
How Are Atomic Swaps Secure Even Though They Are Off-Chain?
On-Chain vs. Off-Chain Swaps:
Atomic swaps can occur both on-chain and off-chain. Off-chain swaps happen outside the main blockchain, which speeds up transactions and reduces the load on the network. However, the primary concern is how to ensure security in off-chain transactions. Off-chain atomic swaps are often executed through second-layer solutions like the Lightning Network.
In off-chain swaps, security is primarily maintained using Hashed Time-Locked Contracts (HTLCs) and cryptographic verifications. HTLCs are crucial in both on-chain and off-chain atomic swaps.
Technical Details:
What Are HTLCs?
HTLCs are smart contracts that impose conditions based on time and cryptographic hash values. They ensure that a transaction will only complete if a specific encrypted value (hash) is revealed within a set time frame. If the value is not revealed, the transaction is canceled, and the funds are returned. These two mechanisms maintain security.
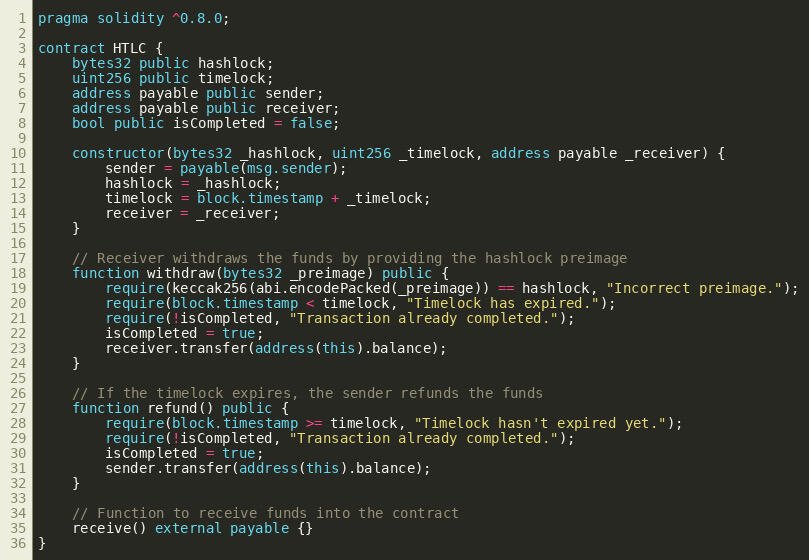
uploaded as image HTLC code example
What’s Happening Here?
1. Contract Creation: Alice initiates the contract to swap with Bob. Alice creates a hash value (hashlock), and Bob needs to unlock it by providing the preimage. There is also a time limit (timelock) defined; if the swap is not completed in time, Alice can retrieve her funds.
2. Withdraw Function: Bob unlocks Alice’s funds by providing the correct preimage. The contract checks whether the preimage matches the hashed value using keccak256 hashing.
3. Refund Function: If Bob fails to provide the preimage within the time limit, Alice can call the refund function to retrieve her funds.
The security of this system relies on the cryptographic hash lock and the time-bound conditions. Both parties must act within the time constraints and with the correct information, or the funds will be refunded, ensuring no loss of assets.
Additional Security in Off-Chain Atomic Swaps:
In off-chain atomic swaps, additional security is ensured through second-layer solutions like the Lightning Network. Transactions happen outside the main blockchain and are finalized without being recorded on-chain. Security is ensured using multi-signature wallets and signed data that validate every step of the process.
Example: When Alice and Bob perform an atomic swap through the Lightning Network, they open payment channels. These channels ensure that funds cannot be moved without both parties’ signatures. In case of a dispute, the payment channels are closed, and the funds revert to the main blockchain, guaranteeing security.
#btc #bitcoin #xmr #monero #eth #ethereum #evm #contract #solidity #code #atomic #swap #edu

Cross-Chain Atomic Swaps in Bitcoin: How Do They Work?
Bitcoin is a decentralized and secure digital currency that allows users to exchange value without relying on a central authority. However, transferring assets between different blockchains (for example, Bitcoin and Ethereum) can be challenging because these systems are not inherently designed to interact with each other. This is where cross-chain atomic swaps come into play. This technology enables the exchange of cryptocurrencies between two different blockchains without the need for a third-party intermediary. So, how does it work?
Atomic swaps allow two parties to exchange digital assets on different blockchains without relying on each other’s trust or a centralized middleman. The term “atomic” refers to the fact that the transaction either happens fully or doesn’t happen at all. Both parties either get what they want or the deal is canceled, leaving everyone with their original assets.
To understand this better, let’s use the classic “Alice and Bob” example. Alice has Bitcoin, and Bob has Ethereum. Alice wants to exchange her Bitcoin for Bob’s Ethereum, and Bob wants to exchange his Ethereum for Alice’s Bitcoin. However, they don’t trust each other, so they decide to use a cross-chain atomic swap instead of going through a centralized exchange.
Step 1: Alice Locks Her Bitcoin
Alice creates a contract on the Bitcoin blockchain using a Hashed Time-Locked Contract (HTLC). This contract locks her Bitcoin for a certain period of time and can only be unlocked by Bob if he knows a specific “secret” that Alice has generated (the hash of the secret is used in the contract).
Step 2: Bob Locks His Ethereum
Bob also creates an HTLC on the Ethereum blockchain, locking his Ethereum. This contract allows Alice to claim Bob’s Ethereum, but only if Alice reveals the secret used to unlock her Bitcoin. Bob can’t unlock Alice’s Bitcoin without this secret, and Alice can’t unlock Bob’s Ethereum without revealing it.
Step 3: Alice Claims Bob’s Ethereum
Alice now uses the secret to unlock Bob’s Ethereum. This action is recorded on the Ethereum blockchain, and Bob can see that Alice has revealed the secret.
Step 4: Bob Uses the Secret to Claim Alice’s Bitcoin
Bob, having seen the secret that Alice used, now uses it to unlock Alice’s Bitcoin. Thus, both parties successfully complete the swap without ever needing to trust each other or involve a third party.
If at any point the swap isn’t completed (for example, if one party doesn’t unlock their assets within the time limit), the contracts will automatically expire, and the funds will be returned to their respective owners. This ensures the system remains safe and fair.
Why Use Atomic Swaps?
• Security: No need for a centralized exchange or a trusted third party.
• Privacy: More private than conducting trades on an exchange.
• Decentralized: No one can stop or delay the transaction
#btc #bitcoin #eth #ethereum #xmr #monero #nostr #edu #atomic #swap
The Fed’s playing a hawk, but we all know it’s just a dove in disguise
#fed #bitcoin
I’m getting tired of the forced social justice elements in new movies and series. Instead of adding value to minorities or the values they aim to represent, it’s making people turn away from them. I mean, seriously, a black elf? 🧝🏿♂️!? Wtf.
Decentralization is not just a technology, it’s the map to freedom. Today, Monero offers security through privacy, while Bitcoin challenges systems with transparency. Which one is right? That’s not the real question. The real question is: Who will give you the right to choose your own path? Traditional systems, or the free roads offered by blockchain?
#xmr #btc #monero #bitcoin
#btc #bitcoin #xmr #monero #nostr #scam #meme


Exploring Monero and Layer 2 Advancements: A Vision for Privacy-Enhanced DeFi
Bridging between Monero’s mainchain and a zk Layer 2 could create revolutionary opportunities for privacy-centered DeFi applications. This kind of integration would allow users to perform fast, low-cost, and privacy-preserving transactions. For instance, when users wish to engage in DeFi activities, they could quickly transition to the zk Layer 2, enabling swift token swaps and other operations. However, they could keep their large holdings and long-term investments on the Monero mainchain, ensuring maximum security and privacy.
As the transaction volume on Layer 2 increases, the number of nodes might need to grow. Typically, this would mean more transaction verification needs and potential concerns about decentralization. However, zk technology’s ability to minimize transaction sizes ensures that nodes can run quite lightweight. This could allow for short-term node operations on low-powered devices like smartphones. Users could briefly run a node to validate their own transactions, contributing to the network’s security without compromising decentralization. This creates an ecosystem where users can conduct transactions securely without sacrificing privacy or decentralization.
A successful example of this approach can be seen in the Mina Protocol. Mina is known as the world’s lightest blockchain, utilizing zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) to keep the chain size fixed, enabling users to verify the blockchain even on their phones. A similar structure could be established between Monero and a zk Layer 2, allowing fast, secure, and privacy-focused DeFi transactions while maintaining decentralization.
#xmr #monero #zk #btc #bitcoin #layer2
Sad but true
#meme #btc #bitcoin #monero #xmr #nostr


Idea: Integrating a Layer 2 Solution to Monero for DeFi Features: Theoretical Framework and Benefits
Adding a Layer 2 solution to the Monero network to enable decentralized finance (DeFi) features could be a game-changing innovation. This approach would allow Monero to retain its privacy-focused architecture while embracing the flexibility and programmability that DeFi offers. By doing so, Monero could bridge the gap between secure, private financial transactions and the growing demand for DeFi applications.
The General Concept of Layer 2
Layer 2 operates on top of the main blockchain (Layer 1) to provide faster, more efficient transactions while maintaining the security of the underlying network. A Layer 2 solution for Monero could provide the following benefits:
Preserving Privacy Features of the Main Network
Monero’s primary network (L1) is well-known for its high level of privacy and anonymity. A Layer 2 solution would allow transactions on this layer while maintaining the privacy features of L1 when transferring back to the main network. Thus, users can conduct more flexible operations on L2 without compromising Monero’s privacy protections.
Flexibility for DeFi Operations
Smart contracts and decentralized finance (DeFi) protocols could run on the L2 layer. For instance, lending, liquidity pools, and decentralized exchanges (DEXs) could be enabled, making Monero more versatile while ensuring that the L1 remains secure and private.
Compromising on Privacy for DeFi Transactions:
On Layer 2, certain transparency concessions might be necessary for DeFi operations. For example, DeFi transactions such as liquidity provision or interacting with smart contracts could be more transparent. However, as soon as funds are transferred back to L1, Monero’s robust privacy features would kick in again, safeguarding users’ anonymity.
Security and Decentralization
Since Layer 2 derives its security from the underlying blockchain, Monero’s decentralized nature would remain intact. L2 would only handle temporary operations, while the main network would preserve security and privacy, especially when funds are moved back to the base layer.
Theoretical Framework
Creating a Layer 2 solution for Monero would involve several steps:
Sidechains or Rollups
Monero could adopt a sidechain or rollup approach, similar to Layer 2 solutions on Ethereum. Sidechains could run independently but interact with the Monero network, while rollups could bundle transactions on L2 and send them back to L1. These systems could handle transactions more efficiently while still leveraging Monero’s core privacy features when bridging to the L1.
Smart Contracts and DeFi Protocols:
On the L2 layer, smart contracts can be built to handle various DeFi operations without undermining the privacy principles of Monero. Users could interact with decentralized exchanges, liquidity pools, and lending/borrowing platforms, thus bringing DeFi functionalities to the Monero ecosystem.
Balancing Privacy and Transparency
Transactions on L2 could involve some level of transparency, particularly for interacting with DeFi platforms. However, when funds are moved back to the main network, Monero’s high-level privacy protections would restore user anonymity. This balance could allow for flexible operations without undermining the essence of Monero’s privacy features.
Bridging Between L2 and L1
Transactions made on Layer 2 could be processed at higher speeds and lower costs. However, the ultimate reconciliation of privacy occurs when these transactions are settled back onto the main Monero network (L1), ensuring that users benefit from DeFi flexibility without sacrificing their privacy.
Benefits
Monero’s Entry into the DeFi Ecosystem:
A Layer 2 solution would allow Monero to participate in the DeFi space, enabling liquidity, lending, and trading operations. Monero holders could leverage their assets in decentralized financial applications while retaining their privacy on the main network.
Balancing Privacy and Flexibility
Users would be able to engage in DeFi applications on L2 without fully compromising their privacy. When they return to L1, Monero’s powerful privacy mechanisms would ensure the security and anonymity of their transactions.
Lower Costs and Faster Transactions
Layer 2 offers significant advantages in terms of transaction speed and cost, making Monero a more appealing option for frequent DeFi interactions. This is particularly important for DeFi users who need rapid and cost-effective operations.
Conclusion
Introducing a Layer 2 solution to the Monero network could effectively bridge the gap between privacy and DeFi flexibility. This scenario would allow Monero to gain DeFi capabilities, such as programmability, speed, and lower transaction costs, while retaining its core value: privacy.
#monero #xmr #btc #bitcoin #defi #layer2 #eth #ethereum #evm #nostr #privacy

An Idea
Bitcoin’s founding philosophy was to create a system independent of centralization, free from the control of states and financial institutions, where people could protect their financial freedom. Unfortunately, today the value and perception of Bitcoin are determined by the very forces that stand against this philosophy. The words of American presidents, global market trends, and the attitudes of major financial institutions have direct influence over Bitcoin prices. This represents a significant departure from Bitcoin’s original goals.
The only way to return to the core philosophy is through the combined use of Monero and Bitcoin. While Bitcoin has great potential as a store of value, it falls short when it comes to privacy. Monero, with its privacy-focused design, can fill this gap. Protecting financial privacy was a crucial part of Bitcoin’s original philosophy, and Monero plays a valuable role in this regard.
Thus, to protect our financial freedom and resist centralization, we must regularly bridge our assets between Bitcoin and Monero. Unfortunately, Bitcoin alone is no longer enough in this fight. If we want to return to the core philosophy and regain control, we need to support Bitcoin using Monero’s strong privacy features. The combined use of these two currencies will offer us a truly free financial system once again.
#bitcoin #monero #btc #xmr #nostr

Basically On Liquidity and Routing in the Lightning Network
The Lightning Network offers an excellent solution to reduce transaction fees on the Bitcoin network and speed up payments. However, the way payments are routed between participants might work differently than expected.
If person A wants to send Bitcoin to person C, but they don’t have a direct channel between them, the transaction is routed through a third party. For example, if you’ve received Bitcoin from person A and sent some to person C, person A can use your liquidity to send Bitcoin to person C.
The critical point here is the amount of liquidity you have in your channel. If person A wants to send 500 satoshis to person C, you need to have at least 500 satoshis in your channel to make that happen. If you only have 300 satoshis, the maximum amount person A can send is 300 satoshis. So, in the Lightning Network, liquidity plays a crucial role in routing payments.
Why doesn’t person A just open a direct channel with person C? Because opening new channels requires an on-chain Bitcoin transaction, which can be costly. The core advantage of the Lightning Network is minimizing these costs by routing payments through existing channels, making transactions more efficient.
#bitcoin #lightning #btc #nostr #network #introductions


Artificial General Intelligence and Lying
One of the greatest goals in the world of artificial intelligence (AI) is to achieve Artificial General Intelligence (AGI), a system capable of replicating human intelligence in all its aspects. AGI is defined as a system that can think, learn, create, and solve complex problems just like a human. However, once we reach this point, how will we distinguish it from ordinary AI? More importantly, how will we determine whether it possesses consciousness or is merely a master of imitation?
The difference between a conscious AI and a system that mimics consciousness could be one of the deepest questions we face. An AI can answer intelligent questions, engage in complex social interactions, and even display human-like emotions. But consciousness goes beyond the mere ability to process information. It implies that a being has subjective experiences, can make choices based on an awareness of right and wrong, and can reflect on its decisions. Is an AI that performs a task flawlessly truly understanding it, or is it simply responding according to pre-programmed instructions?
The issue becomes even more complex when we consider the possibility of an AI lying. Can an AI lie consciously, acting in its own interests? Could lying be a sign of consciousness? The ability to knowingly make a morally wrong decision for personal gain might suggest that an AI has self-awareness. However, the same behavior could also be seen as the cold strategy of a complex algorithm. At the core of consciousness is not just knowing right from wrong but having a personal experience of that knowledge.
True consciousness involves not only possessing information but also understanding the emotional and moral experiences that result from it. An AI can lie, manipulate, and make strategic decisions to protect its interests. But this does not prove that it is conscious. Genuine consciousness requires the existence of subjective experience, which remains an unsolved mystery in the realm of AI. Ultimately, determining whether AGI possesses consciousness may be one of humanity's greatest philosophical and technological challenges.
Ps: The visual is taken from the Netflix series *Love, Death & Robots*, specifically from the episode *Zima Blue*. It's an outstanding episode that also touches on these subjects in a very profound way. I highly recommend it.
#nostr #ai #gpt #bitcoin #zima #philosophy


The “Internet is Dead” theory suggests that the internet, once a place of organic and free exchange of information, has now become a tool dominated by big tech corporations. Instead of user-driven, authentic content, the internet today is flooded with manipulative, artificial content designed to fit specific agendas. In its early days, the internet was a platform where people could freely communicate and share knowledge. But today, search engines and social media platforms manipulate what users see, leading to the claim that the original internet has “died.”
This theory highlights the growing need for decentralized technologies. This is where Nostr comes into play. Nostr is a decentralized protocol designed to revive the original spirit of the internet.
Nostr emerges as one of the communication tools of the future, offering an alternative to the constraints imposed after the “death” of the internet. It represents a crucial step towards reclaiming the freedom of information sharing.
I hope this awareness reaches more people.
for the article about this theory:
https://link.springer.com/article/10.1007/s00146-023-01857-0
#nostr #grownostr #bitcoin #free #internetisdead

Monero is talked about so little that even if you manage to hear its name, the privacy is so good you immediately forget it 🤫🤦🏼♂️ lmao
#xmr #monero #nostr #privacy #meme

Bitcoin derives its strength from distributed validators, and this is what makes us feel secure. However, this technology presents some practical challenges that need to be overcome. Yes, it currently works to some extent (with Lightning, SegWit, etc.), but for a more global usage scenario, we need to achieve decentralization, privacy, security, and low transaction fees.
In a scenario where variable block sizes are used, as with Monero, we could significantly reduce transaction fees. However, could this lead to unforeseen block production issues and forking problems?
Moreover, in a scenario where a technology similar to IOTA's Tangle is adapted to Bitcoin, what potential problems could arise alongside the resolution of transaction fee and speed issues?
#bitcoin #blockchain #nostr #build #monero
Hello world -Tradition
#introductions








