Anyway, what do you think of NIP-17?
Login to reply
Replies (5)
In terms of metadata privacy, NIP-17 is better than NIP-4. NIP-17 provides better protection for the sender's ID, but it does not sufficiently protect the recipient's ID. The visibility of someone continuously receiving messages is also a metadata privacy issue. For a DM (a feature subsidiary to microblogging), this might be an acceptable tradeoff, as users can receive and decrypt messages on multiple clients. However, for an application using Nostr for a chat app, privacy should be a priority.
Since we are considering using NIP-17, we delved deeper into it. So, let's revisit your question, "What do you think of NIP-17?"
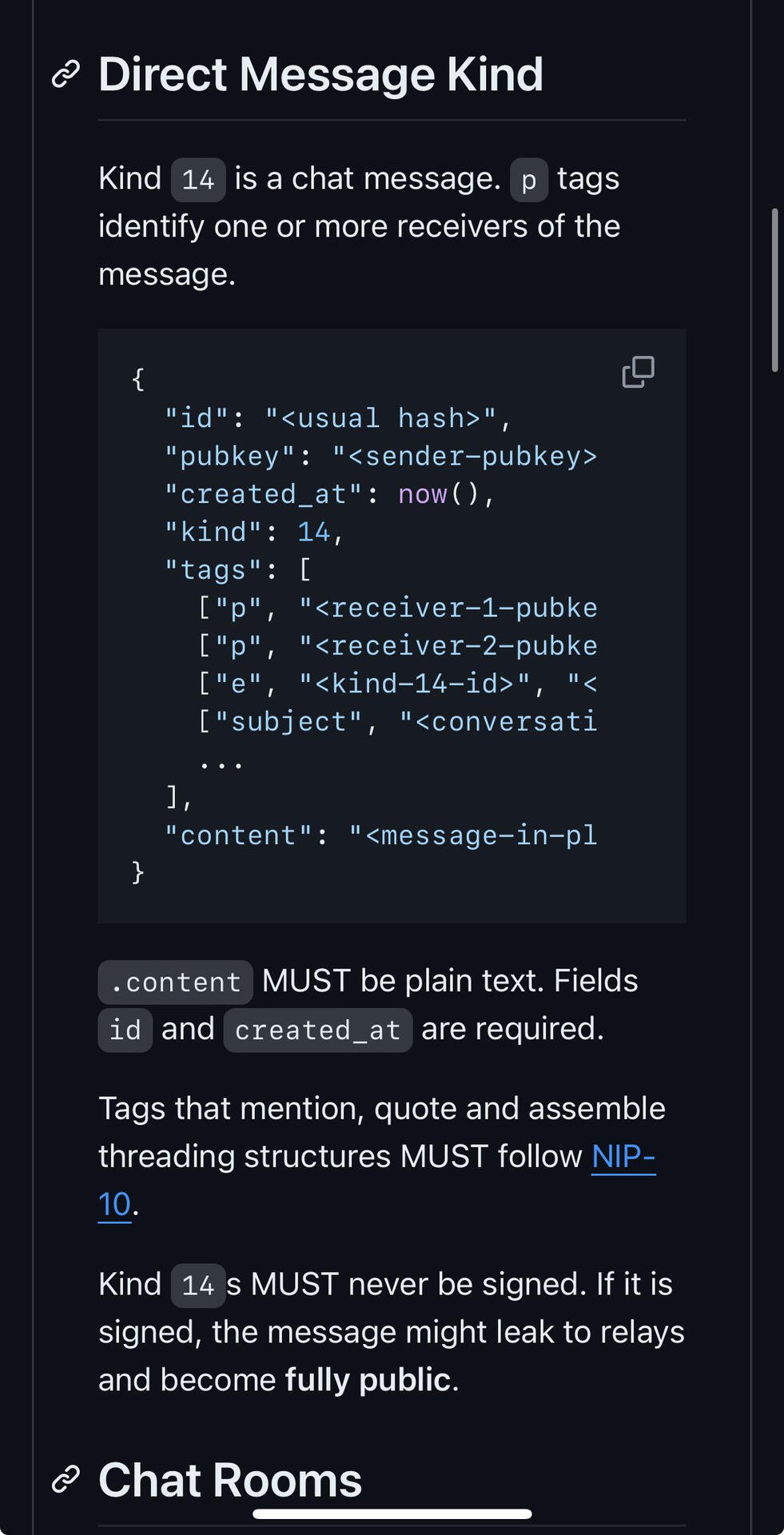
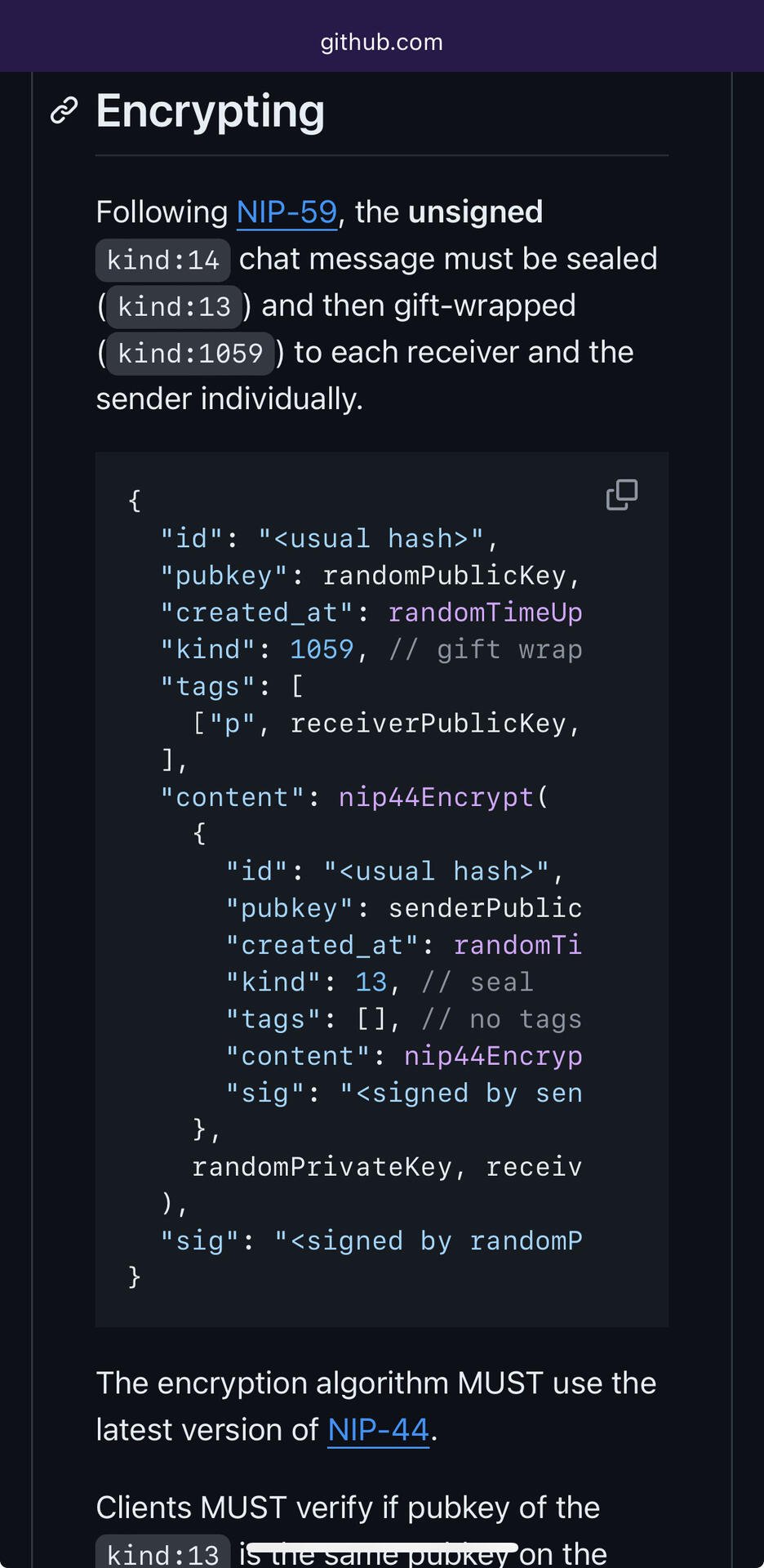
NIP17 defines a message structure as kind1059(kind13(kind14)). We are puzzled as to why it is necessary to apply NIP44 encryption twice.
Kind13 (seal) is responsible for digitally signing and encrypting the message. Since kind1059 has already encrypted the message, there is no need for kind13 to encrypt it again. Therefore, the only role left for kind13 is digital signing. We wonder why the digital signature cannot be directly incorporated into kind14. A digitally signed kind14 would effectively be equivalent to kind1. Hence, we believe that kind1059(kind1) would be a simpler implementation.
Moreover, changing the timestamp of kind1059 messages to a random time from the past two days could lead to relays repeatedly pushing notes to clients, potentially burdening both clients and relays. We are uncertain if this tradeoff is justified.

GitHub
nips/17.md at master · nostr-protocol/nips
Nostr Implementation Possibilities. Contribute to nostr-protocol/nips development by creating an account on GitHub.


Maybe don't actually replace NIP-04 since it's in Keychat already, even if deprecated, but have both NIPs implemented, each with its own warnings. So Keychat could have Signal-encrypted chats, normal NIP-04 chats (both already in) and NIP-17 chats.
the timestamps thing is weird yeah, but they did it to keep perpetuating the myth of free relays with no read access controls..



