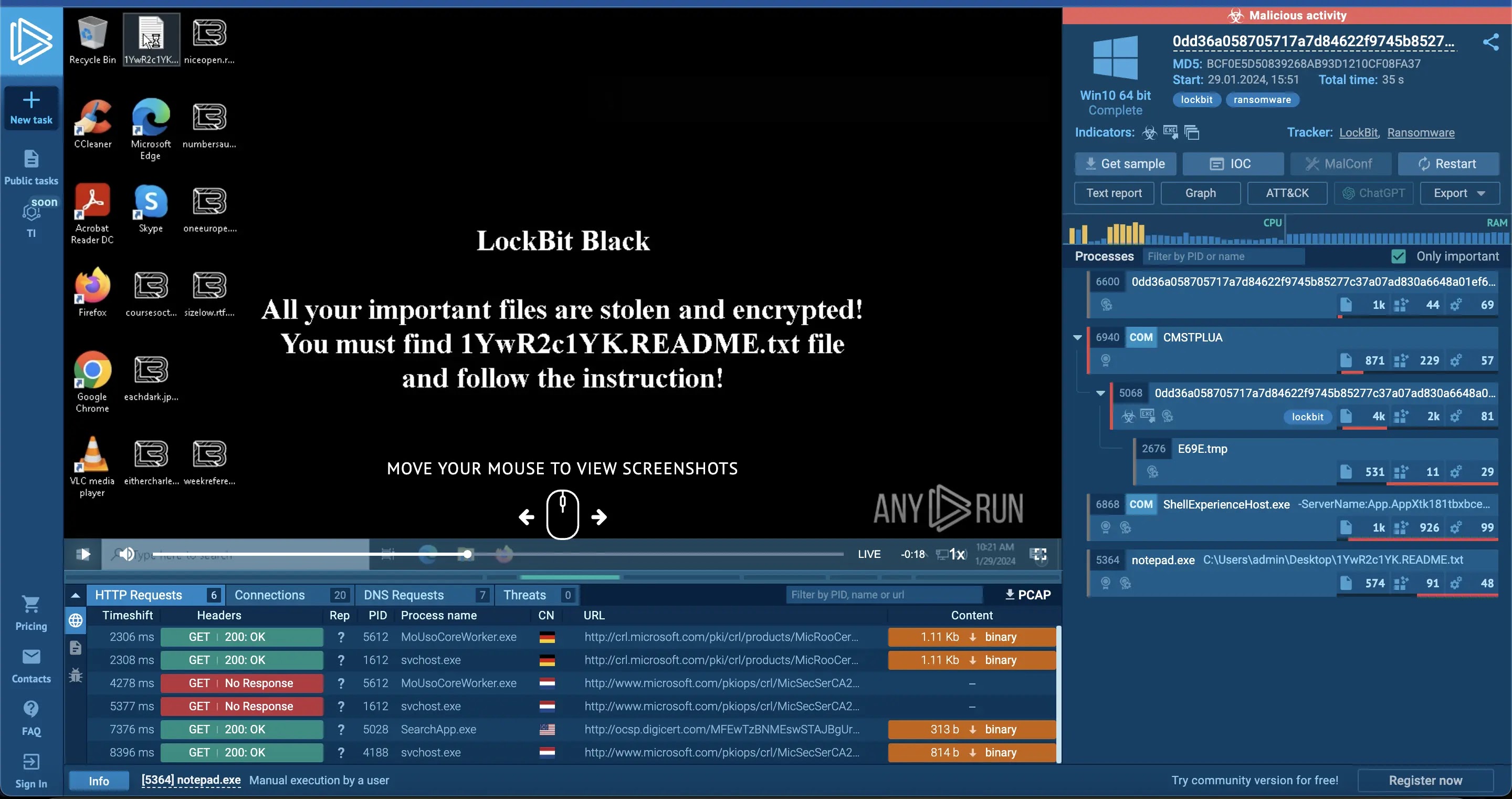
#Summary:
JetBrains TeamCity On-Premises software has a critical flaw (CVE-2024-23917) that could grant attackers administrative control over affected servers. Patched for TeamCity Cloud servers, On-Premises users should update to version 2023.11.3 or use a security patch plugin. Organizations must prioritize immediate patching and focus on vulnerability management.
#Hashtags:
#TeamCity #securityflaw #administrativecontrol #patched #vulnerabilitymanagement


Infosecurity Magazine
Patched Critical Flaw Exposed JetBrains TeamCity Servers
Tracked as CVE-2024-23917, the flaw carries a CVSS rating of 9.8