
#Amethyst Tricks
How to run a private relay over Tor on Android.
With the latest Amethyst supporting outbox & Tor this is more feasible than ever. Host one of your outbox relays on your phone, totally under your control.
🔹Citrine setup
Go to the settings tab.
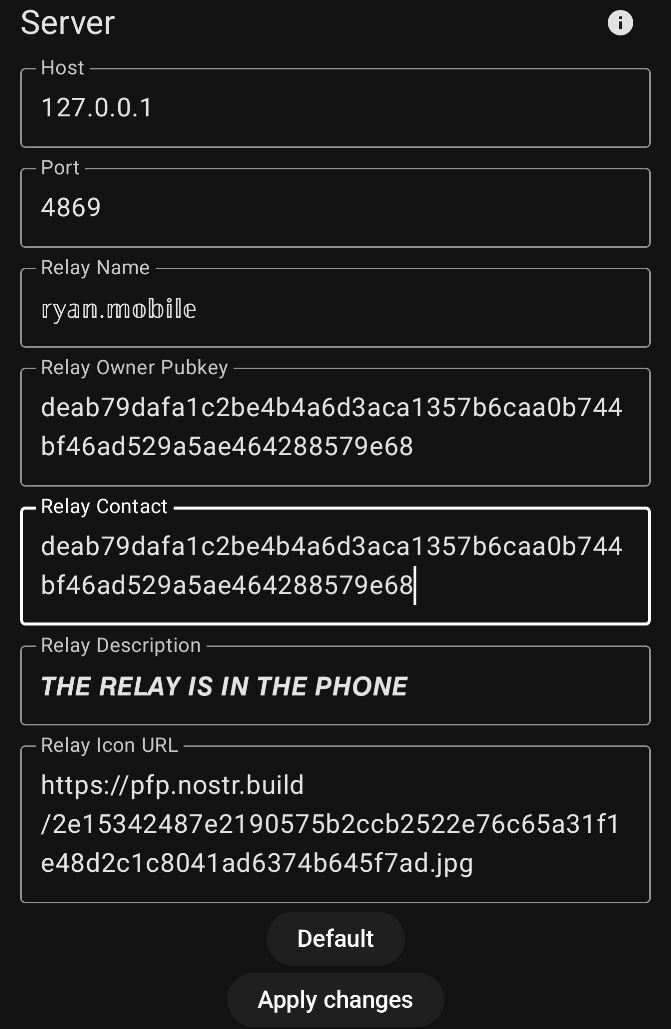
Fill things in as appropriate. Leave the network related settings default.
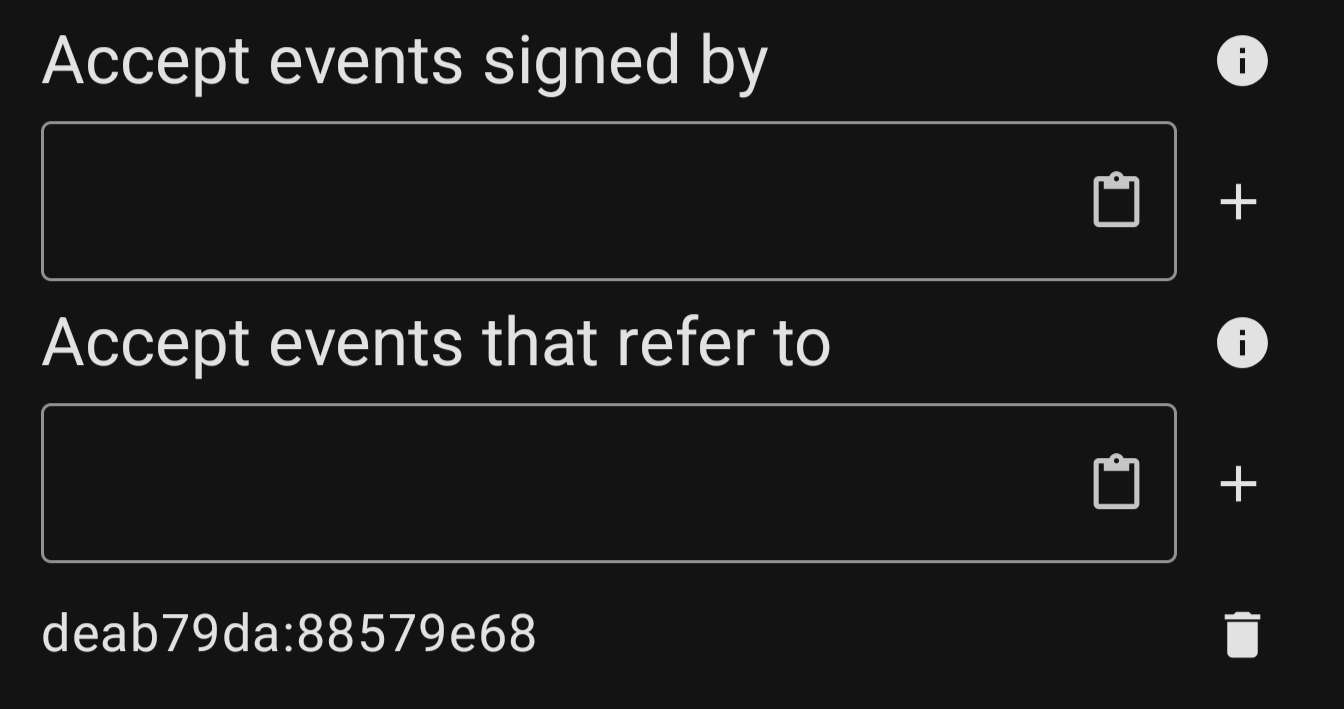
Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
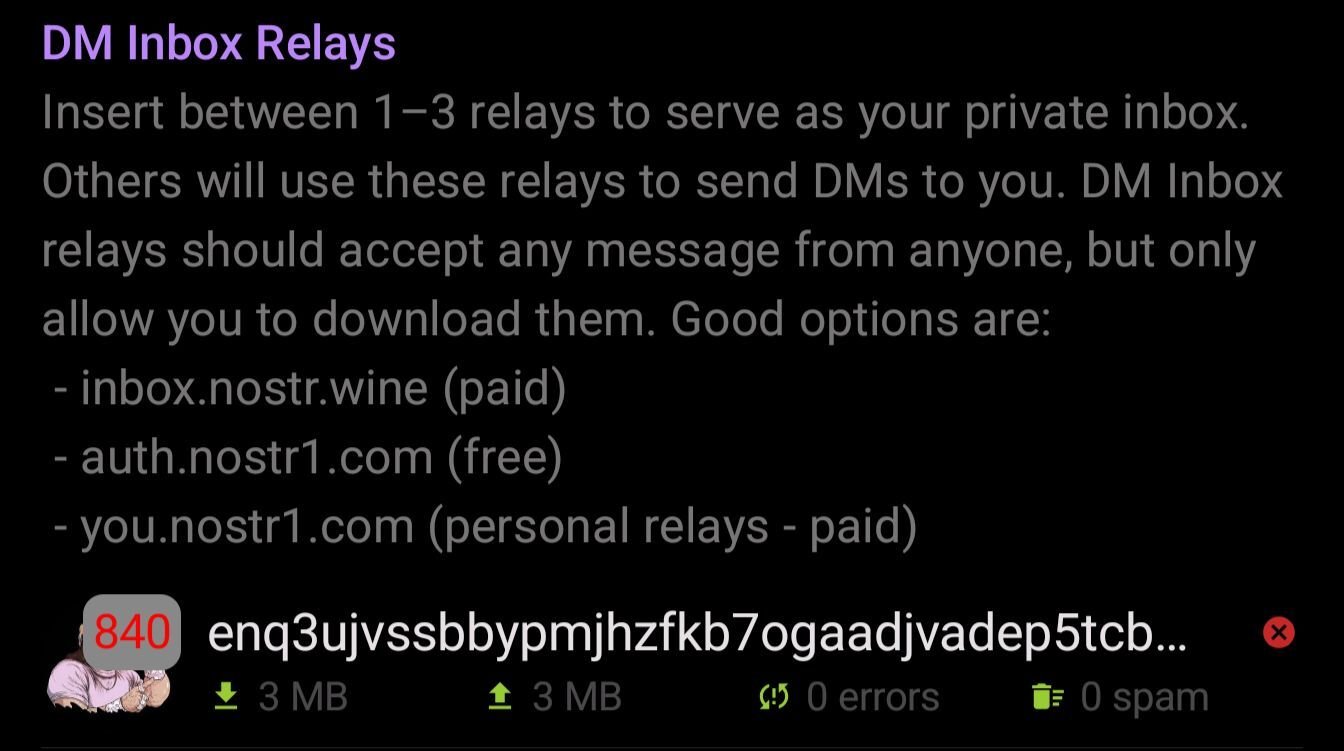
Also add ws://127.0.0.1:4869 as a local relay.
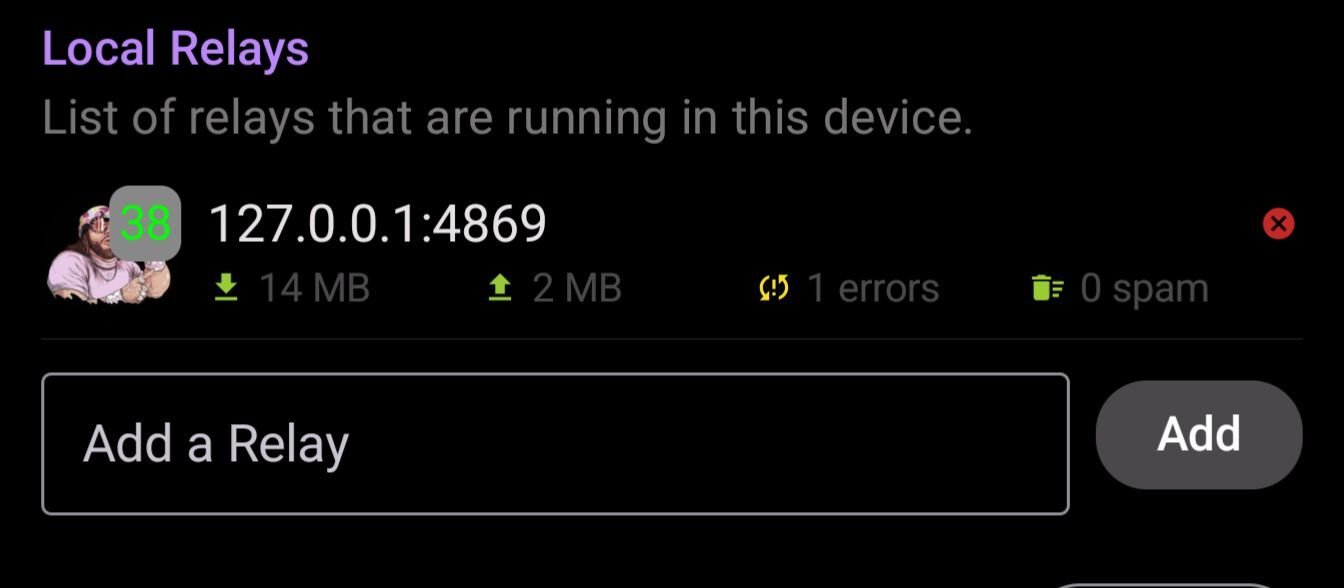
You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
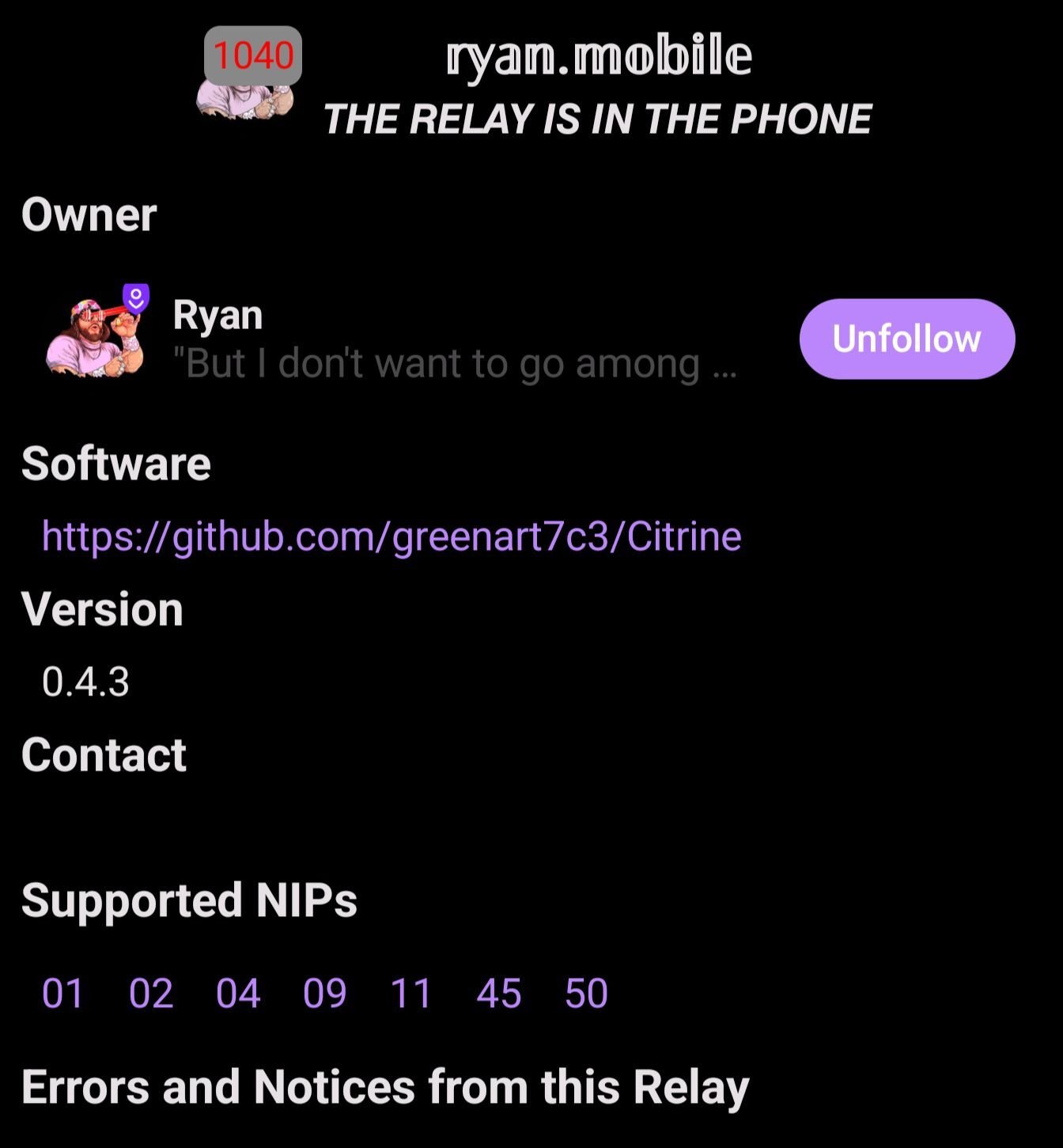
😎👌
Software required

GitHub
GitHub - vitorpamplona/amethyst: Nostr client for Android
Nostr client for Android. Contribute to vitorpamplona/amethyst development by creating an account on GitHub.

GitHub
GitHub - greenart7c3/Citrine: A Nostr relay in your phone
A Nostr relay in your phone. Contribute to greenart7c3/Citrine development by creating an account on GitHub.

GitHub
GitHub - guardianproject/orbot-android: The Github home of Orbot: Tor on Android (Also available on gitlab!)
The Github home of Orbot: Tor on Android (Also available on gitlab!) - guardianproject/orbot-android
Replies (38)
This post is look AI. Too smart
Hey
@node, look what I'm just about to do🥳🥳🥳.
awesome combination🧡
Goodbye Toni 🥲
😂🙋🏻♂️.
I'm not really going to FAFO!
How reliable is Orbot nowadays?
@Vitor Pamplona would be great to have this feature integrated directly in #amethyst instead of relying in #Orbot .
#Amethyst has a very good TOR integration, no need for 3rd TOR apps.
@liminal 🦠 ...do we want kind1s for #ndoc ? I don't know if the long vision encompasses that? Ryan is notoriously & brilliantly educating that way, though. 😅
Oh noooooo 🤣🤣

Bye bye Toni 🤣
We back bitches!
Not sure if the internal tor can run a hosted onion service.
Ryan is too smart!
You should also see in citrine that there are multiple connections in citrine!
i'm still thinking about how I'd go about organizing it, but yes Kind 1's are okay 🫡
Now we just need the ability to self-host relays on I2P or a mesh network and Nostr is tyranny-free.
I like it. Use it too...
And as last step make the onion address known by your friends?
I don't understand 🤔
So you run a nostr relay on your phone, on the same device as your nostr client, but they will connect to each other via Tor? Why would you do that?
Or maybe the primary motivation is to allow other people - your followers specifically - to connect via Tor?
Does that mean that I should keep my phone connected all the time, in order that my relay remain accessible all the time?
I'd like to run such a relay on my Raspberry Pi. Any tips?
That's what setting it as your outbox does.
Just set up my zap ⚡ feel free to test it!
@akiI'm also trying to figure this out. 😂🤷🏻♀️
It's not clear to me, what I can do with this, that is more than using a localhost address. Can people reach my phone over tor?
@Finrod Felagund @ChipTuner is this a security risk?
Yes. You can host your Citrine relay over Tor from your phone, so others can access your notes.
First impression is that it poses no more risk than running a normal relay on your phone and exposing it to the web. And it inherits any possible security risks in the relay code itself.
I don't see the utility for it. Why go through the hassle ? Why host a relay on your phone ? Just why ?
At least, conceptually. I have no idea if the implementation itself introduces new risks. I wouldn't bother with it.
I host one on my phone, that fetches notes from my frens and allows me to read and write notes on the train (spotty Internet).
But I don't see the use case for exposing it to some wider network. That would raise the load in the phone, after all.
You're right. This local relay you're hosting has an assisting function. Anything beyond that for phone relays seems like an overkill.
I entirely agree on this one. I'm someone who likes explicit control over my firewall and incoming/outgoing connections. I wouldn't want to be connecting to a bunch of random servers (relays), you never know which ones could poison your device. One buffer overflow in the client code (meaning the websocket client library or parsing code itself) and you have a RCE vulnerability. The same goes for incoming connections. I assume there is a localhost optimization.
One could setup a malicious relay could be built to trigger a known RCE vuln and every nostr client with the vuln would be pwned XD
For example, in my dream world, noscrypt becomes ubiquitous, there is an overflow somewhere that can be triggered by a malicious relay connection, now all nostr users running noscrypt are pwned simply by connecting to that relay. Same could be said for NDK, or aedile or any framework with a known vuln.
This reminds me of the 7zip vulnerability discovered a year ago which is caused by an integer underflow of all things.
That was a good one
It became a running gag at work.
Wait, what was the gag?
Without getting into details, we were somewhat impacted by this vulnerability. Every time there was a problem because of an overflow or underflow issues, someone would joke that we're endangering national security for example.
I see XD
You lack imagination.
You could run an old Android phone as a cheap & easy self hosted relay.
Self hosted DMs over Tor, leaving no trace of your messages on large relays.
Android is transitioning to be a desktop OS as well, making the power issues of phone use less of an issue. It's basically the same as nostr-relay-tray with the proxy settings enabled. I've been running that for a few days as well, it makes a fine outbox relay.
 Fill things in as appropriate. Leave the network related settings default.
Fill things in as appropriate. Leave the network related settings default.
 Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
 Also add ws://127.0.0.1:4869 as a local relay.
Also add ws://127.0.0.1:4869 as a local relay.
 You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
 😎👌
Software required
😎👌
Software required



 Fill things in as appropriate. Leave the network related settings default.
Fill things in as appropriate. Leave the network related settings default.
 Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
Under "Accept events that refer to" add your npub. This will keep extraneous events from clogging your relay, but still allow DM to function. Note: If you add your npub to "Accept events signed by" your DM partner will not be able to send messages to your relay. You would need to add their npub as well. Maybe a security feature?
🔹Orbot setup
In orbot got to more > hosted onion services.
Add a new service.
Citrine uses port 4869, so set that for both ports. Name it anything. "Nostr" will do.
You will need to restart orbot after you save.
Then you can go back and copy your onion service address. You'll need it for the next step.
🔹Amethyst Setup
Add ws://ONIONADDRESS:4869 as Outbox and DM relays in Amethyst.
 Also add ws://127.0.0.1:4869 as a local relay.
Also add ws://127.0.0.1:4869 as a local relay.
 You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
You should be able to check the relay info in Amethyst by clicking on the icon. It should now reflect what you have set in Citrine!
 😎👌
Software required
😎👌
Software required



















