audits done by a team of professionals are not only expensive, but important. Just because an encryption scheme has been audited does not mean your implementation of it has.
Once you commission and pass a rigorous third-party security audit, then your comparisons to other privacy messengers who have, will carry more weight.
Until then, it looks promising, and I look forward to seeing where it goes, but do not and can not advise anyone to use Keychat or any other privacy and security services for anything where privacy is a must until it has passed an independent security audit.
This is not just me, but basic practice in the privacy space before recommending services that claim to protect user security and/or privacy.
Keep up the good work! I am excited to see where this goes.
thanks for the insights!
I use Simplex and I liked the no 'IDs' design to eliminate any metadata collection. However after reading this post, in theory I think Keychat's design may just work better.
Better model to monetise and stay sustainable via ecash stamps while still preserving user privacy
ok... question, how would you know who's bob and who's alice and how would they know each other? is it, i'm assuming, to meet up someone in a public square (digital or physical) and connect through a new address from the seed? (and in terms of restoring the seed account on a new device, like in bitcoin, it would scan your seed addresses to certain limits to find if there is chat messages sent or received between people?
SimpleX would say this better protects metadata privacy because there’s no ability to correlate from “account” (Alice’s one time sending address) to Alice’s ID. SimpleX doesn’t have the latter.
If I understand correctly, keychat also has 10 sending addresses for 10 friends, you just add the ability to correlate those 10 to an ID.
Just trying to understand.
How does a new user onboard some cashu sats?
SimpleX also has separate sending and receiving addresses. That's why it's called simplex: 

GeeksforGeeks
Transmission Modes - GeeksforGeeks
Your All-in-One Learning Portal: GeeksforGeeks is a comprehensive educational platform that empowers learners across domains-spanning computer scie...
When we first heard the name Simplex Chat, we were curious about why it was called that. Later, we understood the explanation given by its founders.
Perhaps we can more accurately say that in Keychat, both the sending address and the receiving address are constantly changing, while in Simplex Chat, both addresses do not update.
I don't believe any messenger that requires the spending of crypto to send every message is ever going to attain mass adoption. It might take off among the niche nostr/crypto audience, but it's never going to be on the level of Telegram or Signal. Requiring crypto is inherently self-limiting.
Ecash is not crypto. It's a minted token backed by anything.
People will choose their preferred mint backed by their preferred money.
They can use Keychat with any money that has a custodian running a Cashu mint. Even a mixture of different assets while we're at it.
It's just that now bitcoin-backed Cashu still dominates.
Very cool, thanks for the detailed explanation. Following your project
Correct, but we still hope that ecash sat becomes the most popular ecash.
Mint could even issue ecash discount coupons and ecash credit.
Wait that’s true? If I could buy stamps with USD, it would certainly be way easier to onboard.
Free attracts spam, which is by definition not sustainable.
Is requiring organizations like signal to self finance by dumping a token on retail, and seeking grants in perpetuity sustainable?
Signal does have a subscriber program. I wonder what percentage of staff and server costs, spam mitigation costs of a signal service are covered by revenue.
A blog post by the Signal Foundation last year described their financial situation, indicating that they have been operating at a loss.


Signal Messenger
Privacy is Priceless, but Signal is Expensive
Signal is the world’s most widely used truly private messaging app, and our cryptographic technologies provide extra layers of privacy beyond the...
Everyone can create a bot on Keychat, such as an exchange bot. Keychat does not differentiate between humans and bots.
Simplex Chat is very popular in the Nostr community; whenever someone posts a note asking which chat app is secure, many people recommend Simplex Chat. We also think Simplex Chat is a great app.
So, many people ask what is the difference between Keychat and Simplex Chat? Is Keychat's security as good as Simplex Chat's? Is it really possible to create a chat app as secure as Simplex Chat on Nostr? Why not just use Simplex Chat? Why reinvent the wheel?
A common misconception in the Nostr community is that Nostr is not suitable for private things.
"Nothing about any of the protocols we’ve developed requires centralization; it’s entirely possible to build a federated Signal Protocol-based messenger, but I no longer believe that it is possible to build a competitive federated messenger at all." — Signal Founder Moxie https://signal.org/blog/the-ecosystem-is-moving%C2%A0
This is because the encryption process is completed on the client side, and relays only pass the encrypted messages.
Keychat and Simplex Chat both use the Signal protocol to encrypt messages, so both meet the following security requirements 1-4:
Anti-Forgery
Anti-Forgery ensures that the sender of a message is verifiable and the message has not been tampered with.
End-to-End Encryption
End-to-end encryption ensures that only the sender and receiver can decrypt and read the message content, protecting it from unauthorized access by servers or other network devices.
Forward Secrecy
Forward secrecy ensures that even if the current key is compromised, historical messages cannot be decrypted, since each message uses a new encryption key, which is deleted after use.
Break-in Recovery
Break-in Recovery ensures that if the current key is compromised, future messages cannot be decrypted, and the system can recover from the attack. This feature is also known as backward secrecy.
Metadata Privacy
Protecting the privacy of communication involves more than just protecting the content of messages; it also includes protecting the identities of the communication parties and other data.
Regarding the fifth point, metadata privacy. The designs of Keychat and Simplex Chat are different.
Simplex’s metadata privacy protection scheme
"Simplex chat is the first messenger without user IDs."
“To deliver messages, instead of user IDs used by all other platforms, SimpleX uses temporary anonymous pairwise identifiers of message queues, separate for each of your connections — there are no long term identifiers.”
“Temporary anonymous pairwise identifiers
SimpleX uses temporary anonymous pairwise addresses and credentials for each user contact or group member.
It allows to deliver messages without user profile identifiers, providing better meta-data privacy than alternatives.”
We can understand this mechanism as, if a Simplex Chat user has 10 friends, they have 10 IDs, using different IDs with different friends?
Keychat’s metadata privacy protection scheme
Current chat applications and email have forgotten that an address is not the same as an ID, treating the ID as the address. Emails and current chat applications send messages as [from: Alice's ID to: Bob's ID]. Regardless of how your geographical address changes, when Alice sends an email to Bob, it’s always [from: Alice's ID to: Bob's ID]. This compromises metadata privacy.
However, letters work differently; they are [from: Alice's current geographical address to: Bob's current geographical address].
Keychat separates the receiving address and sending addresses from the ID, and the receiving address and sending addresses are also different. Keychat messages are [from: Alice's one-time sending address to: Bob's almost one-time receiving address]. This makes it difficult for outsiders and relay administrators to determine who is sending messages to whom.
Which scheme do you think is easier to understand and better protects metadata privacy?
Finally, Keychat also uses ecash sat as a stamp for messages, with relays funded by stamp revenue to sustain operations.
View quoted note →











