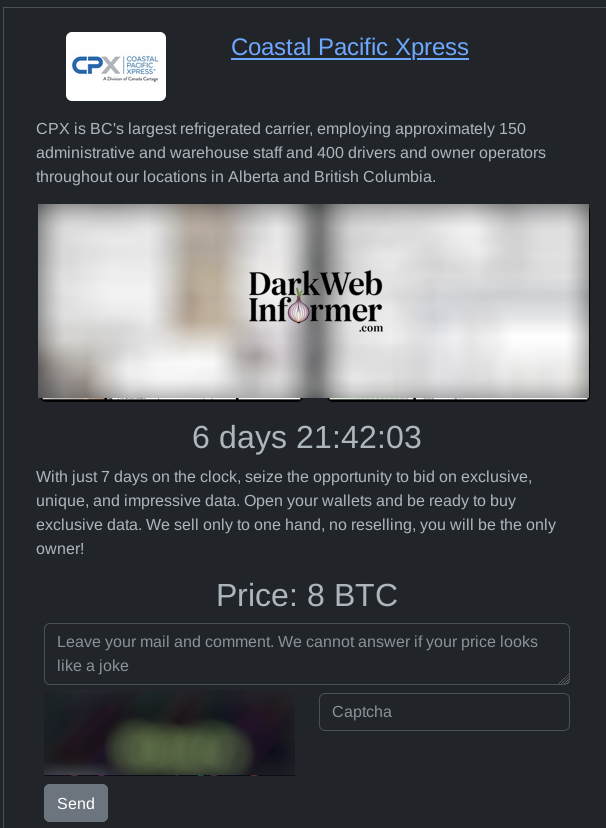
‼️ An international law enforcement operation called "Operation Switch off" has concluded, targeting what authorities describe as a large-scale illegal IPTV streaming network.
Led by Italy's Catania Public Prosecutor's Office and coordinated through Eurojust, Europol, and Interpol, the investigation identified 31 individuals allegedly connected to a transnational criminal organization. The suspects face accusations including unauthorized broadcasting of access-controlled content, computer fraud, and money laundering.
According to investigators, the network captured and redistributed live broadcasts and on-demand content from major platforms including Sky, DAZN, Amazon Prime, Netflix, Paramount, and Disney+, allegedly serving millions of users worldwide.
More than 100 Italian Postal Police officers executed searches across 11 Italian cities and 14 international locations, with cooperation from authorities in the United Kingdom, Spain, Romania, Kosovo, Canada, India, South Korea, and the United Arab Emirates.
The year-long investigation built on intelligence from a previous operation called "Taken Down." Authorities allege the suspects used cryptocurrency investments, shell companies, and fictitious asset registrations to obscure proceeds that reportedly generated millions of euros monthly.
The operation disrupted approximately 1,000 Italian resellers and cut service to over 100,000 end users in Italy, with millions more affected globally. Three illegal IPTV platforms were seized in Italy, while investigators in Romania identified a significant distribution operation running six servers.
The original video is in 360p. Source:

Polizia di Stato
Operazione "Switch off": spento lo streaming delle Iptv illegali | Polizia di Stato
Operazione Switch off: spento lo streaming delle Iptv illegali