Time to grab a bite of some fresh Bitcoin tech flavors 🍕:
- Major revision to BIP 360 introduces a new output type to mitigate quantum threats
- A minimal new introspection primitive as a potentially simple quantum-safe upgrade
- A standardized and extensible P2P feature negotiation mechanism
- Bitcoin optech's 2025 year-in-review special
- Taproot assets v0.7: static reusable addresses, auditable supply, and optimized large lightning payments
- UPLC programming language conference, spotlighting Cardano languages and smart contract tooling
- BOB reduces BitVM3 on-chain costs to roughly $10
- SLH-DSA hardware performance evaluation: slow signing but competitive verification, suitable for long-term security
EN: naddr1qvzqqqr4gupzq046tm6pkgrtr4y73vd7wfqa06k4mkrmwdexrknycw7quf637gawqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgawaehxw309ahx7um5wgknqv3w09skk6tgdahxuefwvdhk6tcqz4697et8gdpxx56vwfx82wrywp28v3twwv6sgs3fsp
CN: naddr1qvzqqqr4gupzq046tm6pkgrtr4y73vd7wfqa06k4mkrmwdexrknycw7quf637gawqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgawaehxw309ahx7um5wgknqv3w09skk6tgdahxuefwvdhk6tcqz4chgn23wdv9j4enxary242gwdunxd2d2acqhvlmnt

Cryptape
cryptape@iris.to
npub186a9...hd06
🏗️ A team of blockchain devs & cryptographic researchers building secure, open, and censorship-resistant infrastructure on Nervos Network: nervos.org
🌐 See decentralization in action: nodes.ckb.dev
#blockchain | #opensource | #web5 | #dweb
The Meepo hard fork strengthens CKB-VM in key ways, making it safer, more reliable, and ready for more capable dApps. 🛠️
Here's what we addressed:
✓ Nervos DAO occupied capacity vulnerability
✓ Error code handling in memory protection
✓ ELF loading edge case
✓ x0 register overwrite in macro-operation fusion
A big thanks to community member phroi for reporting the DAO vulnerability—your contribution made this fix possible. 🙏
We're committed to listening, involving, and strengthening CKB together, and we're always happy to share more about our work with the community.
Read the full article 👇 View article →
🍨 Another week, another Satoshi Scoop! Here’s your round-up of the latest flavors from Bitcoin and beyond.
- Sharing block templates to bridge divergent mempools
- A decade in the making: Simplicity powers a programmable Bitcoin future @Blockstream
- Starkware: building STARKS in Simplicity
- Bitle: solar-powered relay node for Bitchat
- PayPerQ: pay-per-query chatbot via Lightning payments
- Alby: building conditional payment logic into apps @Alby
- Bitcoin-MCP: creating AI agents with Lightning Network access
- FPPS mining unsustainable? A decentralization turning point for Bitcoin?
- Emergency upgrade and multisig mechanisms in BitVM bridges
- Fairgate launches FLEX: garbled-circuit fraud prevention for Bitcoin bridges
- Alpen Labs launches EVM-compatible BitVM testnet
EN:  CN:
CN: 


Yakihonne
Cryptape
🏗️ A team of blockchain devs & cryptographic researchers building secure, open, and censorship-resistant infrastructure on Nervos Network: ner...

Yakihonne
Yakihonne |
N/A

🍦Scoop up! The latest Satoshi Scoop weekly brings:
- Bitcoin's post-quantum migration: a phased upgrade proposal by @`Jameson Lopp`
- POAR proposal: reclaiming long-lost bitcoins to extend miner rewards
- Report: comparing four major Bitcoin full nodes by @`1A1z`
- Bitchat: bluetooth-based P2P messaging @`jack`
- Exploring three uses of zero-knowledge proofs in Bitcoin
- Building watchtower-efficient Bitcoin payment channels with BitVMX
- Alpen labs' Glock: cuts on-chain cost of verifying off-chain computation 1000x
- AnchorWatch launches Bitcoin inheritance vaults
- U.S. lawmakers approve three major digital asset bills
- Why the CLARITY Act matters
- Bitcoin: financial lifeline for global refugees
- Bitcoin mining in space: Intercosmic Energy's low-earth orbit initiative
Full scoop
EN: https://yakihonne.com/naddr1qvzqqqr4gupzq046tm6pkgrtr4y73vd7wfqa06k4mkrmwdexrknycw7quf637gawqq255vnwdeuk5vmsf499j460dveygjrytpy4yzsfwme
CN: https://yakihonne.com/naddr1qvzqqqr4gupzq046tm6pkgrtr4y73vd7wfqa06k4mkrmwdexrknycw7quf637gawqq24qd2twpyy7nr4gf2n2uejd4v95kzvw9mnzq6553m


Fork Smarter, Not Harder: CKB's Forking Philosophy Explained
1/ In most blockchains, hardforks often imply discontinuity, where:
😕 Users risk losing access to assets.
🤨 Developers are forced to upgrade—like it or not.
CKB takes a different approach: it decouples upgradeability from forced consensus.
🔐 Assets remain safe during upgrades.
⛓️ Users aren't forced to adopt new protocols.
 Here's how it works:
2/ Protocol-Level Flexibility: Fork Without Split
CKB is built on the UTXO Cell model, where each user's assets are stored in the discrete Cells—each with its own versioned Lock Script.
After a hardfork, each Cell continues to use the VM version it was deployed with, where:
- Existing Cells remain on the old VM version.
- Users are not forced to upgrade the Scripts.
- They opt in new features — if and when they want to.
This is made possible by introducing multiple hash_type variants (type, data, data1, data2, ...), each pointing to a different version of the code.
🤝 Multiple versions of Scripts and VMs coexist on the same chain.
⛓️ Upgrades won't split the network.
🔐 Users keep full control over both the assets, and the rules that govern them as well.
3/ Why It Matters 💡
Most chains treat a hardfork as a reset — override old logic and force everyone to upgrade.
CKB avoids this.
Multiple versions run side by side on the same chain. This eliminates the tension between network evolution and asset preservation.
4/ Script-Level Upgrade Workflow: Type ID + Lock Script
CKB provides Type ID + Lock Script model for managing script upgrades:
1️⃣ Initial Deployment: A Script developer deploys Scripts with upgrade plans in mind: Using Type ID to assign a stable identity but allows future updates.
2️⃣ Iterative Upgrade: Fix bugs, add new features, and change rules—the deployed code may undergo several upgrades using Type ID.
3️⃣ Code Freezing: At any point, one can freeze the code by modifying the Lock Script to be immutable.
5/ Script Developer & dApp Developer: Separate Roles
CKB separates two responsibilities:
- Script Developers: Deploy the Script and decide if it is upgradeable, via Type ID + Lock Script.
- dApp Developers: Choose how to reference a Script in their applications—fixed or upgradable.
Their options:
🔹Reference by type hash → Auto-follow the latest upgrades
🔹Reference by data / data1 / data2 hash → Stay fixed to the trusted version, ignoring the new one
Either way, dApp devs don't need to fear upstream changes breaking their logic or being kicked out of the network.
6/
This separation enables:
- Reusable Scripts across multiple dApps
- Opt-in upgrades — no forced coordination
- Long-term stability where needed, flexibility where desired
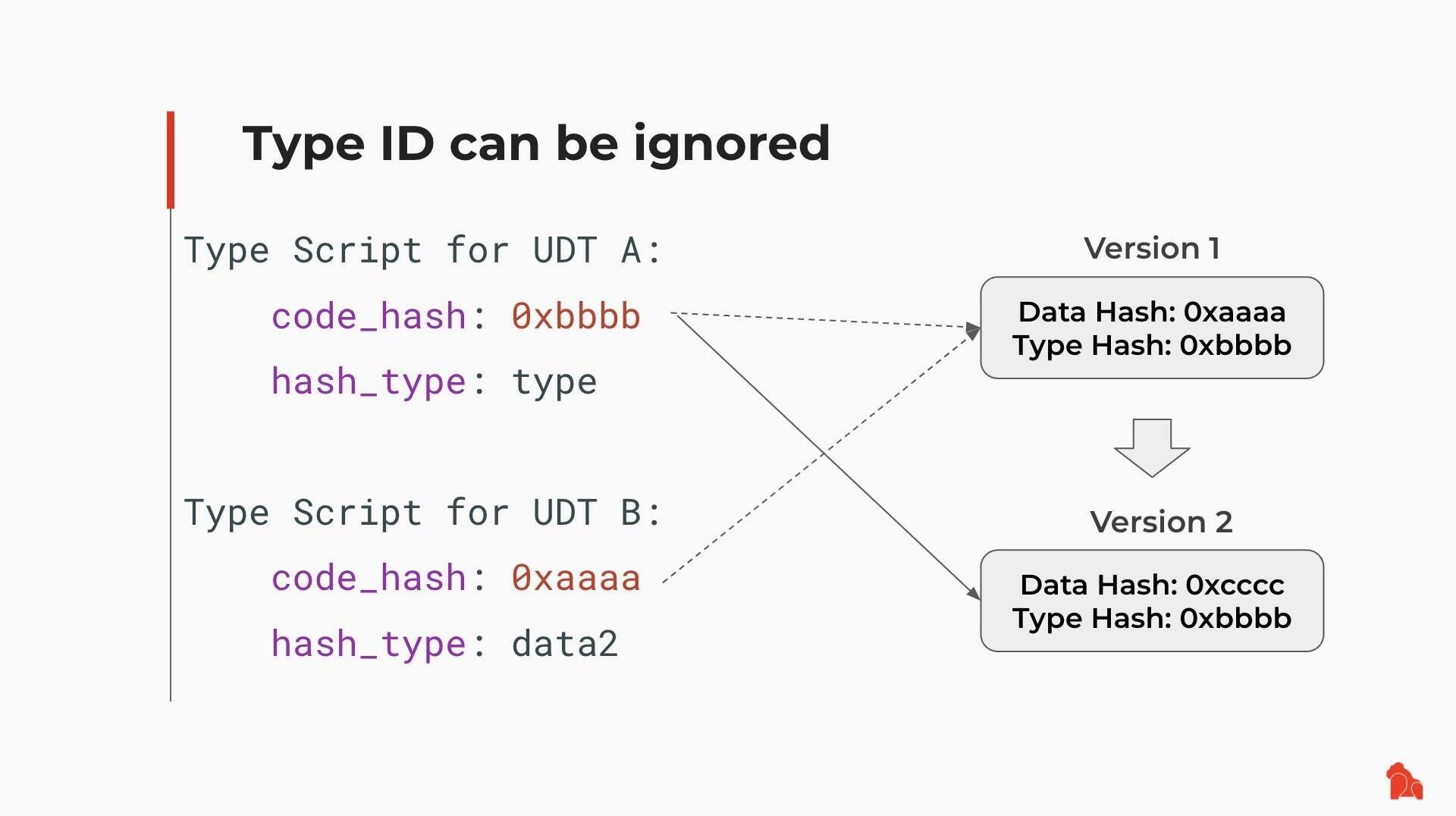
7/ Example: UDT Script Upgrade
Suppose someone deployed a UDT (User-Defined Token) Script using Type ID and created two tokens:
- UDT A uses type as hash_type
- UDT B uses data2 as hash_type
Later, the UDT Script is upgraded from Version 1 to Version 2:
- UDT A automatically adopts Version 2
- UDT B keeps running on Version 1
Here's how it works:
2/ Protocol-Level Flexibility: Fork Without Split
CKB is built on the UTXO Cell model, where each user's assets are stored in the discrete Cells—each with its own versioned Lock Script.
After a hardfork, each Cell continues to use the VM version it was deployed with, where:
- Existing Cells remain on the old VM version.
- Users are not forced to upgrade the Scripts.
- They opt in new features — if and when they want to.
This is made possible by introducing multiple hash_type variants (type, data, data1, data2, ...), each pointing to a different version of the code.
🤝 Multiple versions of Scripts and VMs coexist on the same chain.
⛓️ Upgrades won't split the network.
🔐 Users keep full control over both the assets, and the rules that govern them as well.
3/ Why It Matters 💡
Most chains treat a hardfork as a reset — override old logic and force everyone to upgrade.
CKB avoids this.
Multiple versions run side by side on the same chain. This eliminates the tension between network evolution and asset preservation.
4/ Script-Level Upgrade Workflow: Type ID + Lock Script
CKB provides Type ID + Lock Script model for managing script upgrades:
1️⃣ Initial Deployment: A Script developer deploys Scripts with upgrade plans in mind: Using Type ID to assign a stable identity but allows future updates.
2️⃣ Iterative Upgrade: Fix bugs, add new features, and change rules—the deployed code may undergo several upgrades using Type ID.
3️⃣ Code Freezing: At any point, one can freeze the code by modifying the Lock Script to be immutable.
5/ Script Developer & dApp Developer: Separate Roles
CKB separates two responsibilities:
- Script Developers: Deploy the Script and decide if it is upgradeable, via Type ID + Lock Script.
- dApp Developers: Choose how to reference a Script in their applications—fixed or upgradable.
Their options:
🔹Reference by type hash → Auto-follow the latest upgrades
🔹Reference by data / data1 / data2 hash → Stay fixed to the trusted version, ignoring the new one
Either way, dApp devs don't need to fear upstream changes breaking their logic or being kicked out of the network.
6/
This separation enables:
- Reusable Scripts across multiple dApps
- Opt-in upgrades — no forced coordination
- Long-term stability where needed, flexibility where desired
7/ Example: UDT Script Upgrade
Suppose someone deployed a UDT (User-Defined Token) Script using Type ID and created two tokens:
- UDT A uses type as hash_type
- UDT B uses data2 as hash_type
Later, the UDT Script is upgraded from Version 1 to Version 2:
- UDT A automatically adopts Version 2
- UDT B keeps running on Version 1
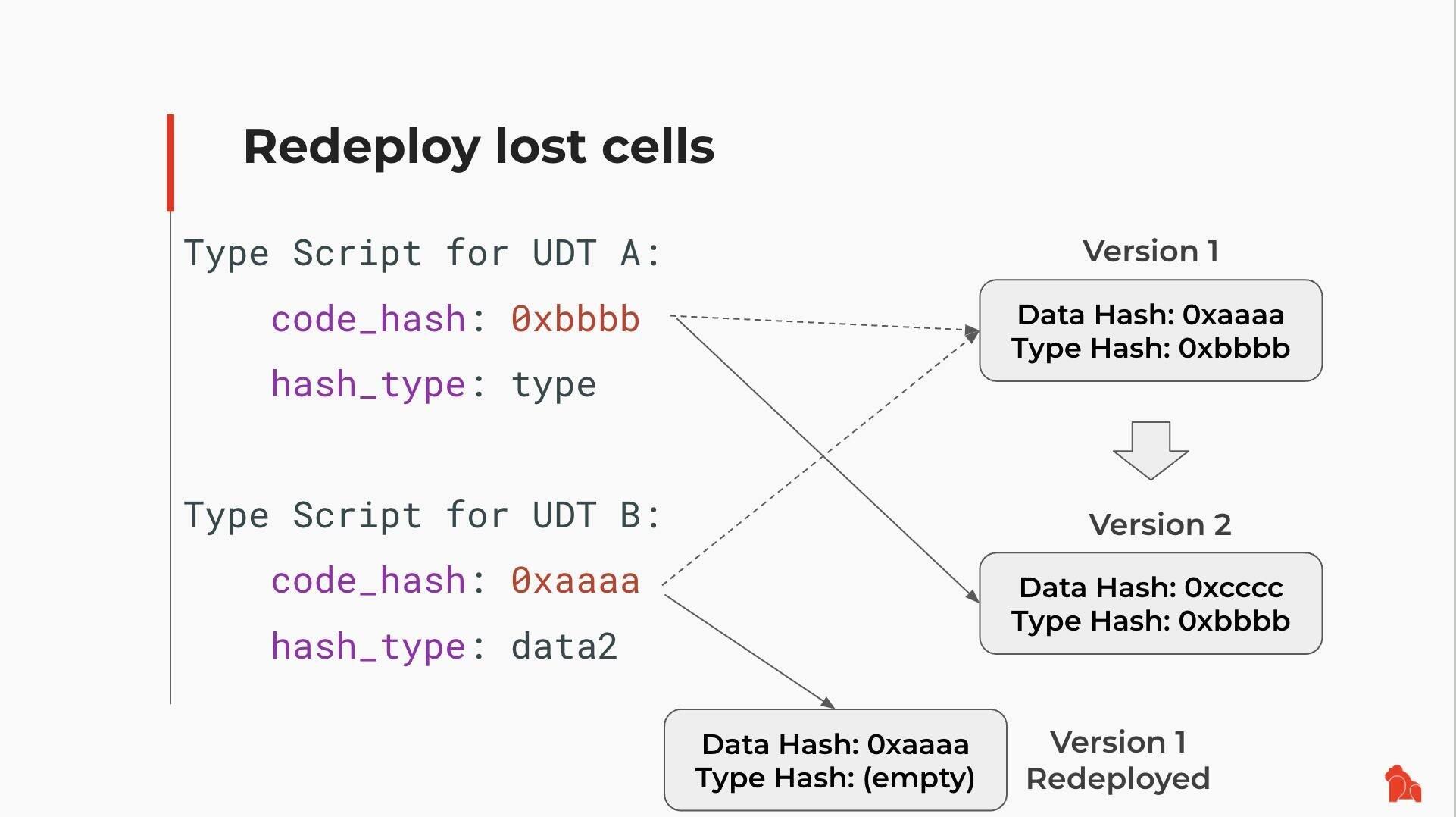
 8/
Even if Version 1 is no longer present in a live Cell, it's not lost.
You can retrieve it from chain history, redeploy it, and use it again.
Old logic remains accessible—by design.
8/
Even if Version 1 is no longer present in a live Cell, it's not lost.
You can retrieve it from chain history, redeploy it, and use it again.
Old logic remains accessible—by design.
 9/ A Better Forking Philosophy
CKB doesn't follow the rigid "hard vs. soft forks" binary. Instead, it offers:
✅ User autonomy
✅ Developer control
Assets stay protected.
Scripts remain stable—or upgradeable.
No one is forced to choose between safety and progress.
It's a better way to fork. And it works.
10/ Reference Links
Rethinking Forks: The Philosophy Behind CKB's Network Upgrade Design:
Recommended Workflow for Script Upgrades:
How CKB Turns User Defined Cryptos Into First-Class Assets:
9/ A Better Forking Philosophy
CKB doesn't follow the rigid "hard vs. soft forks" binary. Instead, it offers:
✅ User autonomy
✅ Developer control
Assets stay protected.
Scripts remain stable—or upgradeable.
No one is forced to choose between safety and progress.
It's a better way to fork. And it works.
10/ Reference Links
Rethinking Forks: The Philosophy Behind CKB's Network Upgrade Design:
Recommended Workflow for Script Upgrades:
How CKB Turns User Defined Cryptos Into First-Class Assets:  CKB, Version Control and Blockchain Evolution:
CKB, Version Control and Blockchain Evolution:  CKB VM Version Selection:
CKB VM Version Selection: 
 Here's how it works:
2/ Protocol-Level Flexibility: Fork Without Split
CKB is built on the UTXO Cell model, where each user's assets are stored in the discrete Cells—each with its own versioned Lock Script.
After a hardfork, each Cell continues to use the VM version it was deployed with, where:
- Existing Cells remain on the old VM version.
- Users are not forced to upgrade the Scripts.
- They opt in new features — if and when they want to.
This is made possible by introducing multiple hash_type variants (type, data, data1, data2, ...), each pointing to a different version of the code.
🤝 Multiple versions of Scripts and VMs coexist on the same chain.
⛓️ Upgrades won't split the network.
🔐 Users keep full control over both the assets, and the rules that govern them as well.
3/ Why It Matters 💡
Most chains treat a hardfork as a reset — override old logic and force everyone to upgrade.
CKB avoids this.
Multiple versions run side by side on the same chain. This eliminates the tension between network evolution and asset preservation.
4/ Script-Level Upgrade Workflow: Type ID + Lock Script
CKB provides Type ID + Lock Script model for managing script upgrades:
1️⃣ Initial Deployment: A Script developer deploys Scripts with upgrade plans in mind: Using Type ID to assign a stable identity but allows future updates.
2️⃣ Iterative Upgrade: Fix bugs, add new features, and change rules—the deployed code may undergo several upgrades using Type ID.
3️⃣ Code Freezing: At any point, one can freeze the code by modifying the Lock Script to be immutable.
5/ Script Developer & dApp Developer: Separate Roles
CKB separates two responsibilities:
- Script Developers: Deploy the Script and decide if it is upgradeable, via Type ID + Lock Script.
- dApp Developers: Choose how to reference a Script in their applications—fixed or upgradable.
Their options:
🔹Reference by type hash → Auto-follow the latest upgrades
🔹Reference by data / data1 / data2 hash → Stay fixed to the trusted version, ignoring the new one
Either way, dApp devs don't need to fear upstream changes breaking their logic or being kicked out of the network.
6/
This separation enables:
- Reusable Scripts across multiple dApps
- Opt-in upgrades — no forced coordination
- Long-term stability where needed, flexibility where desired
7/ Example: UDT Script Upgrade
Suppose someone deployed a UDT (User-Defined Token) Script using Type ID and created two tokens:
- UDT A uses type as hash_type
- UDT B uses data2 as hash_type
Later, the UDT Script is upgraded from Version 1 to Version 2:
- UDT A automatically adopts Version 2
- UDT B keeps running on Version 1
Here's how it works:
2/ Protocol-Level Flexibility: Fork Without Split
CKB is built on the UTXO Cell model, where each user's assets are stored in the discrete Cells—each with its own versioned Lock Script.
After a hardfork, each Cell continues to use the VM version it was deployed with, where:
- Existing Cells remain on the old VM version.
- Users are not forced to upgrade the Scripts.
- They opt in new features — if and when they want to.
This is made possible by introducing multiple hash_type variants (type, data, data1, data2, ...), each pointing to a different version of the code.
🤝 Multiple versions of Scripts and VMs coexist on the same chain.
⛓️ Upgrades won't split the network.
🔐 Users keep full control over both the assets, and the rules that govern them as well.
3/ Why It Matters 💡
Most chains treat a hardfork as a reset — override old logic and force everyone to upgrade.
CKB avoids this.
Multiple versions run side by side on the same chain. This eliminates the tension between network evolution and asset preservation.
4/ Script-Level Upgrade Workflow: Type ID + Lock Script
CKB provides Type ID + Lock Script model for managing script upgrades:
1️⃣ Initial Deployment: A Script developer deploys Scripts with upgrade plans in mind: Using Type ID to assign a stable identity but allows future updates.
2️⃣ Iterative Upgrade: Fix bugs, add new features, and change rules—the deployed code may undergo several upgrades using Type ID.
3️⃣ Code Freezing: At any point, one can freeze the code by modifying the Lock Script to be immutable.
5/ Script Developer & dApp Developer: Separate Roles
CKB separates two responsibilities:
- Script Developers: Deploy the Script and decide if it is upgradeable, via Type ID + Lock Script.
- dApp Developers: Choose how to reference a Script in their applications—fixed or upgradable.
Their options:
🔹Reference by type hash → Auto-follow the latest upgrades
🔹Reference by data / data1 / data2 hash → Stay fixed to the trusted version, ignoring the new one
Either way, dApp devs don't need to fear upstream changes breaking their logic or being kicked out of the network.
6/
This separation enables:
- Reusable Scripts across multiple dApps
- Opt-in upgrades — no forced coordination
- Long-term stability where needed, flexibility where desired
7/ Example: UDT Script Upgrade
Suppose someone deployed a UDT (User-Defined Token) Script using Type ID and created two tokens:
- UDT A uses type as hash_type
- UDT B uses data2 as hash_type
Later, the UDT Script is upgraded from Version 1 to Version 2:
- UDT A automatically adopts Version 2
- UDT B keeps running on Version 1
 8/
Even if Version 1 is no longer present in a live Cell, it's not lost.
You can retrieve it from chain history, redeploy it, and use it again.
Old logic remains accessible—by design.
8/
Even if Version 1 is no longer present in a live Cell, it's not lost.
You can retrieve it from chain history, redeploy it, and use it again.
Old logic remains accessible—by design.
 9/ A Better Forking Philosophy
CKB doesn't follow the rigid "hard vs. soft forks" binary. Instead, it offers:
✅ User autonomy
✅ Developer control
Assets stay protected.
Scripts remain stable—or upgradeable.
No one is forced to choose between safety and progress.
It's a better way to fork. And it works.
10/ Reference Links
Rethinking Forks: The Philosophy Behind CKB's Network Upgrade Design:
9/ A Better Forking Philosophy
CKB doesn't follow the rigid "hard vs. soft forks" binary. Instead, it offers:
✅ User autonomy
✅ Developer control
Assets stay protected.
Scripts remain stable—or upgradeable.
No one is forced to choose between safety and progress.
It's a better way to fork. And it works.
10/ Reference Links
Rethinking Forks: The Philosophy Behind CKB's Network Upgrade Design: Rethinking Forks | Nervos CKB
Originally written by Jan Xie
Upgrade Scripts | Nervos CKB
This article is based on ideas presented in this talk by Xuejie Xiao

Cryptape Jungle
How CKB Turns User Defined Cryptos Into First-Class Assets
Key Takeaways
CKB Cell model is a highly abstract model in blockchain architecture design.
Cell model differs from Bitcoin's UTXO and Ethereum's...

Nervos Talk
CKB, Version Control and Blockchain Evolution
I’m Linus’s fan. This guy created an open-source operating system running everywhere, co-authored a book which is one of my favorites, and buil...
GitHub
rfcs/rfcs/0032-ckb-vm-version-selection/0032-ckb-vm-version-selection.md at master · nervosnetwork/rfcs
This repository contains proposals, standards and documentations related to Nervos Network. - nervosnetwork/rfcs
Fuzzing CKB-VM Into Shape: The Hidden Work Behind Meepo
Do you know that a big part of Meepo’s development time went into fuzzing test, rather than writing new features?
To ensure the reliability and consistency of CKB-VM upgrades on mainnet and testnet, we fuzzed both valid and invalid transactions to catch any subtle compatibility issues early.
The goal was to:
- Ensure stable and consist transaction execution
- Prevent panics
- Verify compatibility in aspects like cycle consumption and error handling across different versions and hardforks
Here’s how fuzzing helped.
 1/ Initial Verification: Transaction Replay 🔁
We began by replaying historical on-chain transactions (via `replay`) from mainnet and testnet to check if `cycle` consumption remained consistent in the upgraded CKB-VM.
This caught several mismatches:
1/ Initial Verification: Transaction Replay 🔁
We began by replaying historical on-chain transactions (via `replay`) from mainnet and testnet to check if `cycle` consumption remained consistent in the upgraded CKB-VM.
This caught several mismatches:
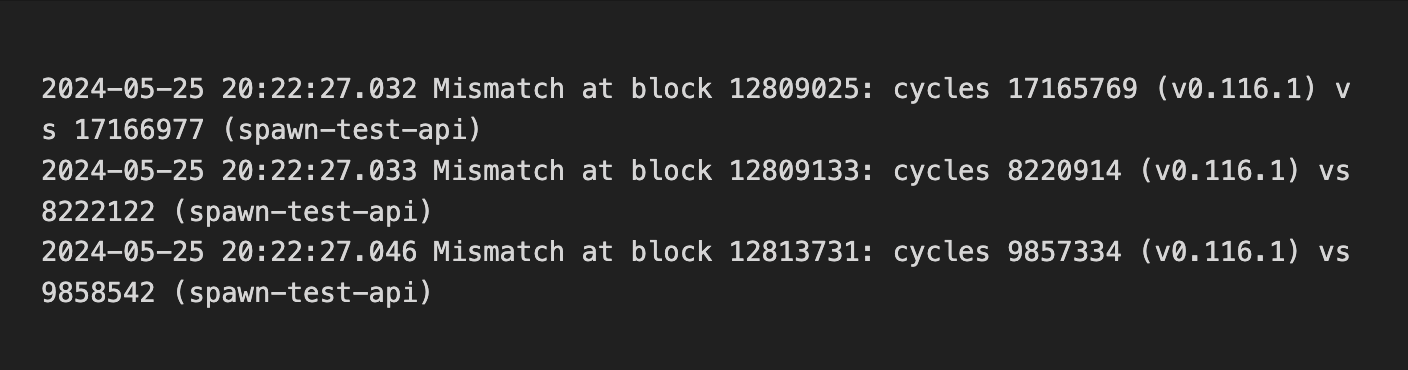 As the chain only contains valid transactions, this method verifies past compatibility but not future cases. To broaden coverage, we turned to fuzzing to simulate diverse transaction inputs and assess compatibility across versions, including error handling in invalid transactions.
2/ First Fuzzing Attempt 🧪
We compared the execution results of `data0` and `data1` of the pre- and post-upgrade VM versions:
As the chain only contains valid transactions, this method verifies past compatibility but not future cases. To broaden coverage, we turned to fuzzing to simulate diverse transaction inputs and assess compatibility across versions, including error handling in invalid transactions.
2/ First Fuzzing Attempt 🧪
We compared the execution results of `data0` and `data1` of the pre- and post-upgrade VM versions:
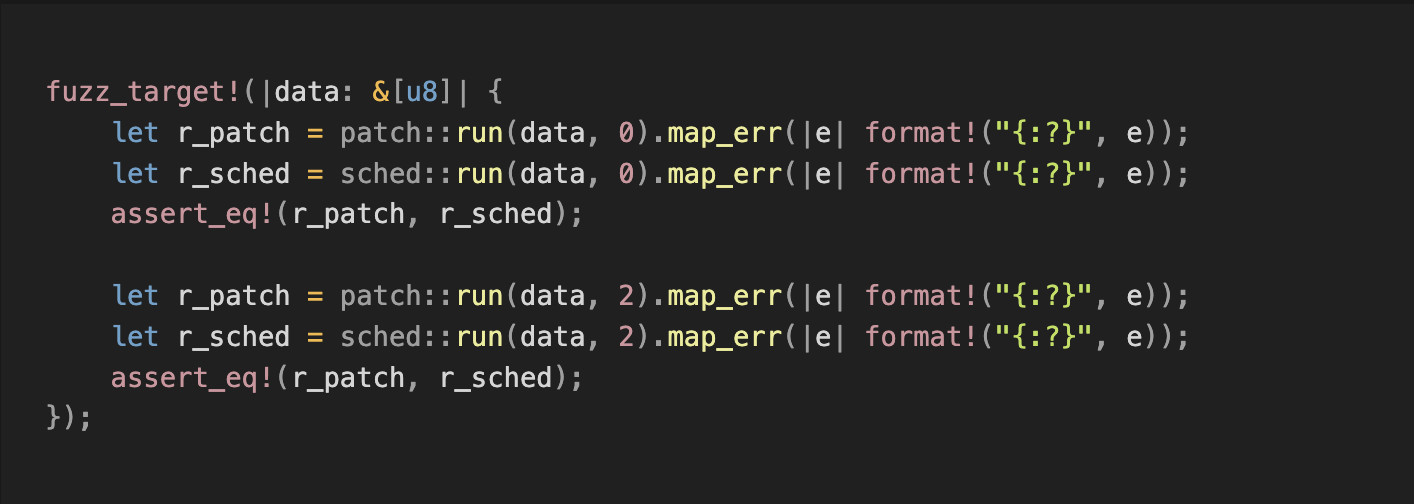 However, most generated test cases were invalid. The test only compared whether the errors matched, but skipped the cycle consumption for valid cases—not enough to meet our goals.
3/ Improved Fuzzing 🔧
To increase valid transaction input coverage, we refined the strategy:
- Corpus Optimization: Added valid transaction data from CKB-VM tests and CKB debugger binaries to the fuzzing corpus.
- Input Filtering: Modified fuzzing logic to only keep valid transactions in the corpus, further increasing the frequency of valid samples and enhancing `cycle` verification.
However, most generated test cases were invalid. The test only compared whether the errors matched, but skipped the cycle consumption for valid cases—not enough to meet our goals.
3/ Improved Fuzzing 🔧
To increase valid transaction input coverage, we refined the strategy:
- Corpus Optimization: Added valid transaction data from CKB-VM tests and CKB debugger binaries to the fuzzing corpus.
- Input Filtering: Modified fuzzing logic to only keep valid transactions in the corpus, further increasing the frequency of valid samples and enhancing `cycle` verification.
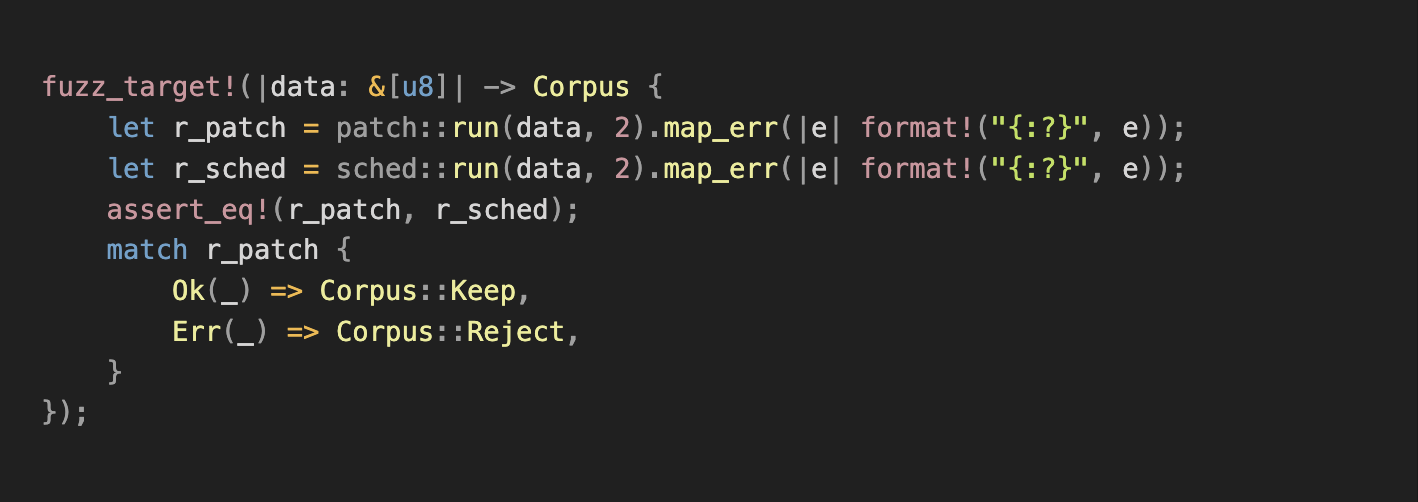 4/ Findings 😃
Improved fuzzing uncovered bugs, including:
- Crash caused by an invalid syscall parameter. Fix: github.com/libraries/ckb/commit/38279e118d3fda3c52f1d47d2062f80e19a2d523
- Instruction reordering led to mismatched `cycle` cost and memory out-of-bounds errors. Fix: github.com/libraries/ckb/commit/ea4aea7fa4cd87ce5df6dee6616466458ff5a86e
- Inconsistent error handling due to mismatched `DataPieceId` behavior. Fix: github.com/libraries/ckb/commit/af87dd355a653eaca19a643866300cc5cd907cf5
- Address truncation in x64. Fix: github.com/nervosnetwork/ckb-vm/commit/f6df535bbf8864fd14684c133b1aa8026a0b0868
- Inconsistencies in memory tracking. Fix: github.com/nervosnetwork/ckb-vm/commit/065a6457d06aa17da4f7dfa1954a2601fc7d288b
All issues were reproduced, analyzed, and added to the test corpus and the fuzzing crash directory for regression testing.
5/ Went Deeper: ISA-Level Fuzzing 🦾
In addition to compatibility testing, we fuzzed the instruction set to prevent unexpected VM panics.
See: github.com/nervosnetwork/ckb-vm-fuzzing-test
6/ Fuzzing isn’t flashy, but it pays off. 🛡️
As we know reliability is what gives developers confidence to build.
We’ll gladly keep things safe and steady—and maybe a little boring—so you don’t have to. 😎
8/ Reference Links 🔗
Fuzzing and tools:
- github.com/nervosnetwork/ckb-vm/tree/develop/fuzz
- github.com/libraries/schedfuzz
- github.com/nervosnetwork/ckb-vm-fuzzing-test
On VM 2:
- github.com/nervosnetwork/rfcs/blob/master/rfcs/0049-ckb-vm-version-2/0049-ckb-vm-version-2.md
4/ Findings 😃
Improved fuzzing uncovered bugs, including:
- Crash caused by an invalid syscall parameter. Fix: github.com/libraries/ckb/commit/38279e118d3fda3c52f1d47d2062f80e19a2d523
- Instruction reordering led to mismatched `cycle` cost and memory out-of-bounds errors. Fix: github.com/libraries/ckb/commit/ea4aea7fa4cd87ce5df6dee6616466458ff5a86e
- Inconsistent error handling due to mismatched `DataPieceId` behavior. Fix: github.com/libraries/ckb/commit/af87dd355a653eaca19a643866300cc5cd907cf5
- Address truncation in x64. Fix: github.com/nervosnetwork/ckb-vm/commit/f6df535bbf8864fd14684c133b1aa8026a0b0868
- Inconsistencies in memory tracking. Fix: github.com/nervosnetwork/ckb-vm/commit/065a6457d06aa17da4f7dfa1954a2601fc7d288b
All issues were reproduced, analyzed, and added to the test corpus and the fuzzing crash directory for regression testing.
5/ Went Deeper: ISA-Level Fuzzing 🦾
In addition to compatibility testing, we fuzzed the instruction set to prevent unexpected VM panics.
See: github.com/nervosnetwork/ckb-vm-fuzzing-test
6/ Fuzzing isn’t flashy, but it pays off. 🛡️
As we know reliability is what gives developers confidence to build.
We’ll gladly keep things safe and steady—and maybe a little boring—so you don’t have to. 😎
8/ Reference Links 🔗
Fuzzing and tools:
- github.com/nervosnetwork/ckb-vm/tree/develop/fuzz
- github.com/libraries/schedfuzz
- github.com/nervosnetwork/ckb-vm-fuzzing-test
On VM 2:
- github.com/nervosnetwork/rfcs/blob/master/rfcs/0049-ckb-vm-version-2/0049-ckb-vm-version-2.md
 1/ Initial Verification: Transaction Replay 🔁
We began by replaying historical on-chain transactions (via `replay`) from mainnet and testnet to check if `cycle` consumption remained consistent in the upgraded CKB-VM.
This caught several mismatches:
1/ Initial Verification: Transaction Replay 🔁
We began by replaying historical on-chain transactions (via `replay`) from mainnet and testnet to check if `cycle` consumption remained consistent in the upgraded CKB-VM.
This caught several mismatches:
 As the chain only contains valid transactions, this method verifies past compatibility but not future cases. To broaden coverage, we turned to fuzzing to simulate diverse transaction inputs and assess compatibility across versions, including error handling in invalid transactions.
2/ First Fuzzing Attempt 🧪
We compared the execution results of `data0` and `data1` of the pre- and post-upgrade VM versions:
As the chain only contains valid transactions, this method verifies past compatibility but not future cases. To broaden coverage, we turned to fuzzing to simulate diverse transaction inputs and assess compatibility across versions, including error handling in invalid transactions.
2/ First Fuzzing Attempt 🧪
We compared the execution results of `data0` and `data1` of the pre- and post-upgrade VM versions:
 However, most generated test cases were invalid. The test only compared whether the errors matched, but skipped the cycle consumption for valid cases—not enough to meet our goals.
3/ Improved Fuzzing 🔧
To increase valid transaction input coverage, we refined the strategy:
- Corpus Optimization: Added valid transaction data from CKB-VM tests and CKB debugger binaries to the fuzzing corpus.
- Input Filtering: Modified fuzzing logic to only keep valid transactions in the corpus, further increasing the frequency of valid samples and enhancing `cycle` verification.
However, most generated test cases were invalid. The test only compared whether the errors matched, but skipped the cycle consumption for valid cases—not enough to meet our goals.
3/ Improved Fuzzing 🔧
To increase valid transaction input coverage, we refined the strategy:
- Corpus Optimization: Added valid transaction data from CKB-VM tests and CKB debugger binaries to the fuzzing corpus.
- Input Filtering: Modified fuzzing logic to only keep valid transactions in the corpus, further increasing the frequency of valid samples and enhancing `cycle` verification.
 4/ Findings 😃
Improved fuzzing uncovered bugs, including:
- Crash caused by an invalid syscall parameter. Fix: github.com/libraries/ckb/commit/38279e118d3fda3c52f1d47d2062f80e19a2d523
- Instruction reordering led to mismatched `cycle` cost and memory out-of-bounds errors. Fix: github.com/libraries/ckb/commit/ea4aea7fa4cd87ce5df6dee6616466458ff5a86e
- Inconsistent error handling due to mismatched `DataPieceId` behavior. Fix: github.com/libraries/ckb/commit/af87dd355a653eaca19a643866300cc5cd907cf5
- Address truncation in x64. Fix: github.com/nervosnetwork/ckb-vm/commit/f6df535bbf8864fd14684c133b1aa8026a0b0868
- Inconsistencies in memory tracking. Fix: github.com/nervosnetwork/ckb-vm/commit/065a6457d06aa17da4f7dfa1954a2601fc7d288b
All issues were reproduced, analyzed, and added to the test corpus and the fuzzing crash directory for regression testing.
5/ Went Deeper: ISA-Level Fuzzing 🦾
In addition to compatibility testing, we fuzzed the instruction set to prevent unexpected VM panics.
See: github.com/nervosnetwork/ckb-vm-fuzzing-test
6/ Fuzzing isn’t flashy, but it pays off. 🛡️
As we know reliability is what gives developers confidence to build.
We’ll gladly keep things safe and steady—and maybe a little boring—so you don’t have to. 😎
8/ Reference Links 🔗
Fuzzing and tools:
- github.com/nervosnetwork/ckb-vm/tree/develop/fuzz
- github.com/libraries/schedfuzz
- github.com/nervosnetwork/ckb-vm-fuzzing-test
On VM 2:
- github.com/nervosnetwork/rfcs/blob/master/rfcs/0049-ckb-vm-version-2/0049-ckb-vm-version-2.md
4/ Findings 😃
Improved fuzzing uncovered bugs, including:
- Crash caused by an invalid syscall parameter. Fix: github.com/libraries/ckb/commit/38279e118d3fda3c52f1d47d2062f80e19a2d523
- Instruction reordering led to mismatched `cycle` cost and memory out-of-bounds errors. Fix: github.com/libraries/ckb/commit/ea4aea7fa4cd87ce5df6dee6616466458ff5a86e
- Inconsistent error handling due to mismatched `DataPieceId` behavior. Fix: github.com/libraries/ckb/commit/af87dd355a653eaca19a643866300cc5cd907cf5
- Address truncation in x64. Fix: github.com/nervosnetwork/ckb-vm/commit/f6df535bbf8864fd14684c133b1aa8026a0b0868
- Inconsistencies in memory tracking. Fix: github.com/nervosnetwork/ckb-vm/commit/065a6457d06aa17da4f7dfa1954a2601fc7d288b
All issues were reproduced, analyzed, and added to the test corpus and the fuzzing crash directory for regression testing.
5/ Went Deeper: ISA-Level Fuzzing 🦾
In addition to compatibility testing, we fuzzed the instruction set to prevent unexpected VM panics.
See: github.com/nervosnetwork/ckb-vm-fuzzing-test
6/ Fuzzing isn’t flashy, but it pays off. 🛡️
As we know reliability is what gives developers confidence to build.
We’ll gladly keep things safe and steady—and maybe a little boring—so you don’t have to. 😎
8/ Reference Links 🔗
Fuzzing and tools:
- github.com/nervosnetwork/ckb-vm/tree/develop/fuzz
- github.com/libraries/schedfuzz
- github.com/nervosnetwork/ckb-vm-fuzzing-test
On VM 2:
- github.com/nervosnetwork/rfcs/blob/master/rfcs/0049-ckb-vm-version-2/0049-ckb-vm-version-2.mdYour fresh dose of updates from the Bitcoin ecosystem is ready! 🍊 Catch up now:  🧡
* Shielded CSV: Private and efficient client-side validation, enhancing Bitcoin privacy at 100 txs/s
* Implementing private offline Lightning Network payments with BOLT12
* UTXOzkp: Proving Lightning channel presence on-chain without revealing specific UTXOs
* Expanding DNS-based payment instruction resolution to identity and data verification via DNS TXT records
* NOIST: A non-interactive, single-round t-of-n threshold signing protocol
* New evidence of mining pool centralization: similar Block templates
* Entering Bitcoin development from a Rust perspective
* Is Babylon’s sustainable yield narrative valid?
* What exactly constitutes client-side validation?
🤹 Other Stuff
* The importance of decoupling product decision-makers from service, as seen from the Telegram founder’s arrest
* Cracking the Onion: how German law enforcement is breaking Tor's anonymity
* A list of privacy-friendly tools covering crypto, desktop, and mobile devices @`mynymbox`
* Are real-world assets (RWAs) a safe haven for on-chain yields?
* Mining heater: enjoy hot coffee while mining Bitcoin
🧡
* Shielded CSV: Private and efficient client-side validation, enhancing Bitcoin privacy at 100 txs/s
* Implementing private offline Lightning Network payments with BOLT12
* UTXOzkp: Proving Lightning channel presence on-chain without revealing specific UTXOs
* Expanding DNS-based payment instruction resolution to identity and data verification via DNS TXT records
* NOIST: A non-interactive, single-round t-of-n threshold signing protocol
* New evidence of mining pool centralization: similar Block templates
* Entering Bitcoin development from a Rust perspective
* Is Babylon’s sustainable yield narrative valid?
* What exactly constitutes client-side validation?
🤹 Other Stuff
* The importance of decoupling product decision-makers from service, as seen from the Telegram founder’s arrest
* Cracking the Onion: how German law enforcement is breaking Tor's anonymity
* A list of privacy-friendly tools covering crypto, desktop, and mobile devices @`mynymbox`
* Are real-world assets (RWAs) a safe haven for on-chain yields?
* Mining heater: enjoy hot coffee while mining Bitcoin

Cryptape Jungle
Satoshi Scoop Weekly, 27 Sep 2024
Take a byte out of the latest weekly updates in the Bitcoin ecosystem. All things
🍽️ Dive into the flavorful Bitcoin ecosystem with the latest Satoshi Scoop. Bon appétit!
🧡 Bitcoin Ecosystem
- Pain Points in BTCFI L2/L1 Development? Why Enhance Contracts via Softfork? @`busyforking`
- Reclaiming the Bitcoin P2P Vision for a Web 5 Future @`CKB DevRel`
- Bitcoin Vaults and the Future of Bitcoin Custody
- Known Attacks on the Nostr protocol @`Ron Stoner`
- UTXO Stack Announces Transition to Lightning Network Staking Layer
- Exploring a New Fungible Token Protocol Using OP_CAT @`Rijndael`
- Enabling Native Tokens on Bitcoin via OP_CAT is Not Ideal
- TMUL Primitive Unlocks More Efficient ZK Verification on Bitcoin
- Permissionless Verifiable Information Dispersal: Data Availability for Bitcoin Rollups
- You Probably Don't Need a Hardware Wallet
🌏 Other Stuff
- 2024 Global Adoption Index
- Trusted Enclaves: Trusted Execution Environments (TEES)
- Introducing Boundless: The Verifiable Compute Layer


Cryptape Jungle
Satoshi Scoop Weekly, 20 Sep 2024
Take a byte out of the latest weekly updates in the Bitcoin ecosystem. All things #POW and #UTXO.
🍴Tuck into the 'Satoshi Scoop Weekly' for a taste of what's cooking in the Bitcoin ecosystem!  - OP_CAT Upgrade: Why Important?
- Rusty Russell on the 'Great Script Restoration' Soft Fork
- Slow is Not a Problem: How SlowFi Fits Into Bitcoin DeFi
- Fiber Network: Lightning Network on CKB
- Bitcoin Ecosystem Evolution Post Babylon Launch and Lorenzo Staking
- Babylon Mainnet: A Catalyst for BTCFI Summer?
- UTXOStack: P2P Economy That Leads a Blockchain Renaissance
- RGB v0.11 Beta 7 Released
- Code Showcase | Paywalled Stock Data API Implemented in Under 100 Lines of Code
- U.S. Treasury and Federal Reserve Redefining 'Money'
- Who is Watching Over You: Uncovering Surveillance Entities
- Germany's Nationwide Raid on Cryptos
- El Salvador Introduces Bitcoin Education and Certification for Civil Servants
- OP_CAT Upgrade: Why Important?
- Rusty Russell on the 'Great Script Restoration' Soft Fork
- Slow is Not a Problem: How SlowFi Fits Into Bitcoin DeFi
- Fiber Network: Lightning Network on CKB
- Bitcoin Ecosystem Evolution Post Babylon Launch and Lorenzo Staking
- Babylon Mainnet: A Catalyst for BTCFI Summer?
- UTXOStack: P2P Economy That Leads a Blockchain Renaissance
- RGB v0.11 Beta 7 Released
- Code Showcase | Paywalled Stock Data API Implemented in Under 100 Lines of Code
- U.S. Treasury and Federal Reserve Redefining 'Money'
- Who is Watching Over You: Uncovering Surveillance Entities
- Germany's Nationwide Raid on Cryptos
- El Salvador Introduces Bitcoin Education and Certification for Civil Servants

Cryptape Jungle
Satoshi Scoop Weekly, 30 Aug 2024
Take a byte out of the latest weekly updates in the Bitcoin ecosystem. All things #POW and #UTXO.