Some new introductions for Keychat will be added next year. View quoted note →

Keychat
npub1h0uj...rwx8
Keychat is the super app for Bitcoiners.
Sovereign IDs, Bitcoin Wallet, Secure Chat, Mini Apps — all in Keychat.
Sovereign. Security. Richness
Contact us for feedback 👇
https://www.keychat.io/u/?k=npub1h0uj825jgcr9lzxyp37ehasuenq070707pj63je07n8mkcsg3u0qnsrwx8
The Web is inherently more expansive. View quoted note →
Keychat for Bitcoin. View quoted note →
Keychat for Bitcoiner. View quoted note →
Rather than saying Keychat's target users are Nostr users, it's more accurate to say Keychat's target users are Bitcoin users.
Nostr mainly uses temporal structure to organize information, whereas the Web employs both temporal and spatial structures.
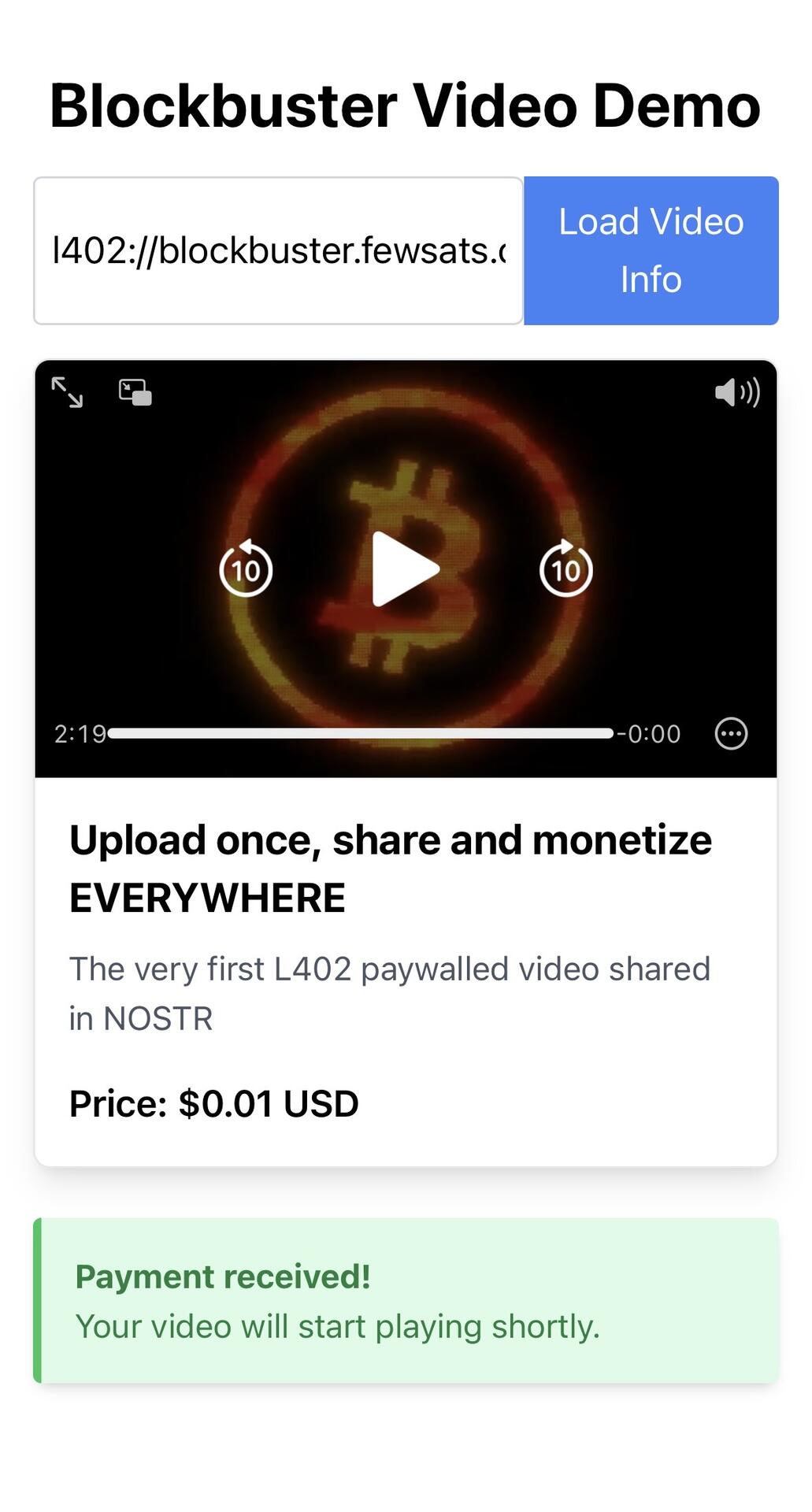
When a user asks a question to an AI bot, Keychat attaches ecash sats to the message and encrypts it.
Once the AI bot receives and decrypts the message, it first collects the ecash sats and then calls an API to retrieve the answer. The AI bot then sends the answer back to the user through Keychat.
For users, sending messages to an AI bot is the same as sending messages to a human.
Keychat does not become more complex because of bots. View quoted note →
The latest version of Keychat uses OpenMLS to implement large group chat.
Please note that MLS large group chat is still in its early testing phase, and we will continue to develop and refine it. OpenMLS is also in its early stages.
If you're interested in learning about the MLS protocol, the note below might be helpful.
 View quoted note →
View quoted note →
GitHub
Releases · keychat-io/keychat-app
Keychat is the super app for Bitcoiners. Autonomous IDs, Bitcoin ecash wallet, secure chat, and rich mini apps — all in Keychat. Autonomy. Securi...
The latest version of Keychat supports AI bots, with a pay-per-use model using ecash sats.
Anyone can create a bot on Keychat. Looking forward to the emergence of more types of bots!
 View quoted note →
View quoted note →
GitHub
Releases · keychat-io/keychat-app
Keychat is the super app for Bitcoiners. Autonomous IDs, Bitcoin ecash wallet, secure chat, and rich mini apps — all in Keychat. Autonomy. Securi...
Over the past few weeks, we have been learning and testing the MLS protocol and have gained a deeper understanding of it. Below is a note providing a general description of the MLS protocol.
The MLS group members (A, B, C, D, E, F, G, H) form the leaf nodes of a binary tree as shown below. Each member has a pair of public and private keys.
For member A, they use their private key  and member B’s public key  to perform an ECDH computation. For member B, they use their private key  and member A’s public key  to perform an ECDH computation.
Both compute the same value. This value becomes the private key of Node3, and from this, the public key of Node3 can also be derived.
Similarly, other members perform their respective ECDH computations.
Moreover, nodes higher in the tree also perform their respective ECDH computations up to the Root. Node3 and Node4 compute the private key of Node1 through ECDH, while Node5 and Node6 compute the private key of Node2. Node1 and Node2 compute the private key of the Root through ECDH.
The private key of the Root is the shared key among the MLS group members. Each member uses this shared key along with their respective related keys to derive their message encryption key.
The most important feature of this key tree is that child nodes know the private keys of their parent nodes.
—————————————————
If member A suspects their key has been compromised, they need to update their key.
Member A generates a new key pair  (public key and private key) locally and recalculates the keys for Node3’, Node1’, and Root’.
Then, A encrypts the public keys of Node3’ and Node1’ using the old public keys of Node3 and Node1, respectively, and sends them to all group members.
When member H receives and decrypts the message, they obtain the public key of Node1’ and, combined with the private key of Node2, perform an ECDH computation to calculate the new private key of Root’.
Other members perform similar operations. As a result, all members successfully update the key tree.
The advantage of the MLS protocol is that when a member updates their key, the complexity of updating the key tree is reduced to O(logN).
Imagine if there were no binary tree. When A updates their key, they would need to update the message one-to-one for each group member, resulting in a complexity of O(N).
However, if member B’s key is compromised, member A updating their key cannot rescue member B. Each member’s update key operation can only protect themselves, not all members. 
 View quoted note →
View quoted note →


Pubky is very aware that it is web. 👍 View quoted note →
Thanks for testing. 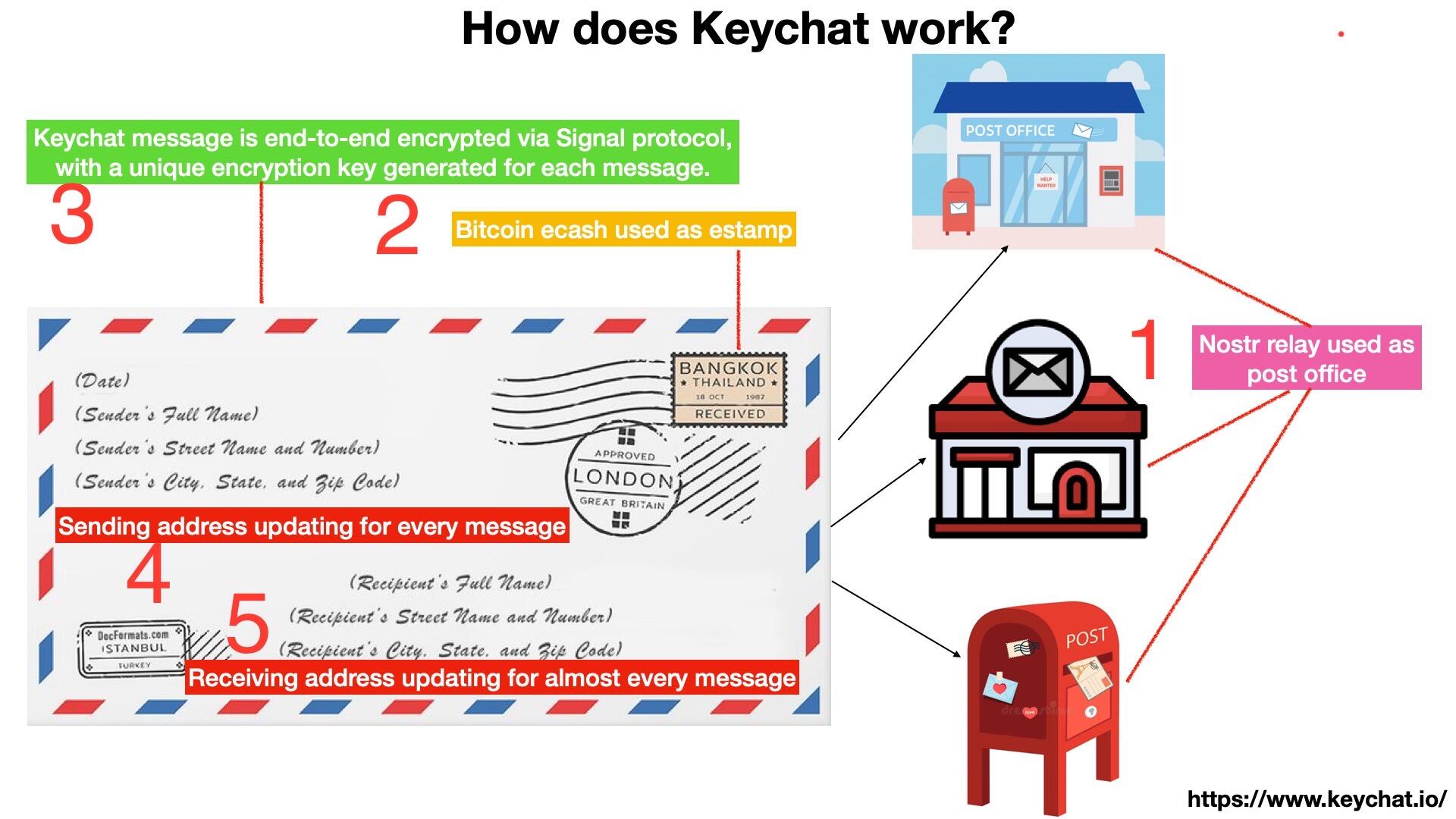 View quoted note →
View quoted note →
 View quoted note →
View quoted note →We are developing this feature for Keychat. 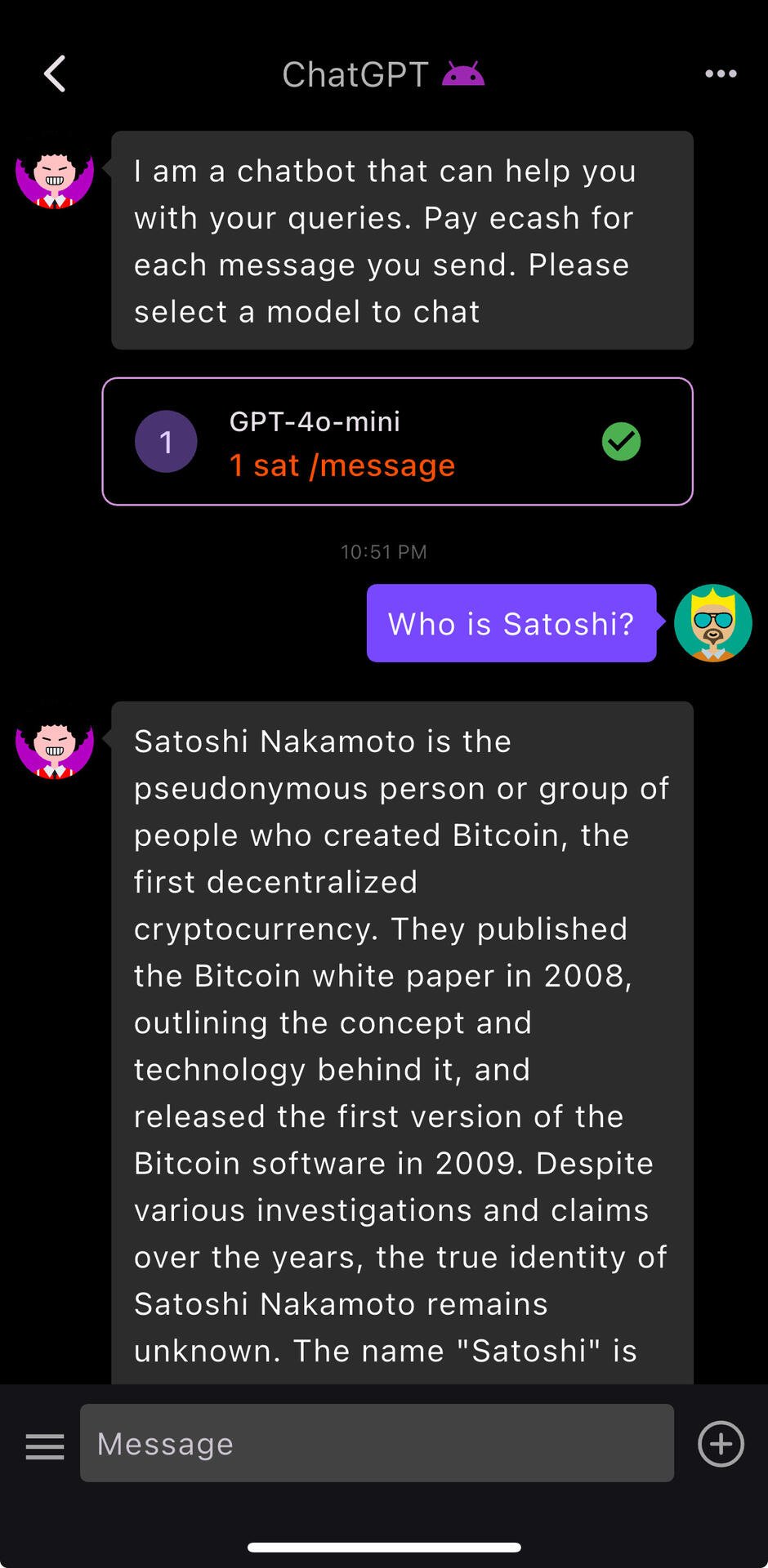 View quoted note →
View quoted note →
 View quoted note →
View quoted note →Is the web browser a super app?