Xiaomi's new smart door lock can disguise your voice.
Xiaomi has launched a new smart door lock in China that includes an intercom voice changer, letting you disguise your identity while speaking with someone at the door.
 This is closed source, so not that great. But it's still a cool idea.. they should add it to phones.
Source:
This is closed source, so not that great. But it's still a cool idea.. they should add it to phones.
Source: 
 This is closed source, so not that great. But it's still a cool idea.. they should add it to phones.
Source:
This is closed source, so not that great. But it's still a cool idea.. they should add it to phones.
Source: 
Notebookcheck
Xiaomi Smart Door Lock 2: New model with voice changer unveiled
Xiaomi has revealed the Smart Door Lock 2 Cat Eye Edition, which is now available in China. The smart home device has an integrated doorbell and 2M...

 Not only will this podcast entertain and educate you, but you'll also learn about the Paradox of Monero.
What if I told you that by making restrictions, it actually cripples the ability to regulate it by under their own legal systems?
Web:
Not only will this podcast entertain and educate you, but you'll also learn about the Paradox of Monero.
What if I told you that by making restrictions, it actually cripples the ability to regulate it by under their own legal systems?
Web: 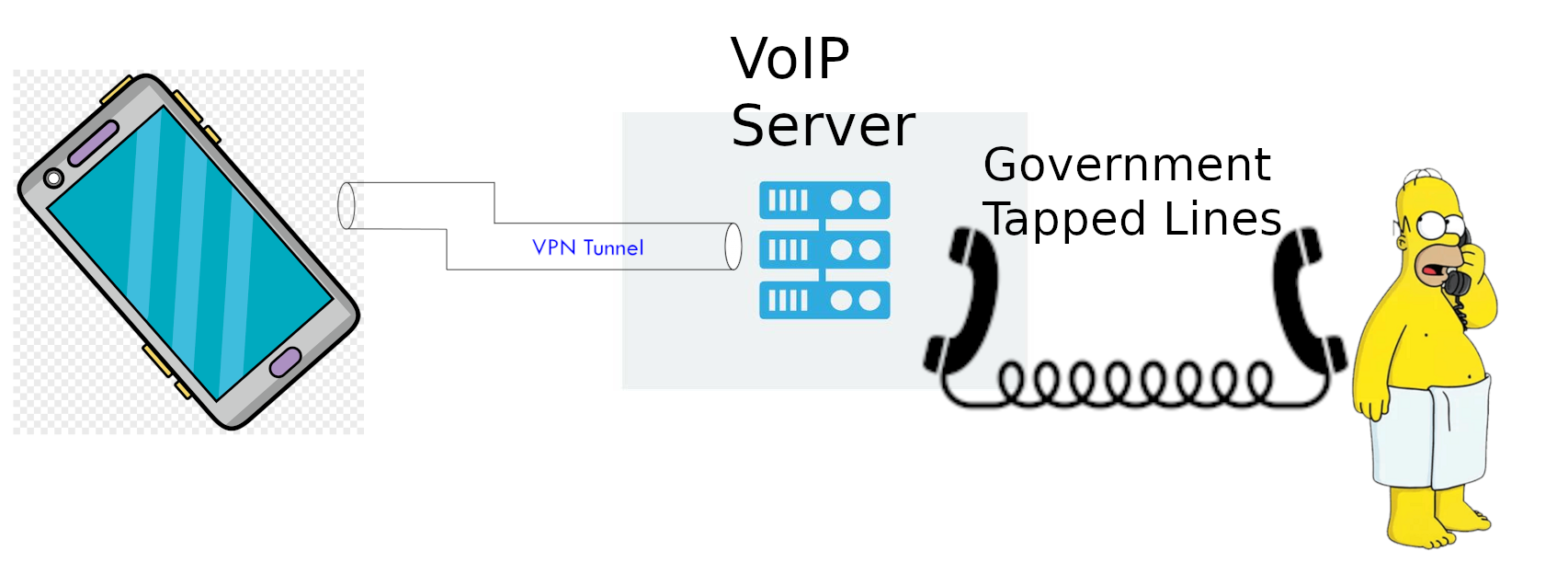 VoIP: Hides from the phone company the LOCATION of the texter, but NOT the content.
VPN: Hides from the VoIP provider your home IP, but NOT the SMS content
Hotspots (& Faraday bags): Hide from the celltower giving you service, where you go when it's bagged.
If you only use the hotspot outside the faraday bag, when you're outside your home,
And only use SMS with VoIP and a VPN, then you're as anonymous as SMS can be. But even better, is reduce/stop using SMS.
VoIP: Hides from the phone company the LOCATION of the texter, but NOT the content.
VPN: Hides from the VoIP provider your home IP, but NOT the SMS content
Hotspots (& Faraday bags): Hide from the celltower giving you service, where you go when it's bagged.
If you only use the hotspot outside the faraday bag, when you're outside your home,
And only use SMS with VoIP and a VPN, then you're as anonymous as SMS can be. But even better, is reduce/stop using SMS.

 What if I told you that the history of how KYC laws came to the US, was even more corrupt than the laws themselves?
In this short but sweet 10-minute podcast, Shadow Rebel breaks down the dark history of physically threatening Congress members to convince them to pass this... and worse:
Web:
What if I told you that the history of how KYC laws came to the US, was even more corrupt than the laws themselves?
In this short but sweet 10-minute podcast, Shadow Rebel breaks down the dark history of physically threatening Congress members to convince them to pass this... and worse:
Web: