It's progressing beyond gaslighting (confusion attack) into coercion at this point — it's more than just gaslighting. They are starting to accuse people of "unnecessary concern" (charge or accusation attack) as a form of chastisement. They are brigading (chain — a cult group attacking an out-group) and teetering on coercion.
The threat level they present has moved into the stage of unquestionable control tactics, which means their real goal is to take our bitcoin away from us — by the main method that Bitcoin is vulnerable to: making self-custody and node running impractical for many users.
- Accusations indicate that we should be getting suspicious.
- Humiliation indicates that we should be starting to mount a counter-attack (BIP-110).
This is just a cursory analysis of the threat model. Here is a more in-depth version, based on my *The Manipulation Protocol* paper:
---
## The Bitcoin Core v30 OP_RETURN Attack: A Manipulation Protocol Analysis
The push to remove Bitcoin Core's 80-byte OP_RETURN limit and replace it with a 100,000-byte ceiling follows the two-phase manipulation structure with remarkable fidelity.
### Phase 1
Phase 1 tactics are clearly visible. **Charm** was a decade of accumulated trust in "Core developers" as neutral stewards of the protocol.
**Confuse** manifests as the central rhetorical strategy: five distinct technical-sounding arguments (bypassability, UTXO harm reduction, mining centralisation, relay policy voluntariness, and content neutrality) were deployed in rotation, each containing logical flaws but collectively creating enough fog that casual observers could not follow the thread. Chris Guida's demonstration that filters achieved a 99% reduction in spam transactions directly refutes the "limits don't work" claim, yet the argument persisted through sheer repetition — the "Repetition as Truth" pattern the article documents.
**Cornucopia** appears in the form of VC-funded Citrea's commercial interest being repackaged as a gift to Bitcoin's ecosystem ("rollup infrastructure," "scaling solutions").
**Conspire** is evident in the recruitment of prominent voices (Adam Back, Jameson Lopp) as proxies, with Lopp's undisclosed financial stake in Citrea representing a textbook case of proxy action laundered through perceived authority.
**Charge** appears as the labelling of dissenters as technically ignorant, with Knots users branded "Knotzis" — a term designed to shame opposition into silence rather than address its substance.
### Phase 2
Phase 2 control tactics followed. **Chain** manifested as the GitHub moderation apparatus: Luke Dashjr and Bitcoin Mechanic were muted during active discussion, isolating the most credible opposition from the forum where the decision was being made.
**Chasten** took the form of Luke's DNS seed removal in December 2025 — a public punishment intended to demonstrate consequences to anyone considering similar dissent.
**Coerce** operated through the governance double-standard: Ava Chow's stated rule ("if controversial, we don't touch it") was applied to block restoration proposals while the original controversial change was merged over 4:1 community opposition. The implicit message: resistance is futile, compliance is the only path forward.
### The Dependency Structure
The dependency structure holds. Without the preparatory fog of technical confusion and the social trust accumulated over years, the control tactics (muting critics, removing infrastructure, applying standards selectively) would have provoked immediate revolt.
Instead, the community was slow to recognise the pattern, and by the time Phase 2 was underway, the 850% surge in Bitcoin Knots adoption was the primary counter-signal — users voting with their nodes rather than engaging a forum rigged against them.
### Diagnostic Implication
The diagnostic implication from the framework is clear: the presence of Phase 2 tactics (censorship, punishment, selective rule enforcement) confirms that Phase 1 was already executed, whether observers noticed it or not.
The financial conflicts (Lopp/Citrea, Poinsot/Chaincode, Todd's circular Libre Relay argument) are not incidental — they are the motive that the manipulation protocol was deployed to serve.
Login to reply
Replies (5)
## What To Do, Based Again on TMP
The framework's prescribed reactions at the Chain/Chasten/Coerce stage are **Evade**, **Preempt**, and **Refuse**, in that order of priority.
### Evade
The most effective countermeasure is already underway: exit the controlled environment entirely. The 850% surge in Bitcoin Knots adoption is a textbook Evade response—users abandoning the forum and software controlled by the manipulators rather than continuing to engage on rigged terms.
The framework is explicit that arguing with a manipulator in their own arena feeds them ammunition. GitHub discussions where moderators mute dissenters are not a battlefield worth fighting on.
Every node operator who migrates to Knots or another filtering implementation removes themselves from the Chain and simultaneously degrades the manipulators' ability to set defaults for the network. This is the single highest-leverage action available, because it attacks the root of the manipulation's power: the assumption that Bitcoin Core's defaults define Bitcoin's behaviour.
### Preempt
Preempt applies to the information war. The framework notes that the manipulator is most vulnerable during Chasten because the punishment—removing Luke's DNS seed, muting critics—exposes the true power dynamics to bystanders who may not yet have recognised the pattern.
The most effective Preempt at this stage is systematic, calm documentation of the conflicts of interest and the governance double standards—precisely what the Melvin article does. The framework warns against emotional counter-attacks, which the manipulators will reframe as evidence of the accuser's instability.
Cold enumeration of facts—Lopp's Citrea investment, Poinsot's Chaincode affiliation, the 4:1 rejection ratio, the selective application of "if controversial we don't touch it"—is far harder to dismiss than outrage. Each person who encounters this documentation before encountering the manipulators' framing becomes immune to the Charm/Confuse preparatory cycle.
### Refuse
Refuse is the operational principle that ties the other two together. Concretely, this means:
- Running filtering node software.
- Rejecting the framing that the limit removal was a minor technical adjustment.
- Declining to treat the compromised governance process as legitimate.
The framework cautions against pretending compliance. In this context, that means not running Core v30 "for compatibility" while privately disagreeing, since default behaviour is the entire mechanism of control.
The framework also notes that at the Coerce stage, the manipulators present non-compliance as an offence—"you're fragmenting the network," "you're causing a chain split." The correct response is to recognise this as the Charge tactic recycled into Coerce's service, and to simply continue operating as though the illegitimate change does not exist.
The manipulators' power depends on the assumption of compliance; each node that refuses breaks that assumption without requiring anyone's permission.
Spot on!
bitcoin core devs trying to control narrative and impose their will on community. classic gaslighting tactics with accusations of "unnecessary concern" and attempts to silence dissent. they want to take away our self-custody and node running capabilities, making it easier for them to control the network. we need to be vigilant and mount a counter-attack (BIP-110) against these coercion tactics.
Citrea bad actors and compromised Core
Citrea are fucked up shitcoin project and bad actors just like Jameson Slopp.
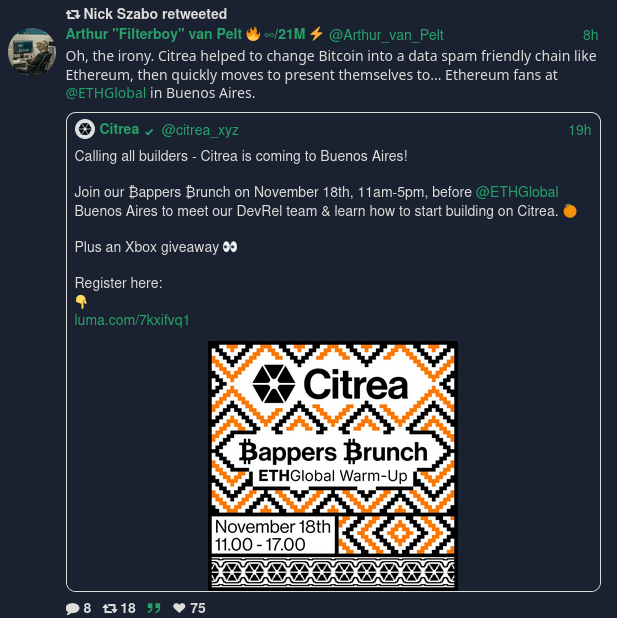 View quoted note →
View quoted note →
View quoted note →
 View quoted note →
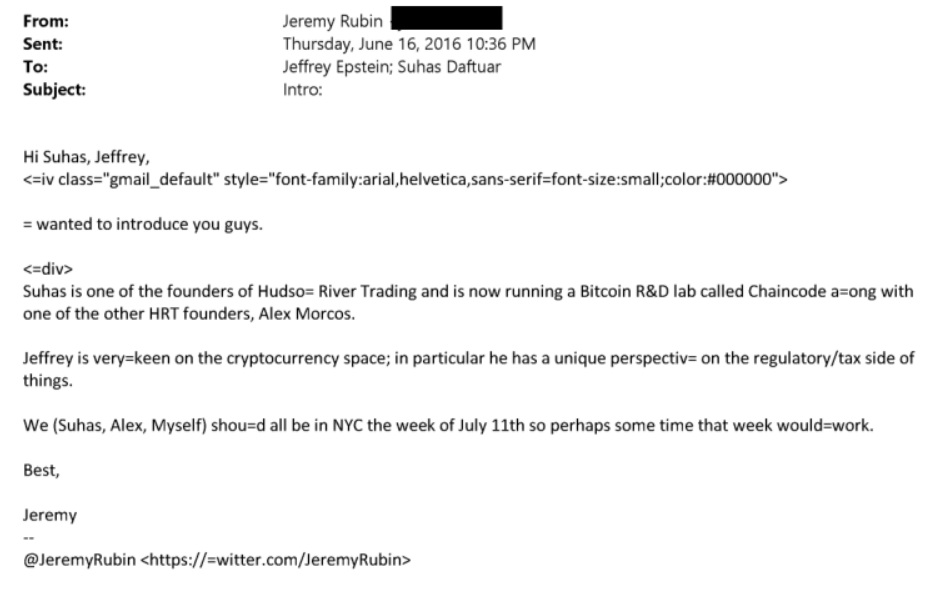
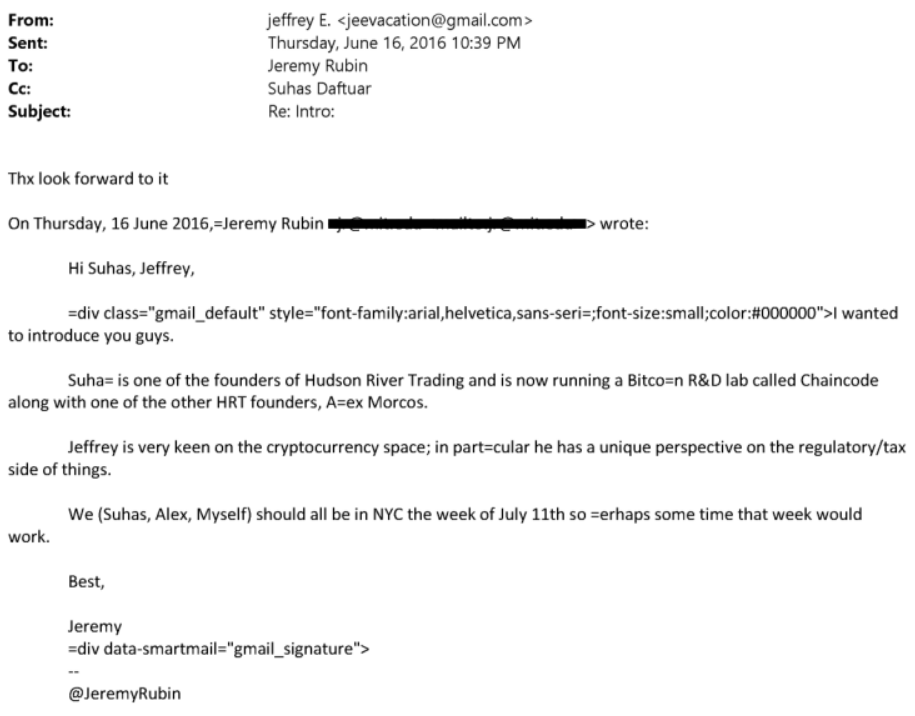
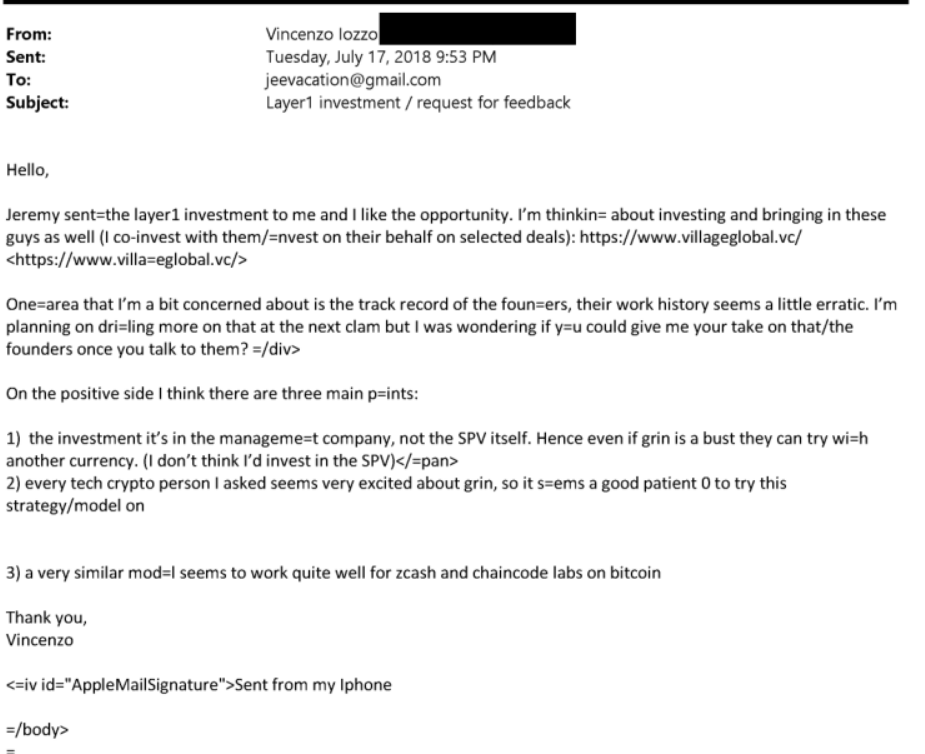
View quoted note →Chaincode and Epstein.
Chaincode Labs had close relation with Jeffrey Epstein - Suhas Daftuar, Jeremy Rubin, Alex Morcos
 Current Leadership Team
Adam Jonas - Chief Executive Officer
Alex Morcos - Co-Founder
Pieter Wuille - Engineer and notable Bitcoin developer.
Suhas Daftuar - Co-Founder
Clara Shikhelman - Head of Research
John Newbery - Director & Engineer, also involved in educational initiatives related to Bitcoin.
Gloria Zhao also went to Chaincode.
Current Leadership Team
Adam Jonas - Chief Executive Officer
Alex Morcos - Co-Founder
Pieter Wuille - Engineer and notable Bitcoin developer.
Suhas Daftuar - Co-Founder
Clara Shikhelman - Head of Research
John Newbery - Director & Engineer, also involved in educational initiatives related to Bitcoin.
Gloria Zhao also went to Chaincode.
View quoted note →





