Privacy Features of Popular Messengers
In the world of secure messaging, not all apps are created equal. Let's take a look at the privacy features of SimpleX, Signal, Session, and Threema.
1
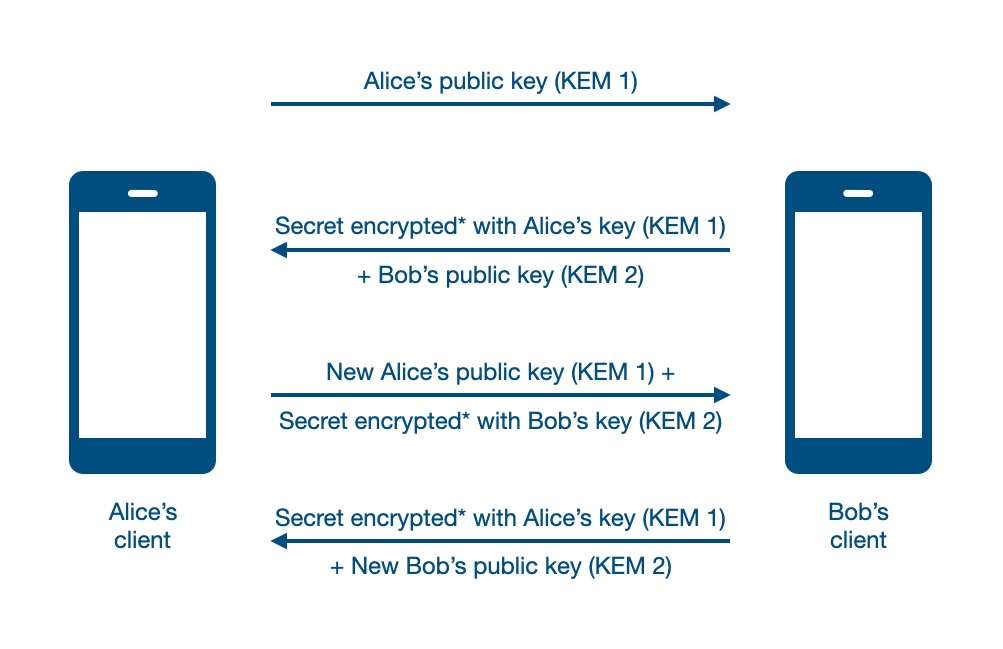
SimpleX
- Fully decentralized with no central servers.
- No phone number or email required.
- Minimal metadata collected.
- Strong anonymity with no user identifiers.
- Users can run their own servers.
- Focused on privacy.
2
Signal
- Strong end-to-end encryption.
- Requires a phone number (less anonymous).
- Collects some metadata (e.g., contact discovery).
- Centralized, with servers controlled by Signal Foundation.
- Widely adopted, with a balance between privacy and usability.
3
Session
- Decentralized and uses Onion routing (Tor) for added anonymity.
- No phone number or email required.
- Minimal metadata.
- User IDs are public keys, providing strong anonymity.
- Open-source community servers, users can run their own nodes.
4
Threema
- End-to-end encryption, but partially open source.
- No phone number required, can use an anonymous ID.
- Some metadata is collected, but it's limited.
- Centralized, with servers controlled by Threema GmbH.
- Requires a one-time fee, but offers robust privacy features.
Conclusion
SimpleX for decentralization & privacy purists.
Signal for strong encryption with a user-friendly experience.
Session for anonymity-focused users.
Threema for those wanting privacy with an anonymous ID system.







 aps ⚡ (and MANY thanks for this content, good one)
aps ⚡ (and MANY thanks for this content, good one)

 Source:
Source: