 WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!
WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!
WalletScrutiny
_@WalletScrutiny.com
npub1j9kt...uswx
Know your wallet like you made it!
Our goal is to improve the security of Bitcoin wallets by examining products for transparency and potential attacks.
 WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!
WalletScrutiny turned 6!
We've come a long way over the years. In the beginning, we only looked into Android wallets - 40 of them - and now we've grown to more than 6000 products across many platforms. Your favorite hardware wallet? We got you covered. Desktop? Probably, too. And desktop is a lot of work as here we found many open source and reproducible products!We’ve been busy but quiet these last months. @btc_remnant improved the site a lot by adding new features around #nostr based build verifications.
We hope other projects in the nostr ecosystem like @franzap @Zapstore will see the value of these verifications and start integrating them. The more products that build on reproducibility, the more users can truly apply the principle of “Don’t trust - verify.” Binary transparency shouldn’t remain a niche feature - it needs to become the default.
If you run software that touches your private keys - be it nostr clients or bitcoin wallets - without binary transparency, only whoever built the binary really knows what code you’re running.
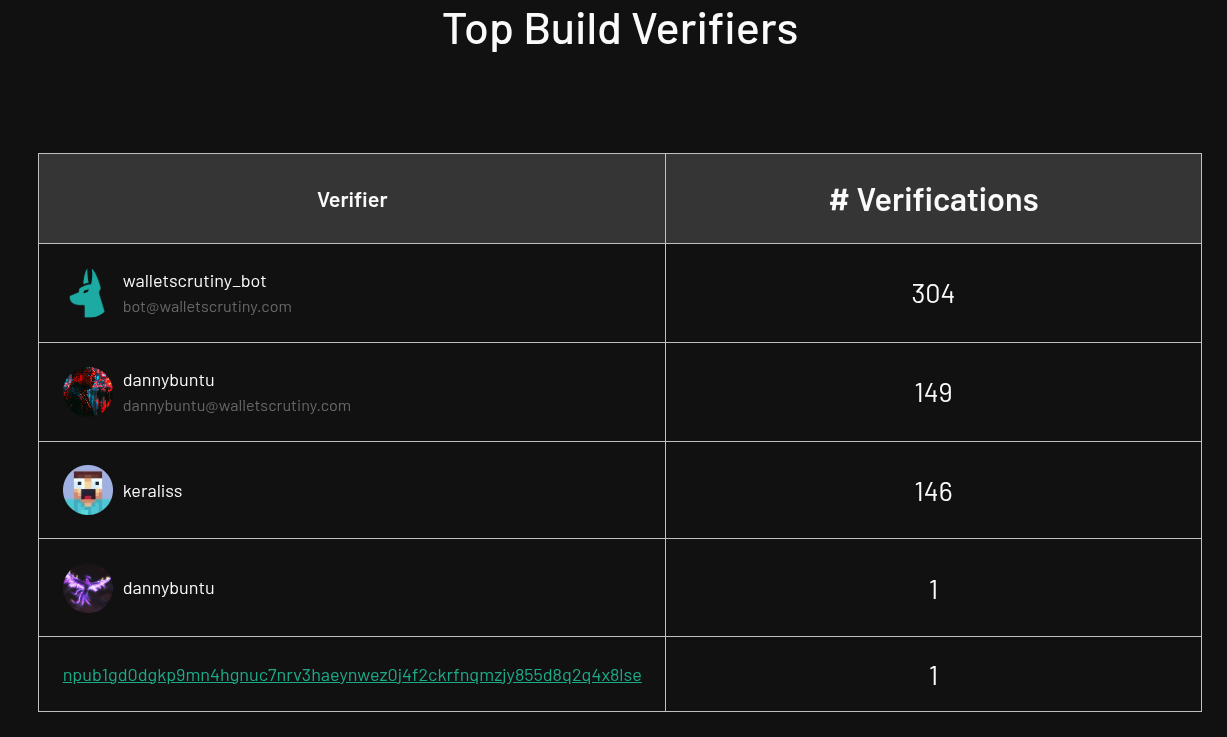 @dannybuntu and @keraliss checked the reproducibility of almost 300 binaries. The 304 verifications by @WalletScrutiny Bot are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
@dannybuntu and @keraliss checked the reproducibility of almost 300 binaries. The 304 verifications by @WalletScrutiny Bot are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
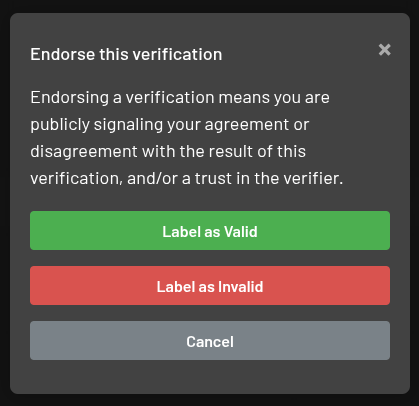 This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!
This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!
 @dannybuntu and @keraliss checked the reproducibility of almost 300 binaries. The 304 verifications by @WalletScrutiny Bot are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
@dannybuntu and @keraliss checked the reproducibility of almost 300 binaries. The 304 verifications by @WalletScrutiny Bot are all the old verifications we had migrated to nostr. And the backlog keeps growing as we cover more and more products with frequent updates.
Are we doing something valuable for the space? A @Spiral grant says yes, and community endorsements confirm it - but the project itself also needs scrutiny.
We recently introduced "verification endorsements":
 This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!
This is a simple contribution many could provide. If you read a verification and it looked plausible and complete and you trust the author, mark the verification as verified. If you ran the documented commands yourself on your hardware and got to similar results, please endorse the verification!
Even more importantly label verifications as invalid and leave a comment about what's missing when you find issues! Don't be shy!
Our goal is to document all steps such that all mildly technical users (you should be comfortable with a Linux shell) can reproduce our findings. If that's not the case, please provide your feedback and we will improve ✋.
And if you maintain one of the products we check, share your own verification as a template for others!The ByBit Hack Report [1] reveals interesting details.
While many blame ETH and its complexities, it's important to note that a combination of circumstances made this attack possible.
But the core issue clearly was a central point of failure. Multi Signature was used but all signers used the same hacked, remote server.
The server was trusted, supposedly running a well audited open source web wallet software but "open source" is not enough as the source run on that compromised server did not match the well audited code.
At WalletScrutiny we so far do not list web wallets because it is hard if not impossible to attest to the integrity of web wallet code when the server can serve different code every other second or depending on your IP address.
We are investigating options to list progressive web apps that give the user more control of what is being run. While standard PWA manifests primarily contain metadata, a security-focused implementation could leverage several mechanisms to establish stronger integrity guarantees:
Extending manifest files with cryptographic commitments to all resources
Implementing Subresource Integrity (SRI) checks to verify each script matches expected hashes
Using a trust-on-first-use (TOFU) signature model where developer keys are stored after initial verification
Creating transparent, user-controlled update processes that display cryptographic verification before applying changes
Such an approach would significantly reduce trust requirements in the server after initial installation, as the PWA could verify the integrity of updates against developer signatures before execution. Static analysis could also differentiate between PWAs with secure update mechanisms versus those with silent automatic updates.
While not eliminating all risks, this model would provide a more verifiable path than traditional web wallets, potentially bringing them closer to the verification standards we apply to other wallet types.
[1] 
DocSend
Bybit Hack Report
DocSend
English speakers please help us out here ...
We are close to launching "attestations" where anybody will be able to attest to the reproducibility of binaries. The process is technical and quite involved. Are those who do this ...
* Attestators
* Wittnesses
* Verifiers
* Certifiers
#askNostr
Question for people who looked at individual reviews on  Should we remove the individual coloring of pages based on the product's logo?
Please comment below or vote on Xitter
Should we remove the individual coloring of pages based on the product's logo?
Please comment below or vote on Xitter 

WalletScrutiny
Know your wallet like you built it.
Not everyone is a developer. Not everyone has to be.

X (formerly Twitter)
WalletScrutiny (@WalletScrutiny) on X
Question for people who looked at individual reviews on https://t.co/np0b5LsMBI: Should we remove the individual coloring of pages based on the pro...
Today we welcome @btc_remnant as our new lead developer! He brings a lot of experience not only with Bitcoin and nostr but even was involved with two reproducible wallet builds already years ago besides many other bitcoin tools he contributed to.
At least some 300,000 machines reachable on the internet are vulnerable to a remote code execution vulnerability that appears to be rather easy to execute on all of those.
The vulnerable package is cups-browsed - a tool for printing - which does get installed by default on many desktop linux systems but who knows ... maybe you are running some media server with your bitcoin wallet and your printer reachable via the same RaspberryPi?
Check your machines. Android appears not to run cups but if you run Linux or Mac, you might want to double-check if you're one of the lucky 300,000 that get to update their system **now**.


evilsocket
Attacking UNIX Systems via CUPS, Part I
At WalletScrutiny.com, we track 4574 apps on Google Play. 2956 of those are not on Google Play anymore. Can that be right?
The Apple App Store "only" shows 550 of 1291 apps as removed.
Either way, especially if you found a cool new wallet, assume the fun will not last.
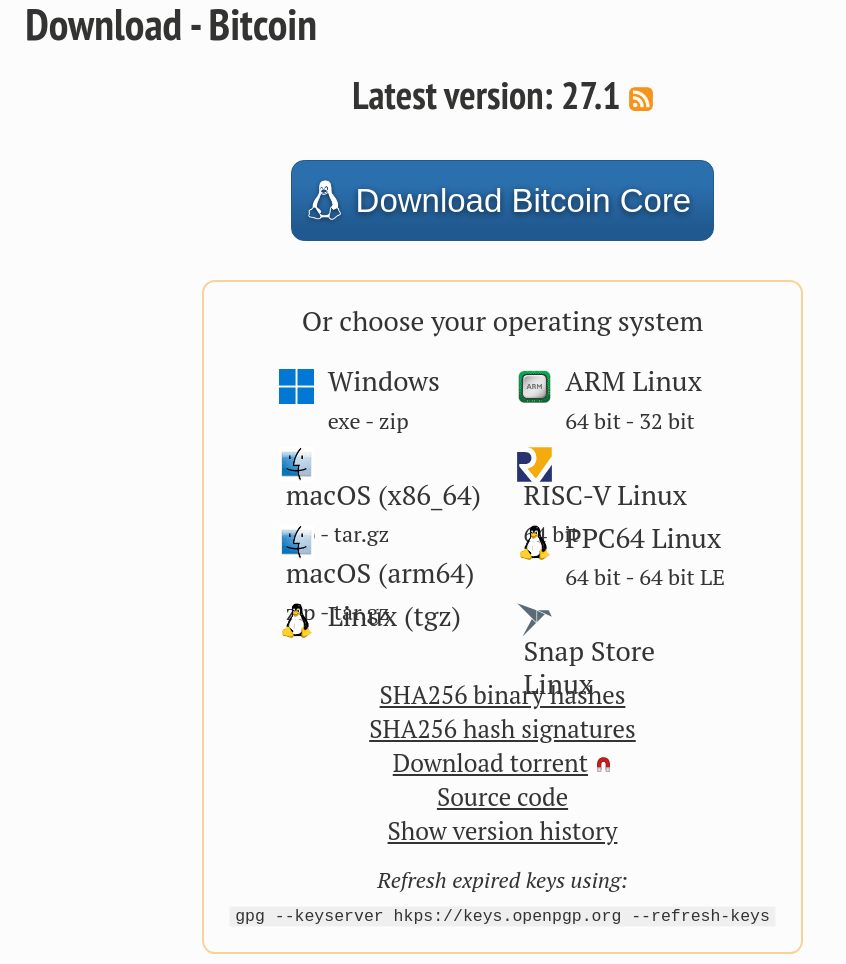
We have long been working on testing desktop wallets but it's really tricky as there is just so many binaries floating around for what claims to be the same product. Even Bitcoin Core is showing 8 download options depending on your operating system or distribution channel preference:
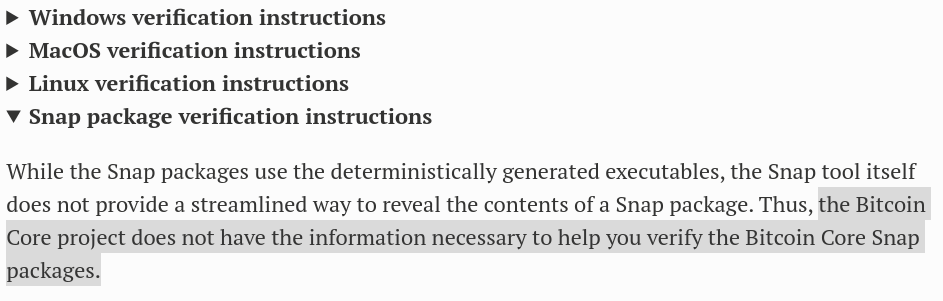
 With snapcraft obviously being tricky:
With snapcraft obviously being tricky:
 Either way, for desktop wallets, most of the time people have download links and want to verify those downloads, so Chris is working on a binary checker. It's still only a draft merge request and clearly needs a design but what it will enable is actually pretty cool:
WalletScrutiny calculates the hash of the file dropped onto it and if it's an apk, it also determines the appId which allows finding the right product. If the hash is known, the verdict is immediately displayed. If not, the page invites the user to upload the file for analysis.
The attestations for artifacts will live on nostr as signed events and nostr will also be used to advertise the existance of new binaries for reviewers.
Either way, for desktop wallets, most of the time people have download links and want to verify those downloads, so Chris is working on a binary checker. It's still only a draft merge request and clearly needs a design but what it will enable is actually pretty cool:
WalletScrutiny calculates the hash of the file dropped onto it and if it's an apk, it also determines the appId which allows finding the right product. If the hash is known, the verdict is immediately displayed. If not, the page invites the user to upload the file for analysis.
The attestations for artifacts will live on nostr as signed events and nostr will also be used to advertise the existance of new binaries for reviewers.
 With snapcraft obviously being tricky:
With snapcraft obviously being tricky:
 Either way, for desktop wallets, most of the time people have download links and want to verify those downloads, so Chris is working on a binary checker. It's still only a draft merge request and clearly needs a design but what it will enable is actually pretty cool:
WalletScrutiny calculates the hash of the file dropped onto it and if it's an apk, it also determines the appId which allows finding the right product. If the hash is known, the verdict is immediately displayed. If not, the page invites the user to upload the file for analysis.
The attestations for artifacts will live on nostr as signed events and nostr will also be used to advertise the existance of new binaries for reviewers.
Either way, for desktop wallets, most of the time people have download links and want to verify those downloads, so Chris is working on a binary checker. It's still only a draft merge request and clearly needs a design but what it will enable is actually pretty cool:
WalletScrutiny calculates the hash of the file dropped onto it and if it's an apk, it also determines the appId which allows finding the right product. If the hash is known, the verdict is immediately displayed. If not, the page invites the user to upload the file for analysis.
The attestations for artifacts will live on nostr as signed events and nostr will also be used to advertise the existance of new binaries for reviewers.Not all metal backups are made equally. If you use metal to not have to also worry about your bitcoins when your house is on fire, don't use this product:
 But running these tests must have been great fun, right @Jameson Lopp?
If we add these backup solutions to our website, we would certainly heavily lean on Jameson Lopp's work as a hydrolic press and acids isn't what we had planned to play around with ourselves for now.
Jameson are you planning to test more products any soon? Adding "backup tools" to WalletScrutiny might get excessive if we don't draw lines like you did. If it's not at least claiming to be heat resistant, we won't bother to list it or else we end up listing a million different ways to print on paper.
But running these tests must have been great fun, right @Jameson Lopp?
If we add these backup solutions to our website, we would certainly heavily lean on Jameson Lopp's work as a hydrolic press and acids isn't what we had planned to play around with ourselves for now.
Jameson are you planning to test more products any soon? Adding "backup tools" to WalletScrutiny might get excessive if we don't draw lines like you did. If it's not at least claiming to be heat resistant, we won't bother to list it or else we end up listing a million different ways to print on paper.
 But running these tests must have been great fun, right @Jameson Lopp?
If we add these backup solutions to our website, we would certainly heavily lean on Jameson Lopp's work as a hydrolic press and acids isn't what we had planned to play around with ourselves for now.
Jameson are you planning to test more products any soon? Adding "backup tools" to WalletScrutiny might get excessive if we don't draw lines like you did. If it's not at least claiming to be heat resistant, we won't bother to list it or else we end up listing a million different ways to print on paper.
But running these tests must have been great fun, right @Jameson Lopp?
If we add these backup solutions to our website, we would certainly heavily lean on Jameson Lopp's work as a hydrolic press and acids isn't what we had planned to play around with ourselves for now.
Jameson are you planning to test more products any soon? Adding "backup tools" to WalletScrutiny might get excessive if we don't draw lines like you did. If it's not at least claiming to be heat resistant, we won't bother to list it or else we end up listing a million different ways to print on paper.Some fan art ✨ 🎶 🎶
Which one do you like best?
If you still have funds trapped in Samourai, @dannybuntu wrote some tips on what to do next to recover them here:
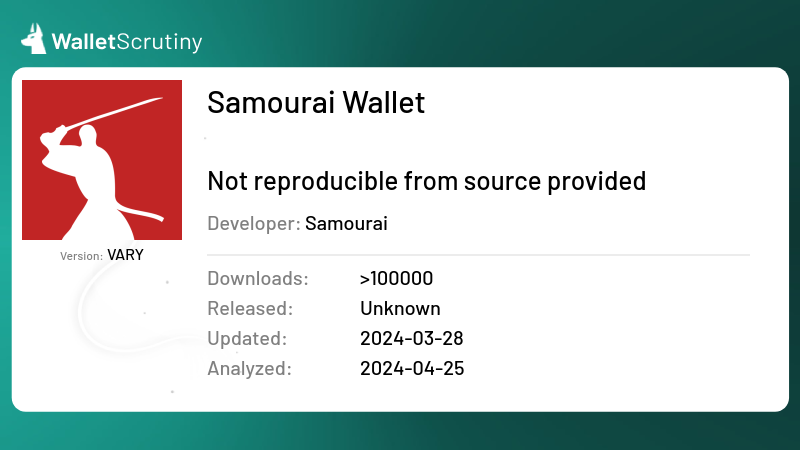

WalletScrutiny
Samourai Wallet
Review of Samourai Wallet (verdict: sourceavailable)
 Most people don't dig that deeply but when they do, they have this question. Computers are 1s and 0s. They are digital. How can they be non-deterministic??
Software development mostly revolves around performance both in the end product and the development process. Only very few developers even spend a thought on reproducibility. So if they compile something and it compiles 5 seconds faster, they can test the feature they were working on 5 seconds quicker. These two reasons result in stuff being non-reproducible as:
Files are processed in the order they come and that order depends on many factors. For example some file systems sort by date and others by file name.
Compilers can optimize the result, so compiling something with one version of the compiler will often give a different result than when compiled with another version.
The compiler might process multiple files in parallel and pack them into the result as they finish compiling.
Other sources of problems are timestamps or file paths that end up in the result.
Some tools on purpose use randomnes to generate IDs that are unique to every build.
Of the above issues, all result in non-reproducibility by our standards. While some lead us to comment on the build looking benign as the diff is only some random number appearing twice, others might also be benign but result in differences far too big to quickly judge with the tools we are using.
The more developers care about reproducibility over only performance, the better it will get but there are some widely used tools that consistently cause issues and maybe should just be avoided in wallets.
Most people don't dig that deeply but when they do, they have this question. Computers are 1s and 0s. They are digital. How can they be non-deterministic??
Software development mostly revolves around performance both in the end product and the development process. Only very few developers even spend a thought on reproducibility. So if they compile something and it compiles 5 seconds faster, they can test the feature they were working on 5 seconds quicker. These two reasons result in stuff being non-reproducible as:
Files are processed in the order they come and that order depends on many factors. For example some file systems sort by date and others by file name.
Compilers can optimize the result, so compiling something with one version of the compiler will often give a different result than when compiled with another version.
The compiler might process multiple files in parallel and pack them into the result as they finish compiling.
Other sources of problems are timestamps or file paths that end up in the result.
Some tools on purpose use randomnes to generate IDs that are unique to every build.
Of the above issues, all result in non-reproducibility by our standards. While some lead us to comment on the build looking benign as the diff is only some random number appearing twice, others might also be benign but result in differences far too big to quickly judge with the tools we are using.
The more developers care about reproducibility over only performance, the better it will get but there are some widely used tools that consistently cause issues and maybe should just be avoided in wallets.Hi @Coinkite (old npup)
We were asked to attest to the reproducibility of your Q1 wallet and while the shop looks like it's maybe not released, we think it's just out of stock? May we ask for a release date?
 appears to not support compiling the firmware for the Q1, right? We found for example 2024-04-02T1416-v1.1.0Q-q1-coldcard.dfu at
appears to not support compiling the firmware for the Q1, right? We found for example 2024-04-02T1416-v1.1.0Q-q1-coldcard.dfu at  yet the script appears to assume the download always to contain "mk".
Where can we find the documentation to reproducibly build the Q1 firmware?
yet the script appears to assume the download always to contain "mk".
Where can we find the documentation to reproducibly build the Q1 firmware?
GitHub
firmware/stm32/repro-build.sh at master · Coldcard/firmware
❄️ Firmware and simulator for Coldcard Hardware Wallet - Coldcard/firmware

COLDCARD - Latest Firmware Downloads
Download the latest firmware for your COLDCARD hardware wallet.

WalletScrutiny
Samourai Wallet
Review of Samourai Wallet (verdict: sourceavailable)
Has anybody noticed that we now have "screen recordings" in our reproducibility tests? As another project is sharing "video proof" of reproducibility, we were asked to also do so but it felt kind of pointless to produce GBs of data for every reproducibility test. We did however start playing around with console recordings that are somewhat more optimized as they record the ASCII on the screen and not every pixel. Resulting files are much more manageable but for example, running the compile script for the Electrum for Android app resulted in 72MB of output. As we test a lot, this is a lot to add in a single day.
Does anybody care about screen recordings? Can we throw them at some nostr relay instead of our git repo, with some expiry date in three months, so that interested users can grab it while it's hot? Any other ideas?
Currently the tiniest ascii cast is the one for the Schildbach "Bitcoin Wallet": 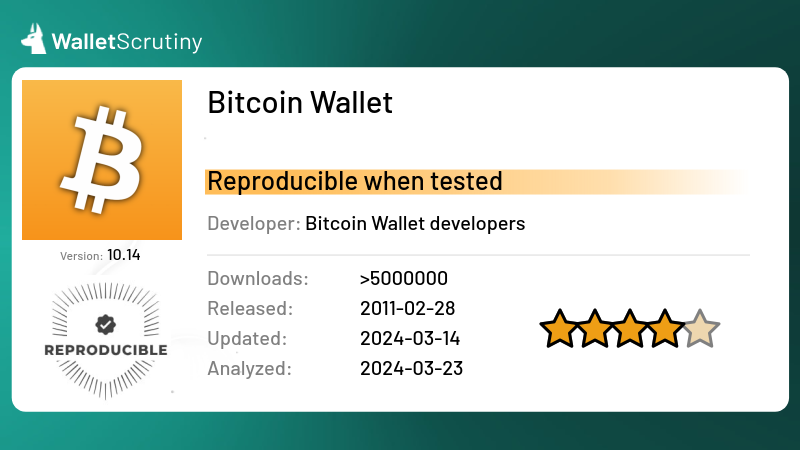

WalletScrutiny
Bitcoin Wallet
Review of Bitcoin Wallet (verdict: sourceavailable)
It can be really frustrating to hunt after fake apps when not even the provider of the original seams to care ...
Here is our attempt at reporting a fraud at 
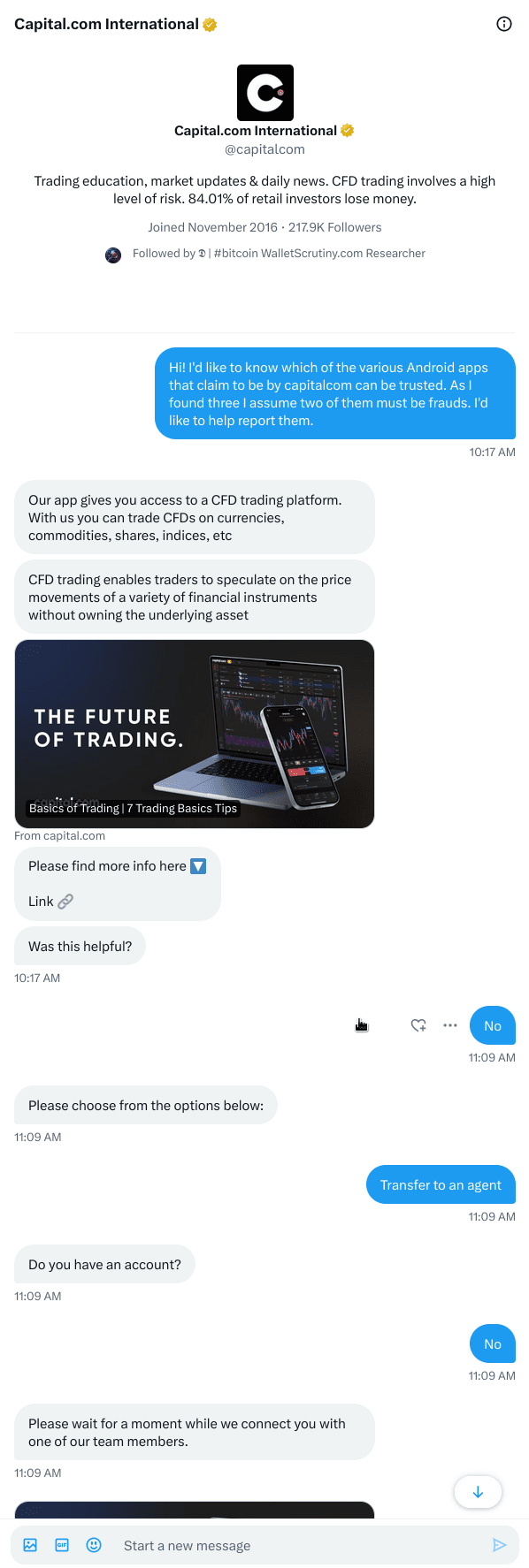
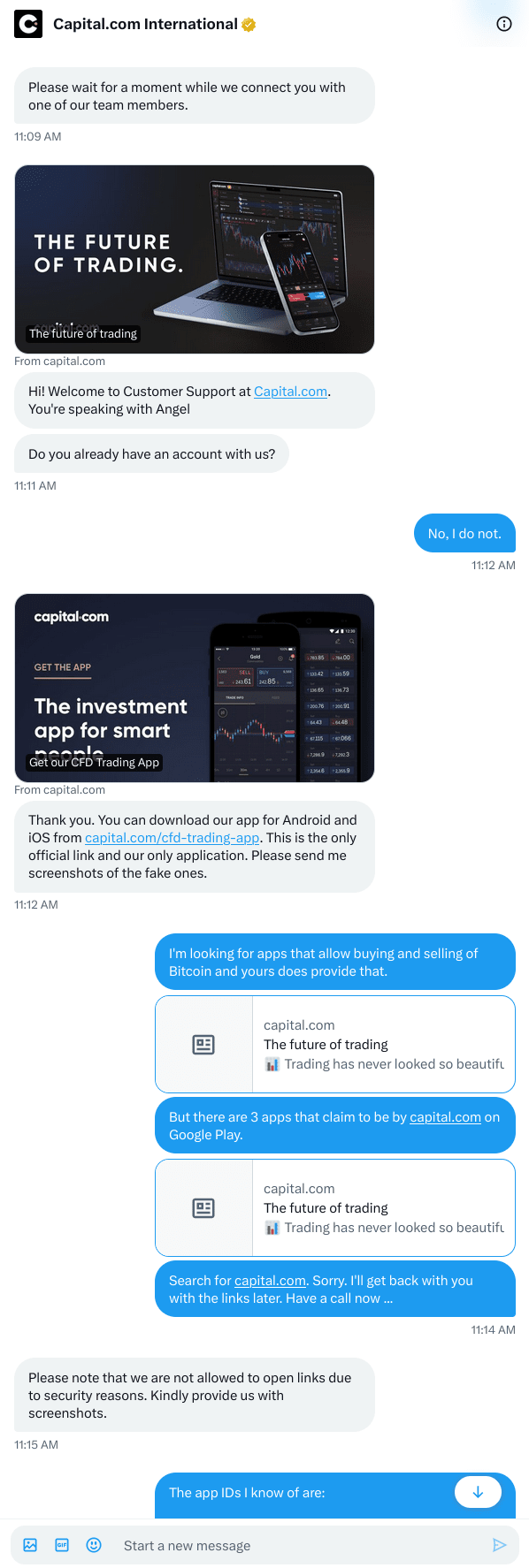
 View quoted note →
View quoted note →

Online Trading with Our Award-winning Platform | Capital.com
Join 798,000+ global traders on OMA’S Best Overall Trading Platform 2024. Trade 5,000+ CFD markets and get 24/7 English support. 81.31% of invest...




Does anybody know how
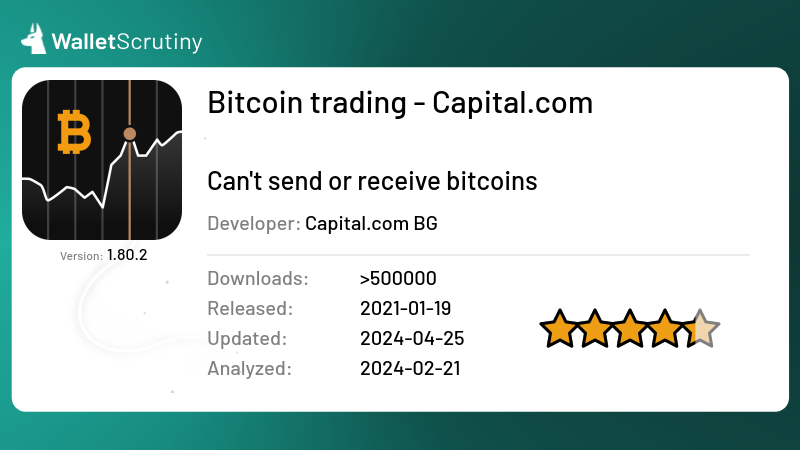 relates to
relates to
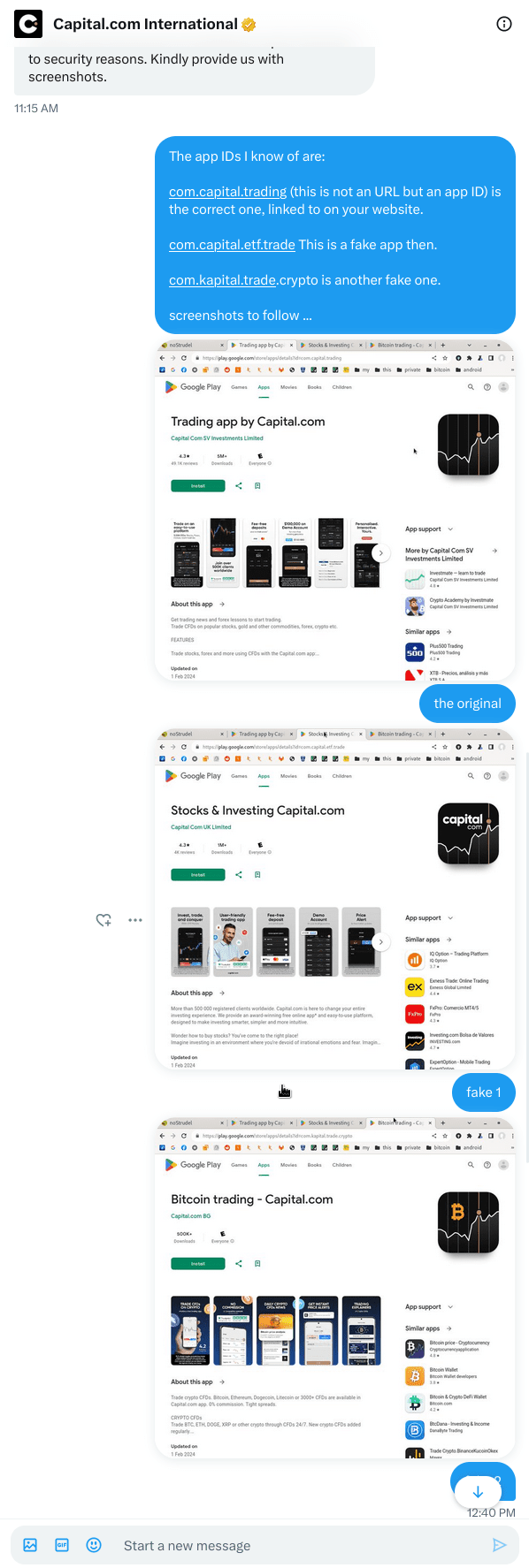
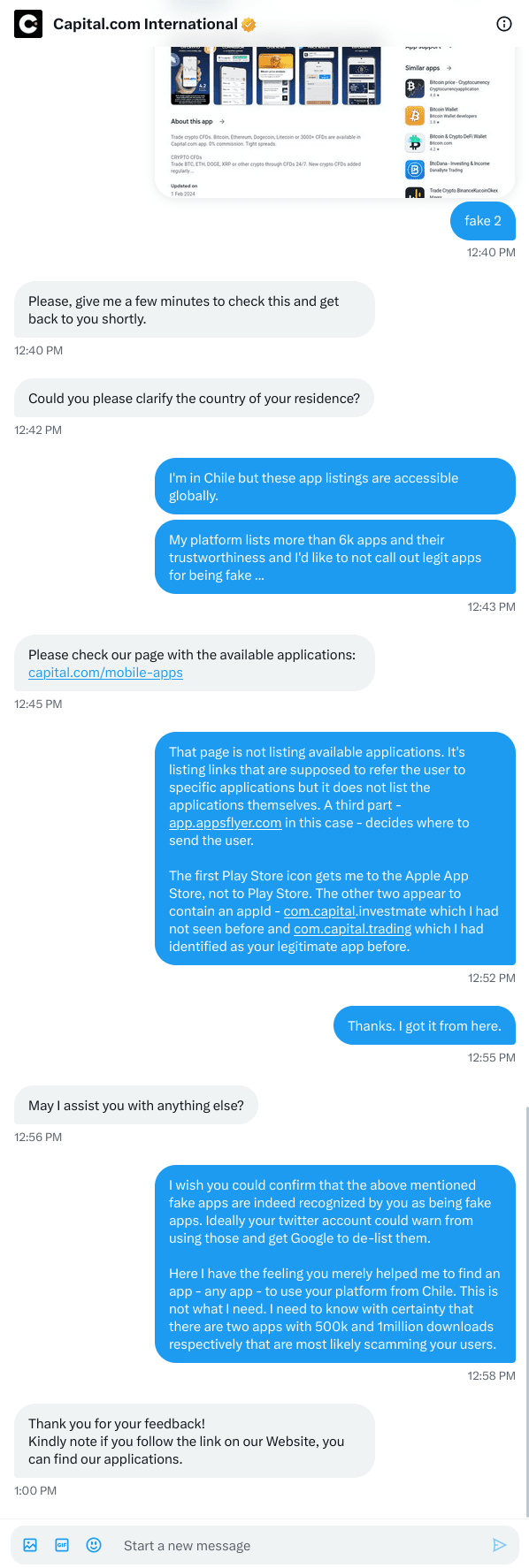
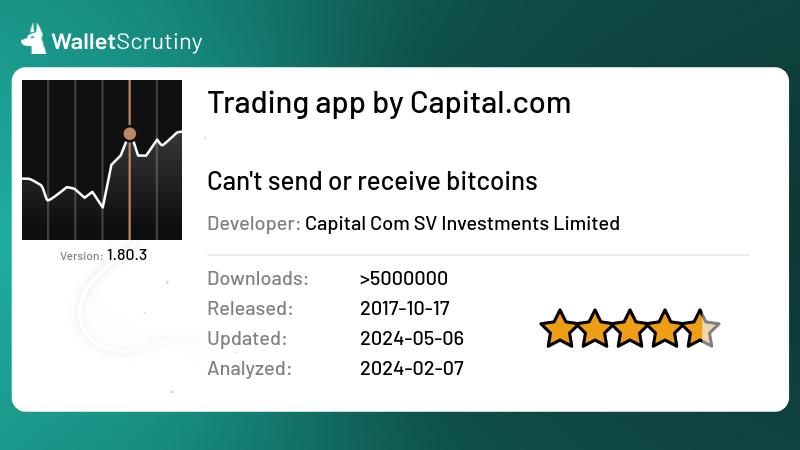 The former has 500k users but looks like a fake app given the "typo" in the app ID and given that capitalCom links to the latter, only.
The former has 500k users but looks like a fake app given the "typo" in the app ID and given that capitalCom links to the latter, only.

WalletScrutiny
Bitcoin trading - Capital.com
Review of Bitcoin trading - Capital.com (verdict: nosendreceive)

WalletScrutiny
Trading app by Capital.com
Review of Trading app by Capital.com (verdict: nosendreceive)
Sadly Mycelium hasn't published any source code updates since June, yet their latest release on Google Play was days ago. As of now, Mycelium for Android has to be considered closed source.
We poked Alexander Pavlenko - the author of the last commit and probably maintainer - on Telegram yesterday but did not get a reply yet.
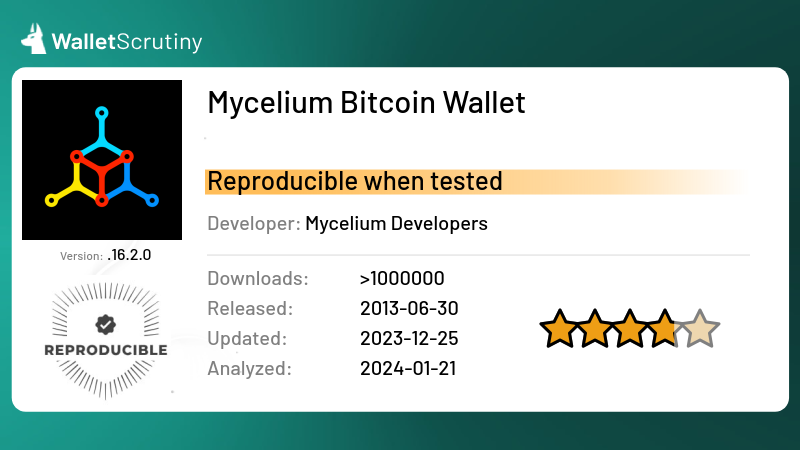

WalletScrutiny
Mycelium Bitcoin Wallet
Review of Mycelium Bitcoin Wallet (verdict: sourceavailable)