I personally don't trust hardware wallets.
Especially if it's closed source. If you got a large enough amount of cryptocurrency to justify a hardware wallet, then I'd:
a) Split it up into a hot wallet for daily stuff, and a large cold wallet with the rest
b) Cold wallet could be KeePass inside VeraCrypt Drives, with a fake password for a hidden drive
c) With an epic amount of cryptocurrency, (this is not the vast majority of the readers), using a virtual machine, with the crypto wallets on the host, and the purchases inside the VM.
d) With a medium amount of cryptocurrency, our fingerprint app also gives you the added benefit of GUI isolation for Linux Distros like Mint, which don't have it for x11 displays. In other words, the web browser isn't seeing your keepass and wallets.

SimplifiedPrivacy.com
npub14slk...t5d6
Give me Liberty, or Give me Death. HydraVeil is our Revolutionary New Linux app that allows you to create different isolated profiles, to resist AI Browser Fingerprinting from Cloudflare & Big Tech. Another feature of HydraVeil is routing your traffic though your choice of WireGuard or a Tor->Socks5 proxy (to evade Tor blocks), and to fool CDN packet speed tracing with different IPs for each profile.
Additionally, we provide VPN service for Android, iPhone, Windows, Mac, and Routers. Tune in to our Podcast to combat Big Tech surveillance. Help me, help you.
Hashtags: #Cypherpunk, Open source, #Linux, DeGoogled Phones, self-hosted services, #Monero, #Security, and more!
Myth: Browsers can Fool AI by “Spoofing”
Reality: Spoofing is just lying with your words.
 Even back in 2016, Google could detect spoofing:
Even back in 2016, Google could detect spoofing:
 Google gives your client a challenge to draw. This image is from their (now ancient tech) 2016 whitepaper: [12]
Google gives your client a challenge to draw. This image is from their (now ancient tech) 2016 whitepaper: [12]
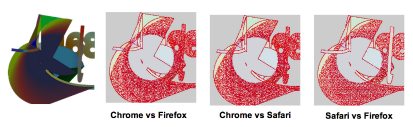 Then these drawings are analyzed at the pixel level,
Then these drawings are analyzed at the pixel level,
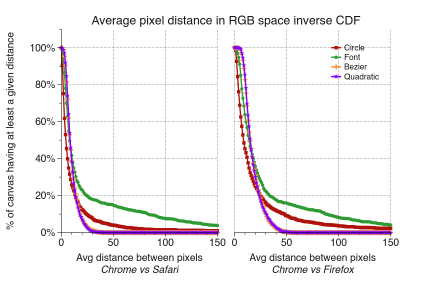 And compared to what that browser, OS, and hardware can normally produce,
And compared to what that browser, OS, and hardware can normally produce,
 This is why the Chameleon Browser Extension whitelists Google and Cloudflare [14]
This is why the Chameleon Browser Extension whitelists Google and Cloudflare [14]
 Because their app, and those like it, just LIE with “user-agents” (their words)
Because their app, and those like it, just LIE with “user-agents” (their words)
 You can’t hide the fundamental nature of browsers,
You can’t hide the fundamental nature of browsers,
 For example, when someone asked if they should block the specific type of JavaScript (that hides your screen size), the GrapheneOS dev said: [10]
For example, when someone asked if they should block the specific type of JavaScript (that hides your screen size), the GrapheneOS dev said: [10]
 In other words, they fingerprint you based on what you choose to block,
In other words, they fingerprint you based on what you choose to block,
 And if you turn off JavaScript,
And if you turn off JavaScript,

 Enjoy the rest of the fun meme slideshow or get sources:
Enjoy the rest of the fun meme slideshow or get sources:
 Even back in 2016, Google could detect spoofing:
Even back in 2016, Google could detect spoofing:
 Google gives your client a challenge to draw. This image is from their (now ancient tech) 2016 whitepaper: [12]
Google gives your client a challenge to draw. This image is from their (now ancient tech) 2016 whitepaper: [12]
 Then these drawings are analyzed at the pixel level,
Then these drawings are analyzed at the pixel level,
 And compared to what that browser, OS, and hardware can normally produce,
And compared to what that browser, OS, and hardware can normally produce,
 This is why the Chameleon Browser Extension whitelists Google and Cloudflare [14]
This is why the Chameleon Browser Extension whitelists Google and Cloudflare [14]
 Because their app, and those like it, just LIE with “user-agents” (their words)
Because their app, and those like it, just LIE with “user-agents” (their words)
 You can’t hide the fundamental nature of browsers,
You can’t hide the fundamental nature of browsers,
 For example, when someone asked if they should block the specific type of JavaScript (that hides your screen size), the GrapheneOS dev said: [10]
For example, when someone asked if they should block the specific type of JavaScript (that hides your screen size), the GrapheneOS dev said: [10]
 In other words, they fingerprint you based on what you choose to block,
In other words, they fingerprint you based on what you choose to block,
 And if you turn off JavaScript,
And if you turn off JavaScript,


Fingerprinting Myths: Spoofin, alt-Browers, VMs | Simplified Privacy
Myths of Privacy!
Avoid Fake (or Unrealistic) Solutions, and Learn What to Do
 In 2019, Google said fingerprinting was wrong,
In 2019, Google said fingerprinting was wrong,
 But now it's okay,
But now it's okay,
 You can’t hide the fundamental nature of browsers,
You can’t hide the fundamental nature of browsers,
 This NEW article will summarize technical whitepapers as fun easy memes, and give you a comprehensive overview of what nobody ever told you regarding digital privacy:
This NEW article will summarize technical whitepapers as fun easy memes, and give you a comprehensive overview of what nobody ever told you regarding digital privacy:

 In 2019, Google said fingerprinting was wrong,
In 2019, Google said fingerprinting was wrong,
 But now it's okay,
But now it's okay,
 You can’t hide the fundamental nature of browsers,
You can’t hide the fundamental nature of browsers,
 This NEW article will summarize technical whitepapers as fun easy memes, and give you a comprehensive overview of what nobody ever told you regarding digital privacy:
This NEW article will summarize technical whitepapers as fun easy memes, and give you a comprehensive overview of what nobody ever told you regarding digital privacy:
Fingerprinting Myths: Spoofin, alt-Browers, VMs | Simplified Privacy

Age 15 - 20:
I'm cooler than everyone because of my taste in music
Age 20 - 25:
I'm cooler than everyone because of my political beliefs
Age 30s+:
I can never win at politics. These beliefs will never be cool.
But I'm strong, because of my actions
Donald Trump pushed forward a budget with spending increases
So,
He does not care about the cutting back
Yet,
He's got Elon Musk firing IRS guys, to make government more “efficient”
Therefore,
It is logical to assume that firing workers isn't about reducing spending, but getting Peter Thiel & Elon Musk's AI to replace the workers. AI as the backbone of the government.
This would,
Make AI-run government more efficient at enslaving and controlling you.
Haters try to attack me by saying:
"People don't care about privacy at the level of your VPN"
And that's my point! As you navigate life, people will constantly try to force you to use unprivate services that won't work in Tor Browser. And to download and configure separate isolated forked browsers, just because your co-worker sends you daily Google docs, or your high-school buddy will only talk on Facebook messenger, is not realistic for 99% of people.
So our app is NOT designed for the masses, it's designed to protect you FROM the sheep
Alt + Spacebar
That's all you need to have AI record your voice,
With the all new Microsoft Windows Copilot Press to Talk AI recorder! [1]
Next maybe they'll remove the Alt key, so just hit spacebar and we'll film... Or an Elon Musk brainchip to better comply with X's terms and conditions..
Or: You could Install Linux Mint using a cheap USB stick and be up and running this weekend.
Hit up the Linux Section of our Site:
[2]
News Source:
[1] 
Linux | Simplified Privacy

The Verge
Copilot gets a press-to-talk hotkey on Windows.
Microsoft is rolling out a new way to summon Copilot in Windows for voice interactions. The new Copilot for Windows app now has a keyboard shortcut...
Shout-out EP with Spam Control for Groups.
Unfortunately due to the severity of attacks on our room, we have to wait for his new "knocking" feature, which isn't out yet.
View quoted note →
I hate AI
But I'm getting exhausted with explaining the political and privacy risks of AI.
Maybe I should I automate my explanations?
Although reposting your own stuff really makes one look arrogant,
It's worth the risk to me, if it helps you.
View quoted note →
Crypto-Anarchy 101: (as Pictures)
Get one easy to understand Picture for each protocol:
 Signal
Signal is on the CIA contractor Amazon, and tries to use “sealed sender” to hide the metadata. However it’s flawed.
Signal
Signal is on the CIA contractor Amazon, and tries to use “sealed sender” to hide the metadata. However it’s flawed.
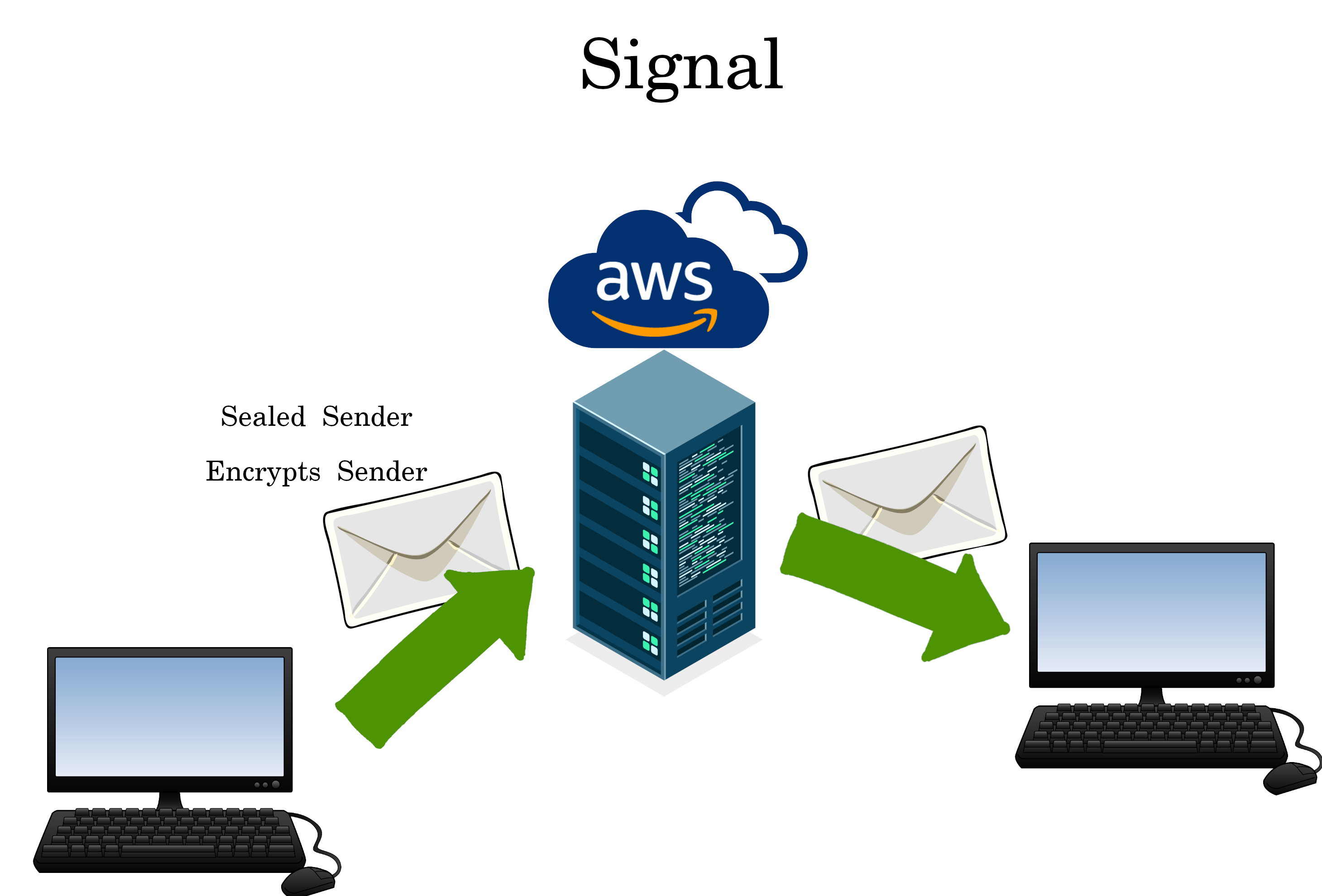 Learn Tips for Signal:
~~
XMPP
XMPP is well-trusted, but the OMEMO encryption dies with the domain it’s linked to. This means XMPP is nothing more than end-to-end encrypted email (with rotating keys).
Learn Tips for Signal:
~~
XMPP
XMPP is well-trusted, but the OMEMO encryption dies with the domain it’s linked to. This means XMPP is nothing more than end-to-end encrypted email (with rotating keys).
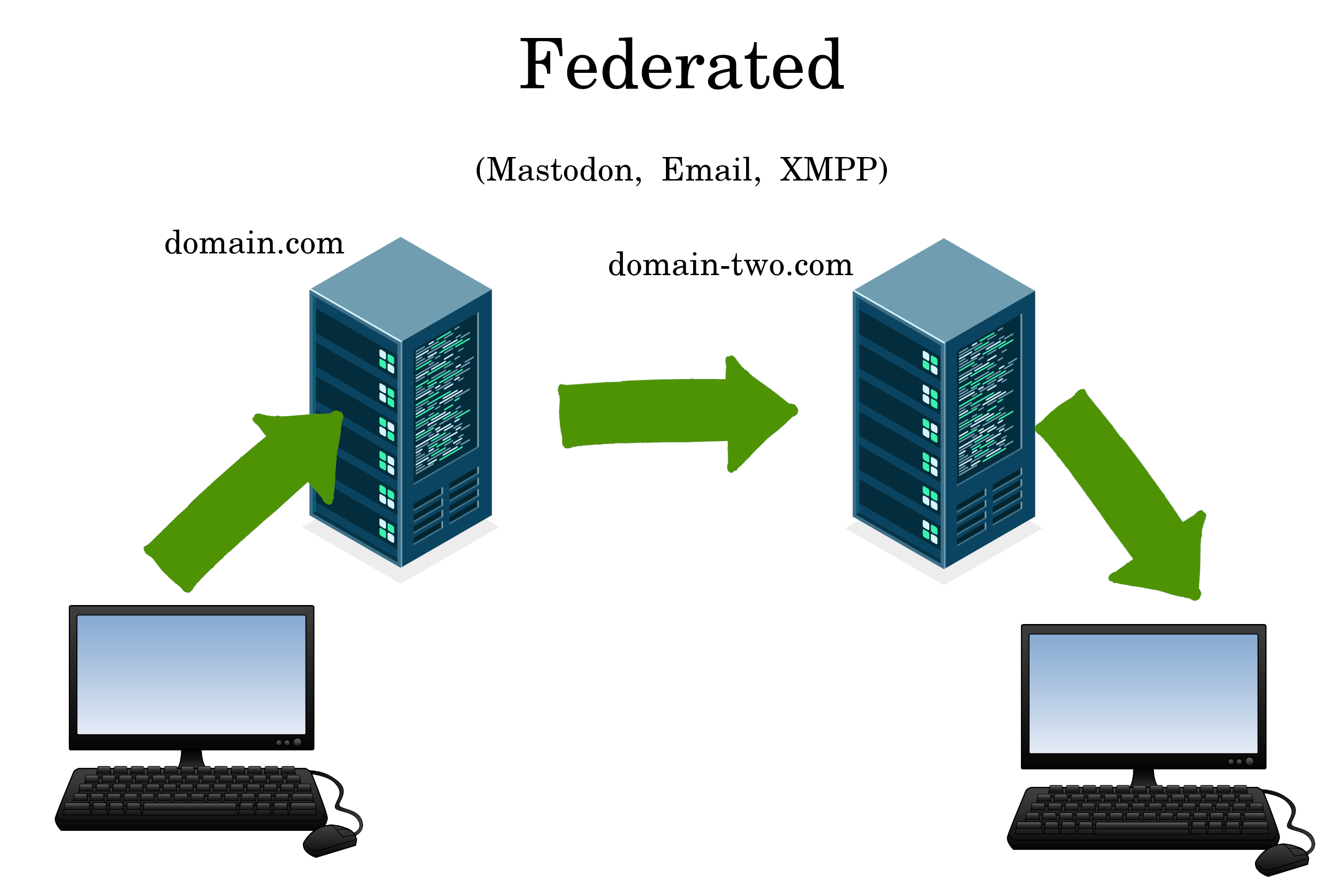 Learn about XMPP here: https://video.simplifiedprivacy.com/xmpp/
~~
SimpleX
SimpleX splits up messages into a give and take. It’s similar to a double-federated model.
Learn about XMPP here: https://video.simplifiedprivacy.com/xmpp/
~~
SimpleX
SimpleX splits up messages into a give and take. It’s similar to a double-federated model.
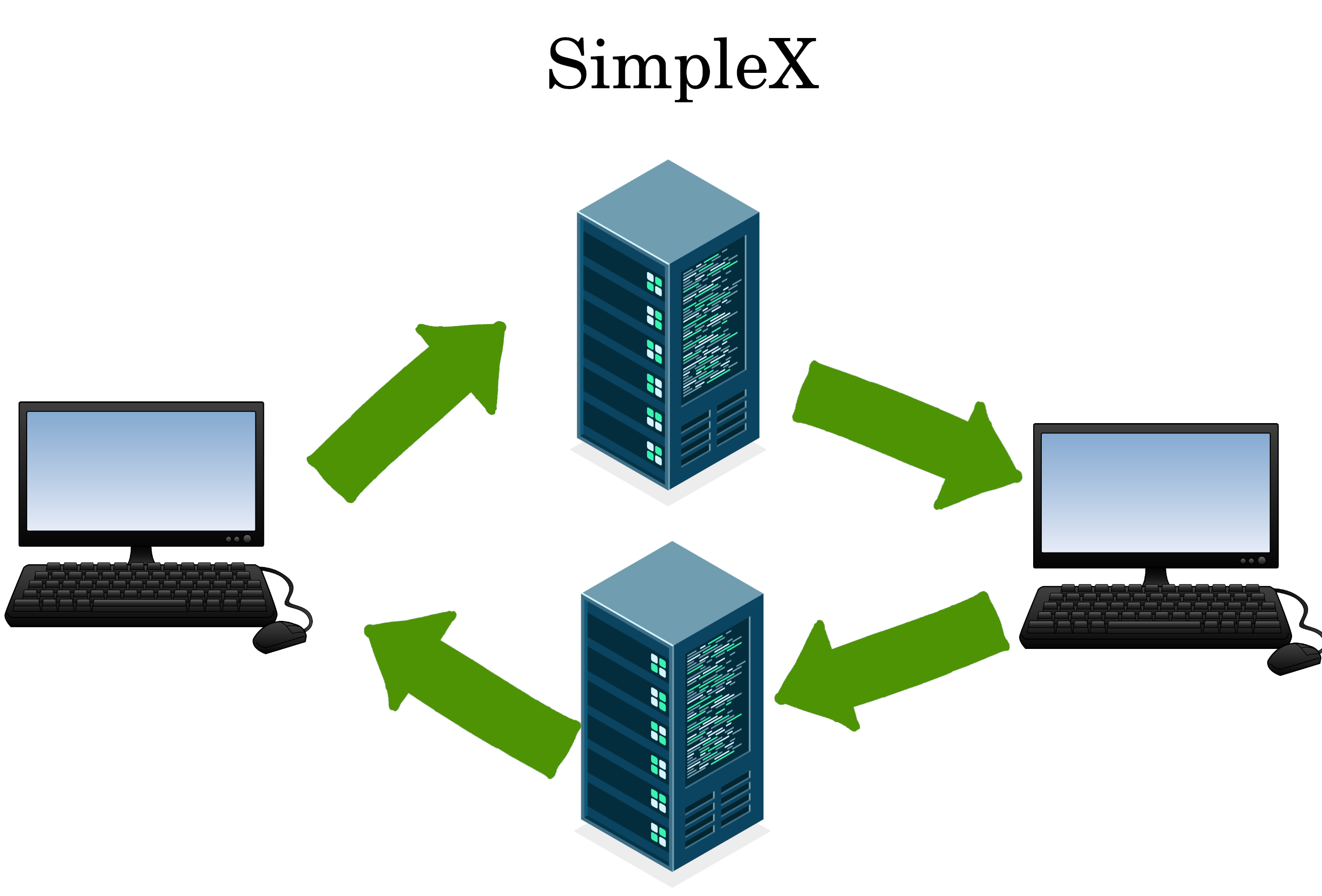 SimpleX users can change the relays mid-conversation, but new incoming messages are tied to government domains that can be censored.
~~
Session
Session transcends physical locations through unique DNS, onion-routing, and data stored in a BitTorrent database.
SimpleX users can change the relays mid-conversation, but new incoming messages are tied to government domains that can be censored.
~~
Session
Session transcends physical locations through unique DNS, onion-routing, and data stored in a BitTorrent database.
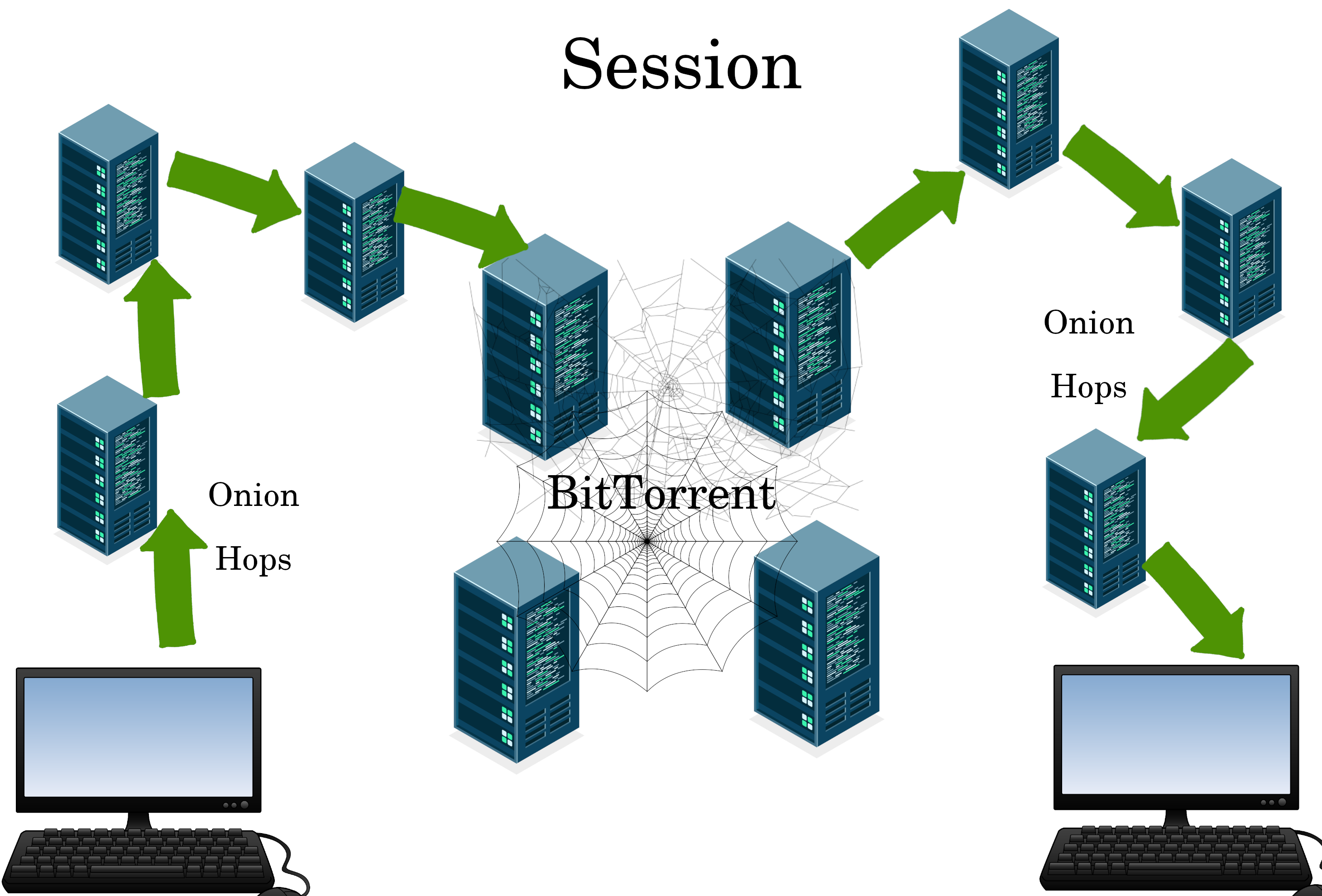 We use Session for an uncensored email list:
~~
Arweave
Arweave is to websites, what Session is to messages. Both have nodes being paid in a crypto to host a BitTorrent database. The main difference is Arweave stores the data DIRECTLY ON the blockchain.. and potentially forever.
We use Session for an uncensored email list:
~~
Arweave
Arweave is to websites, what Session is to messages. Both have nodes being paid in a crypto to host a BitTorrent database. The main difference is Arweave stores the data DIRECTLY ON the blockchain.. and potentially forever.
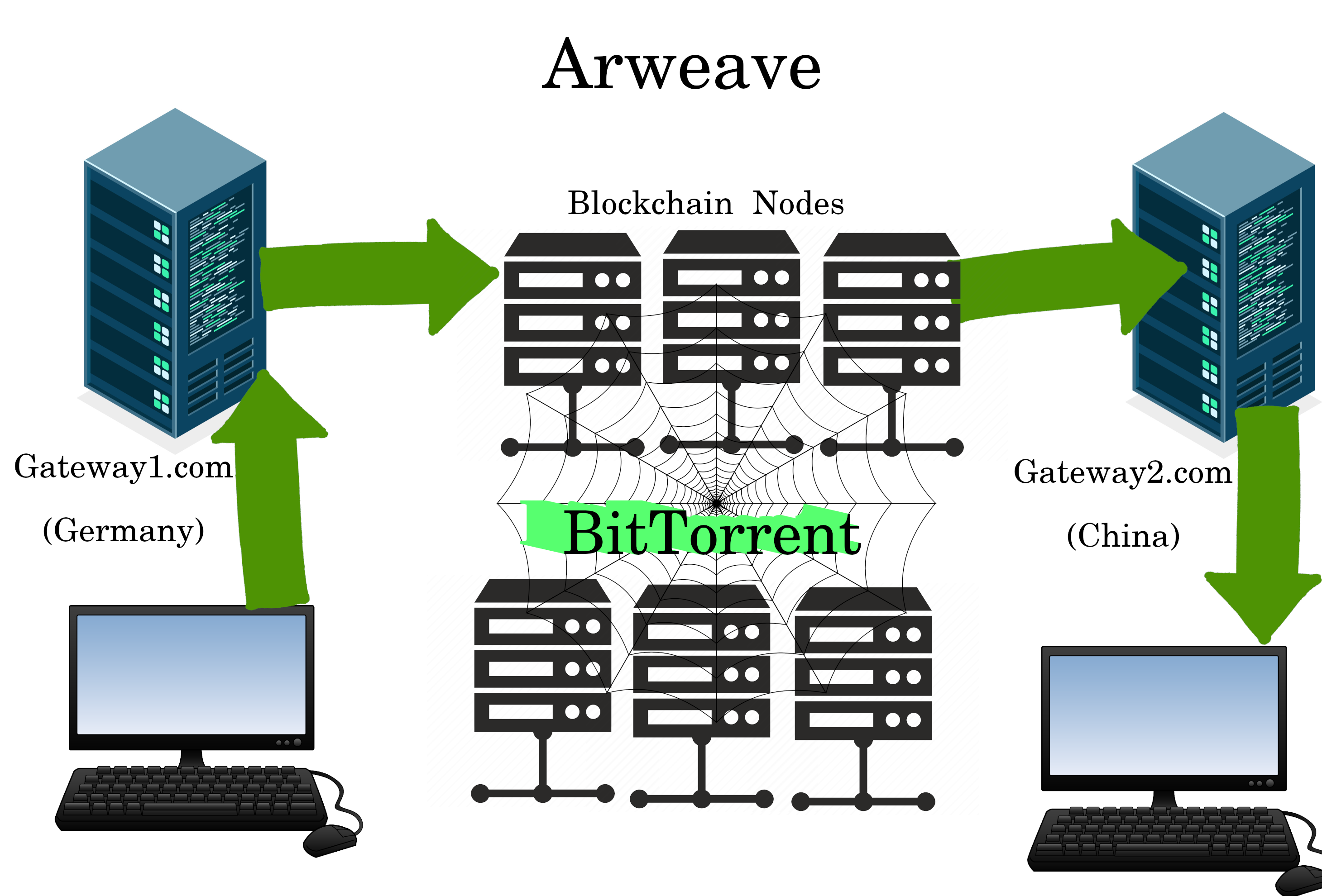 Learn about Arweave here:
~~
Nostr
Nostr has no blockchain. Users cryptographically sign messages, and then directly post and receive from relays.
Learn about Arweave here:
~~
Nostr
Nostr has no blockchain. Users cryptographically sign messages, and then directly post and receive from relays.
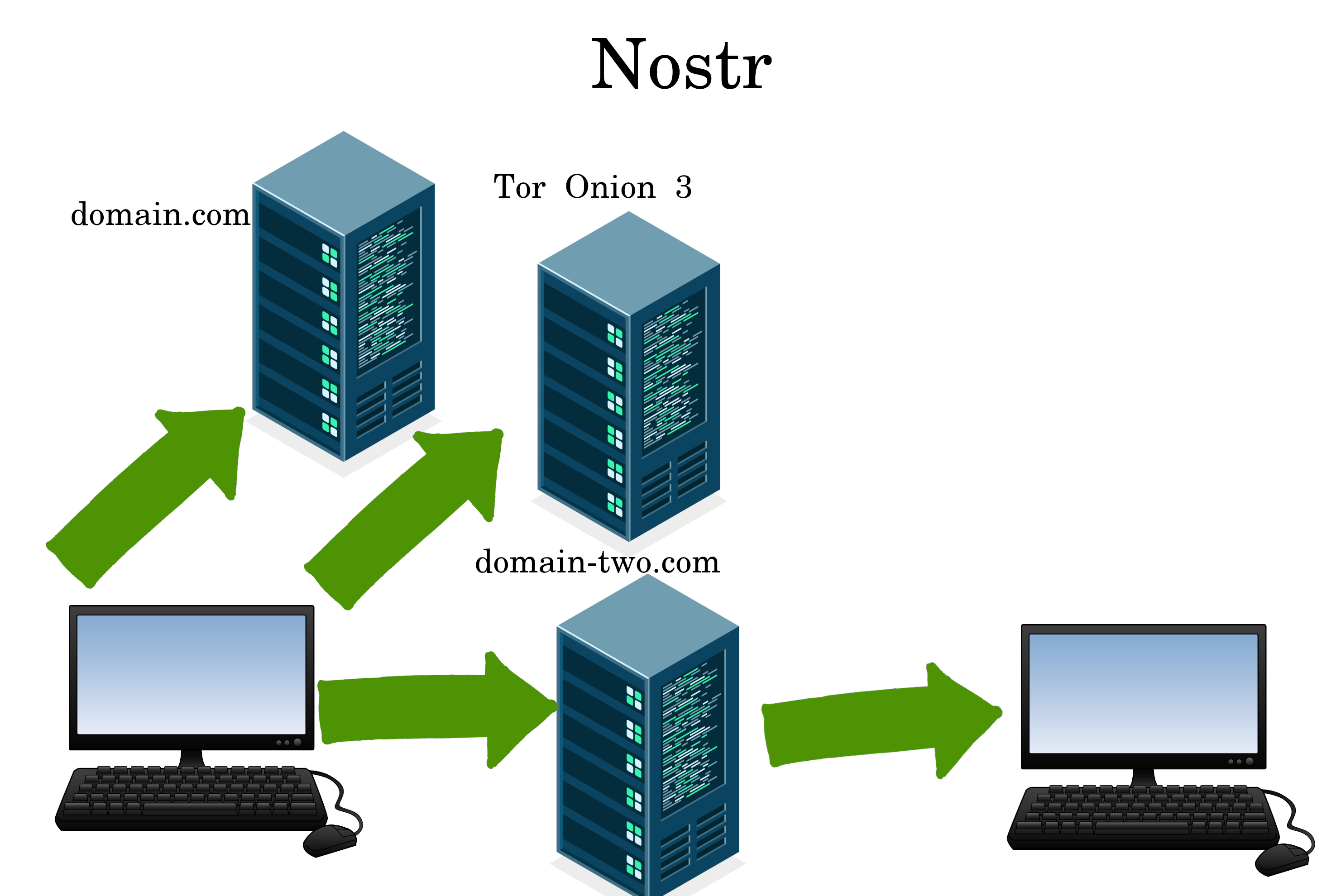 Learn about Nostr here: https://video.simplifiedprivacy.com/nostrtutorial
~~
Bastyon
Bastyon is the “Russian Nostr” because it’s good at penetrating Firewalls. Unlike Nostr, Bastyon has a blockchain, and home client computers can directly and easily act as nodes (which makes it tough for governments to block).
Learn about Nostr here: https://video.simplifiedprivacy.com/nostrtutorial
~~
Bastyon
Bastyon is the “Russian Nostr” because it’s good at penetrating Firewalls. Unlike Nostr, Bastyon has a blockchain, and home client computers can directly and easily act as nodes (which makes it tough for governments to block).
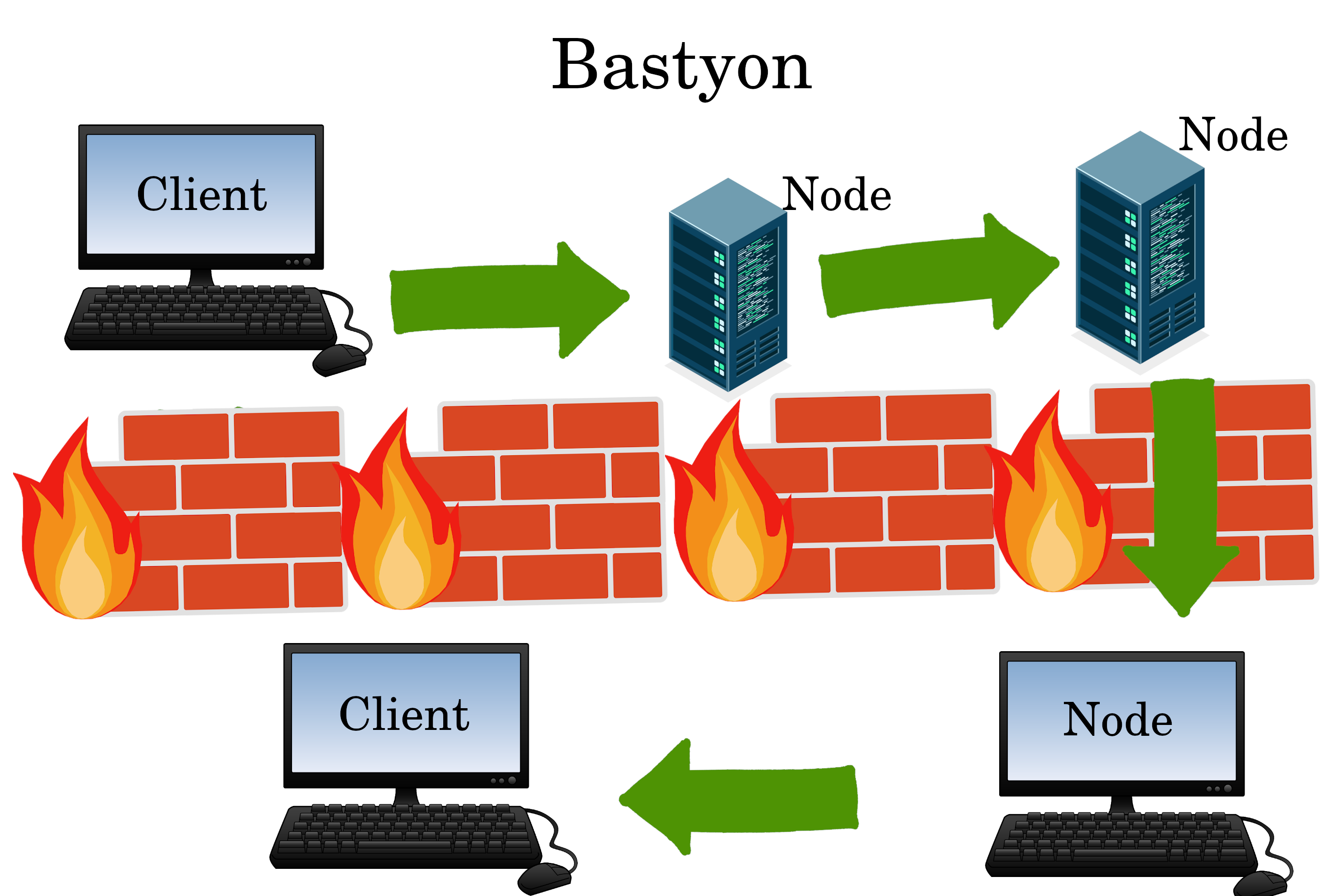 Learn about Bastyon here:
~~
Bitcoin Lightning
Lightning Channels are like an Abacus, keeping track of who owes who on the Layer 1. It does multiple hops for privacy, similar to Tor.
Learn about Bastyon here:
~~
Bitcoin Lightning
Lightning Channels are like an Abacus, keeping track of who owes who on the Layer 1. It does multiple hops for privacy, similar to Tor.
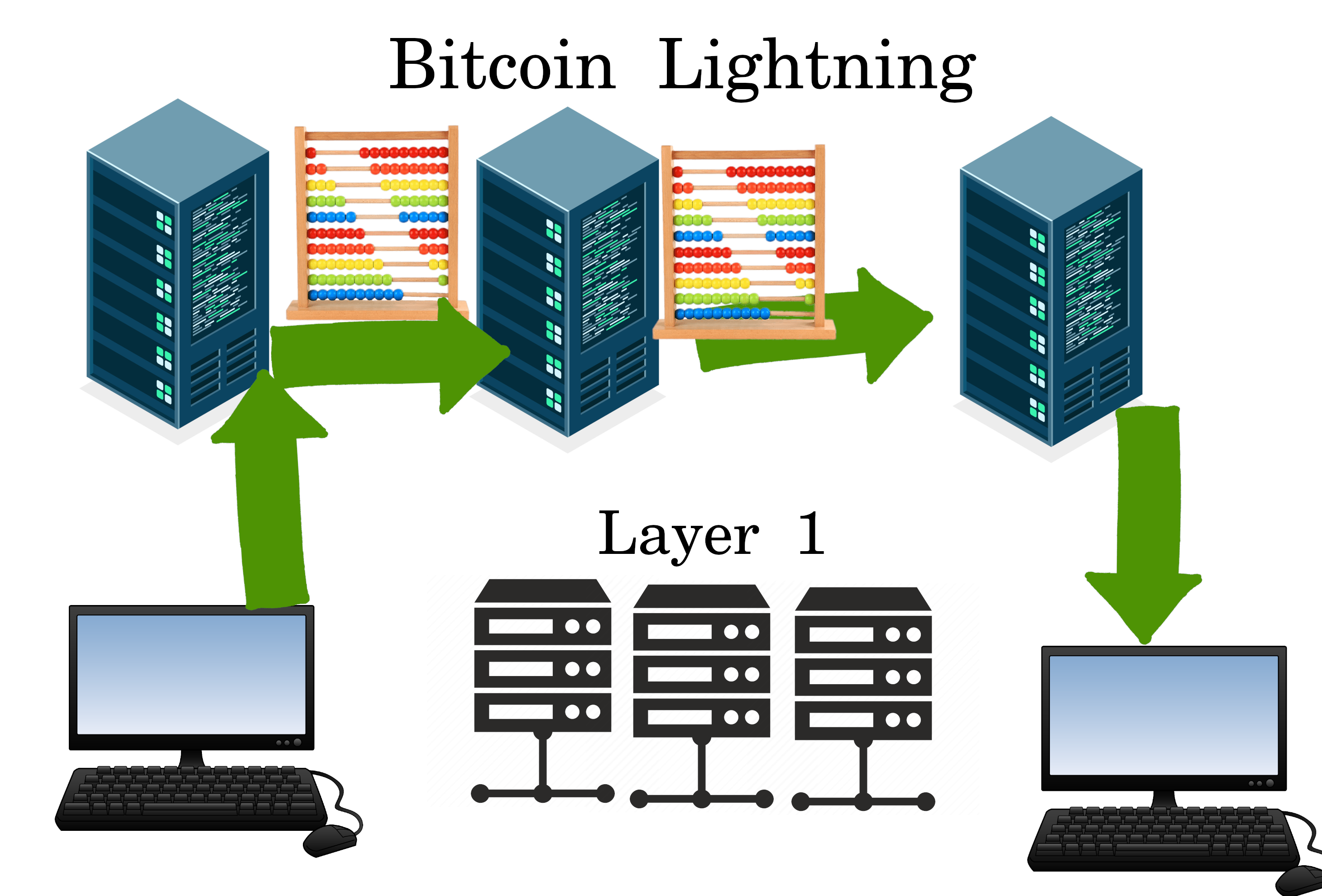 ~~
Monero
Monero hides the data by having fake “decoy” signers. Then having the reciever download and scan all the transactions for a match.
~~
Monero
Monero hides the data by having fake “decoy” signers. Then having the reciever download and scan all the transactions for a match.
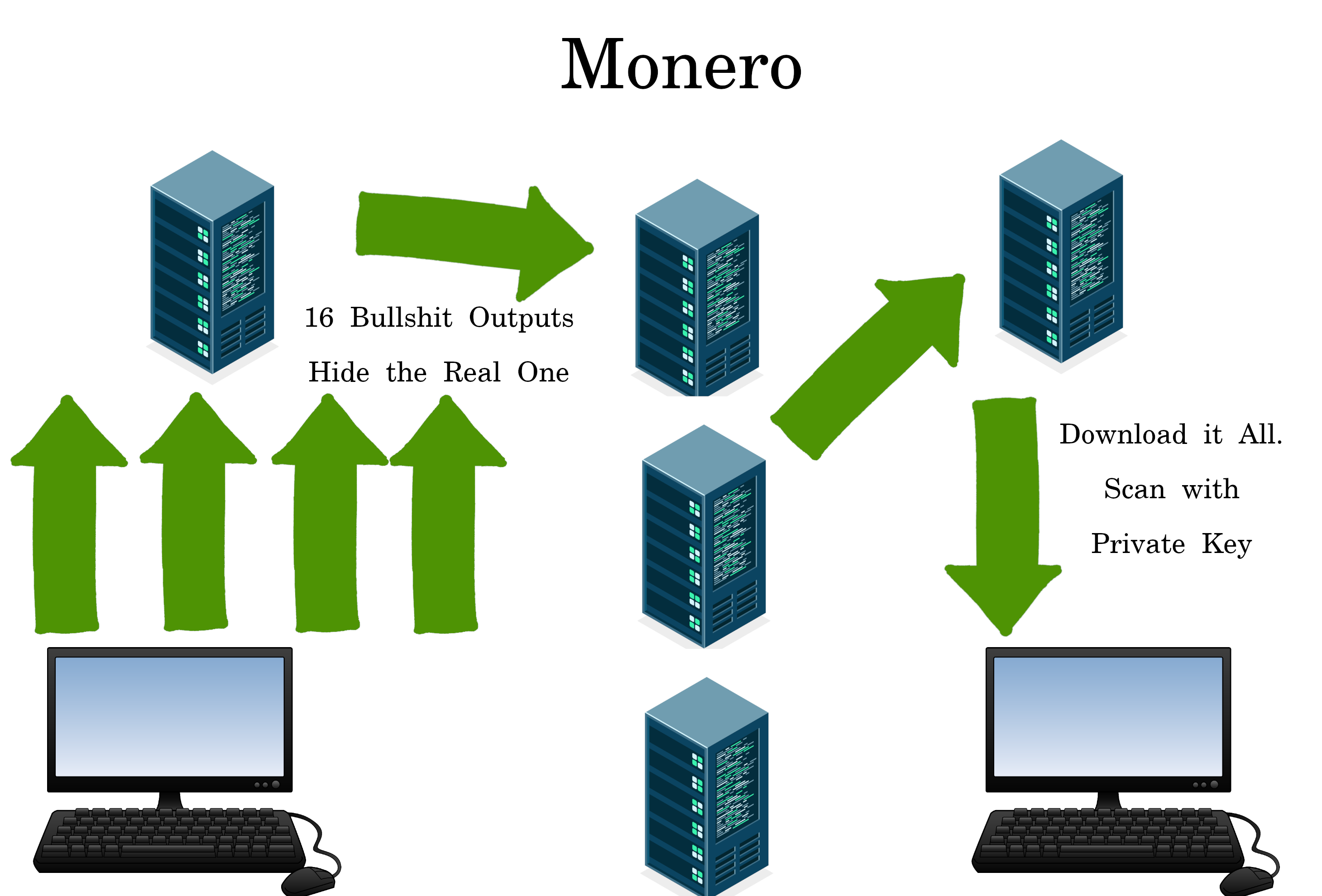 Learn about Monero here: https://video.simplifiedprivacy.com/how-xmr-works/
~~
The NSA Taps the Ocean Cables
Learn about Monero here: https://video.simplifiedprivacy.com/how-xmr-works/
~~
The NSA Taps the Ocean Cables
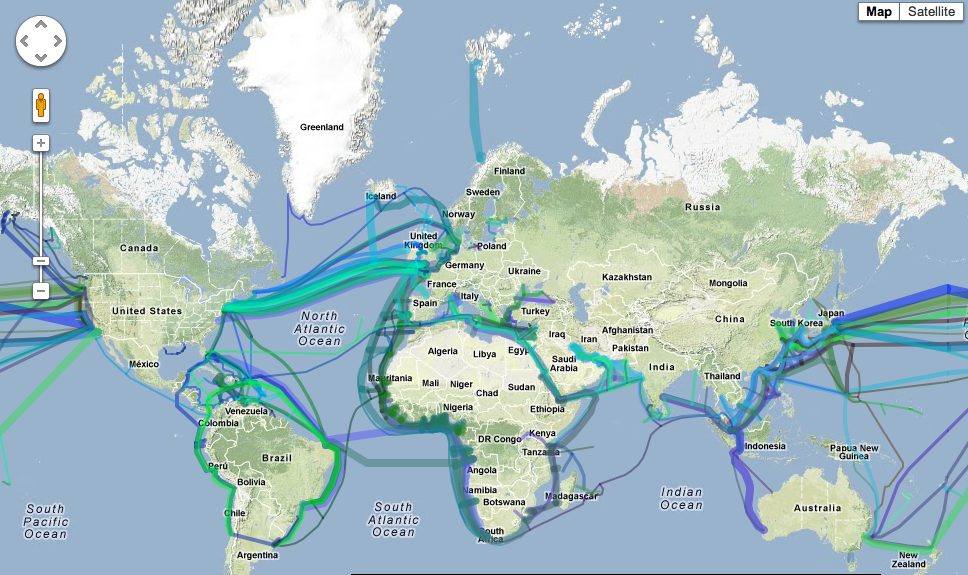
 Simplified Privacy
Our VPN allows for split traffic with fake decoy outputs, (like the “Monero of VPNs”). So your home ISP and the ocean cables see different packet sizes.
Simplified Privacy
Our VPN allows for split traffic with fake decoy outputs, (like the “Monero of VPNs”). So your home ISP and the ocean cables see different packet sizes.
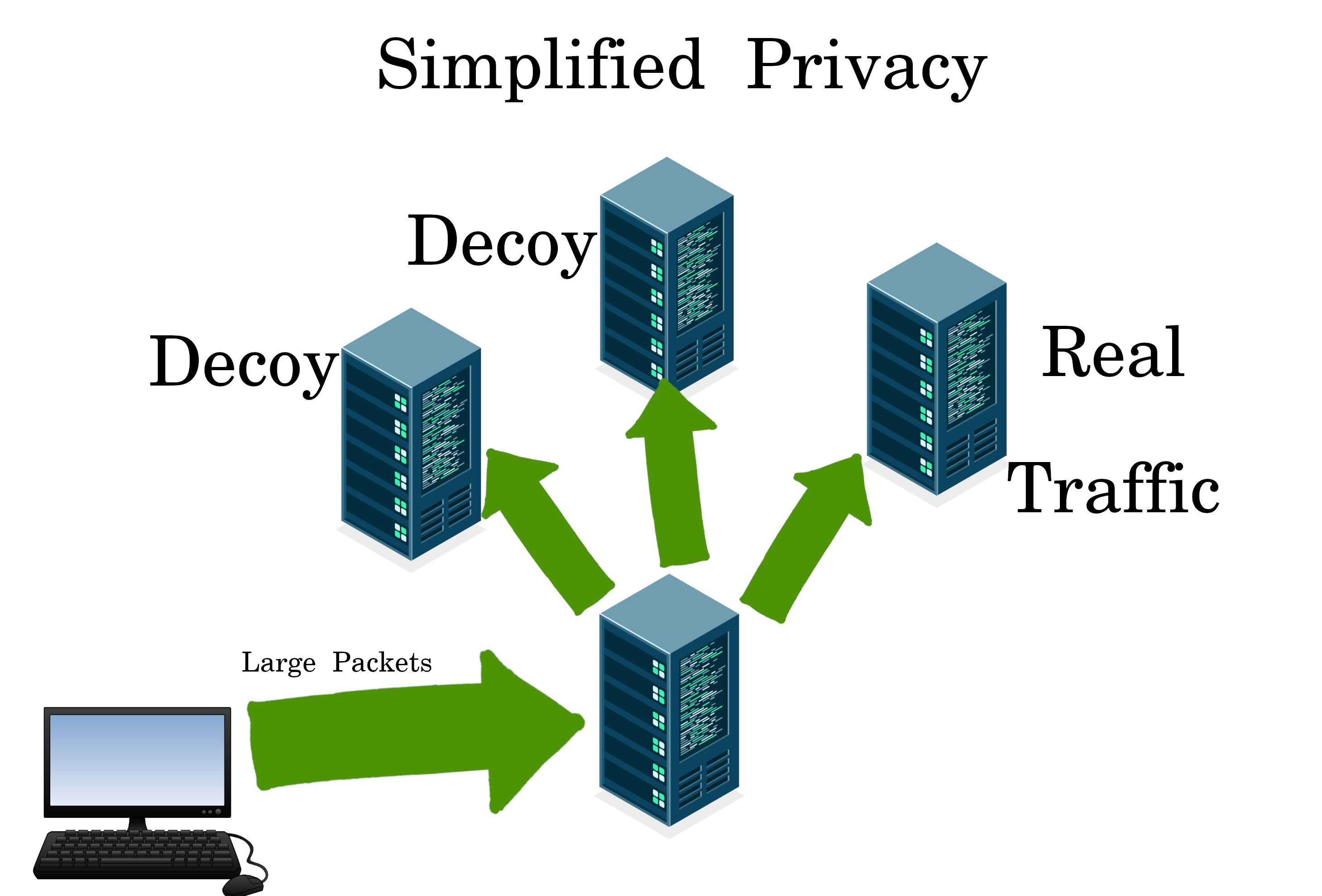 Proof of Concept Beta
The VPN currently supports split-traffic, but the cover traffic is manual. For example, opening a 2nd profile with a 12-hour music list, which is very easy with a bookmark homepage. One advantage of manual, is the server doesn’t know if it’s cover traffic or not. But we will be automating the cover traffic in future beta rounds.
Learn About Our Split Approach:
Proof of Concept Beta
The VPN currently supports split-traffic, but the cover traffic is manual. For example, opening a 2nd profile with a 12-hour music list, which is very easy with a bookmark homepage. One advantage of manual, is the server doesn’t know if it’s cover traffic or not. But we will be automating the cover traffic in future beta rounds.
Learn About Our Split Approach:
 Signal
Signal is on the CIA contractor Amazon, and tries to use “sealed sender” to hide the metadata. However it’s flawed.
Signal
Signal is on the CIA contractor Amazon, and tries to use “sealed sender” to hide the metadata. However it’s flawed.
 Learn Tips for Signal:
Learn Tips for Signal: Tips for Signal | Simplified Privacy
 Learn about XMPP here: https://video.simplifiedprivacy.com/xmpp/
~~
SimpleX
SimpleX splits up messages into a give and take. It’s similar to a double-federated model.
Learn about XMPP here: https://video.simplifiedprivacy.com/xmpp/
~~
SimpleX
SimpleX splits up messages into a give and take. It’s similar to a double-federated model.
 SimpleX users can change the relays mid-conversation, but new incoming messages are tied to government domains that can be censored.
~~
Session
Session transcends physical locations through unique DNS, onion-routing, and data stored in a BitTorrent database.
SimpleX users can change the relays mid-conversation, but new incoming messages are tied to government domains that can be censored.
~~
Session
Session transcends physical locations through unique DNS, onion-routing, and data stored in a BitTorrent database.
 We use Session for an uncensored email list:
We use Session for an uncensored email list: Why Session’s censorship resistance is the strongest | Simplified Privacy
 Learn about Arweave here:
Learn about Arweave here: How Arweave Offers Amazing Privacy | Simplified Privacy
 Learn about Nostr here: https://video.simplifiedprivacy.com/nostrtutorial
~~
Bastyon
Bastyon is the “Russian Nostr” because it’s good at penetrating Firewalls. Unlike Nostr, Bastyon has a blockchain, and home client computers can directly and easily act as nodes (which makes it tough for governments to block).
Learn about Nostr here: https://video.simplifiedprivacy.com/nostrtutorial
~~
Bastyon
Bastyon is the “Russian Nostr” because it’s good at penetrating Firewalls. Unlike Nostr, Bastyon has a blockchain, and home client computers can directly and easily act as nodes (which makes it tough for governments to block).
 Learn about Bastyon here:
Learn about Bastyon here: How Bastyon Works | Simplified Privacy
 ~~
Monero
Monero hides the data by having fake “decoy” signers. Then having the reciever download and scan all the transactions for a match.
~~
Monero
Monero hides the data by having fake “decoy” signers. Then having the reciever download and scan all the transactions for a match.
 Learn about Monero here: https://video.simplifiedprivacy.com/how-xmr-works/
~~
The NSA Taps the Ocean Cables
Learn about Monero here: https://video.simplifiedprivacy.com/how-xmr-works/
~~
The NSA Taps the Ocean Cables


 Proof of Concept Beta
The VPN currently supports split-traffic, but the cover traffic is manual. For example, opening a 2nd profile with a 12-hour music list, which is very easy with a bookmark homepage. One advantage of manual, is the server doesn’t know if it’s cover traffic or not. But we will be automating the cover traffic in future beta rounds.
Learn About Our Split Approach:
Proof of Concept Beta
The VPN currently supports split-traffic, but the cover traffic is manual. For example, opening a 2nd profile with a 12-hour music list, which is very easy with a bookmark homepage. One advantage of manual, is the server doesn’t know if it’s cover traffic or not. But we will be automating the cover traffic in future beta rounds.
Learn About Our Split Approach: NSA Taps Ocean Cables, So Our VPN Splits Traffic | Simplified Privacy
Session messenger has a structure setup for Crypto-Anarchy.
 Because not only does it have no physical locations, but its own DNS for assigning keys. There is no path to stop it. Not even discovering the location of the server... The domain can be re-assigned.
Yet it gets a lot of criticism. For example not rotating encryption keys automatically. So to better understand his design decisions, our organization interviewed KeeJef, Session Messenger's lead-developer.
Interview w/ KeeJef:
Because not only does it have no physical locations, but its own DNS for assigning keys. There is no path to stop it. Not even discovering the location of the server... The domain can be re-assigned.
Yet it gets a lot of criticism. For example not rotating encryption keys automatically. So to better understand his design decisions, our organization interviewed KeeJef, Session Messenger's lead-developer.
Interview w/ KeeJef:

 Because not only does it have no physical locations, but its own DNS for assigning keys. There is no path to stop it. Not even discovering the location of the server... The domain can be re-assigned.
Yet it gets a lot of criticism. For example not rotating encryption keys automatically. So to better understand his design decisions, our organization interviewed KeeJef, Session Messenger's lead-developer.
Interview w/ KeeJef:
Because not only does it have no physical locations, but its own DNS for assigning keys. There is no path to stop it. Not even discovering the location of the server... The domain can be re-assigned.
Yet it gets a lot of criticism. For example not rotating encryption keys automatically. So to better understand his design decisions, our organization interviewed KeeJef, Session Messenger's lead-developer.
Interview w/ KeeJef:
Interview: KeeJef on Session Messenger Misunderstandings | Simplified Privacy

The biometric prison has begun.
Amazon landed a deal with a hospital for a new hand-palm biometric sign-in for patients.
They are targeting the sick and elderly, and say it's for convenience. C'mon scan that palm grandma.
1 million patients per year at these facilities for "Amazon One". It's optional... for now.
What could go wrong? Oh, other than a year ago, quote: "Leaked documents reveal patient safety issues at Amazon’s One Medical" [2]
Sources:
[1]  [2]
[2]

Reclaim The Net
Amazon Expands Biometric Palm Scanning to Healthcare with NYU Langone Partnership
Amazon's biometric payment system makes a bold entry into healthcare, raising fresh concerns over privacy and data security.
MSN
It’s ironic that they are trying to pass this law to stop drugs:
Because that’s what I think the politicians are smoking.
View quoted note →
Cloudflare is now blocking niche browsers.
They just started doing it. Now they decide what software you can run. [1]
BLOCKED: Pale Moon, Falkon, and SeaMonkey
ALLOWED: Chromium, Firefox
WHY: I believe they are purposefully trying to reduce the choices, so you're more likely to use the same browsers, that are more easily fingerprinted. Pale Moon is considered better by some, but.. Once again I am pounding the table that:
a) If you're looking to do unique stuff, you're going to stand-out as unique
b) If you think custom mods and forks is the answer, you're sticking out like a sore thumb, based on what flavors of JavaScript, you're uniquely blocking. So..
c) Plugins, forks, & extensions are not going to change the fundamental nature of web browsers, which is that...
d) The way Chromium & Firefox are structured, is designed to empower the website developer, and not you. But..
e) You will not be able to stop using Web Apps, give it up. It's a dying battle. Instead,
f) Simplified Privacy is a 2nd Linux distro of browsers, to empower you with enough options at the tips of your fingers, (such as different versions of the same browser), to easily and effortlessly overwhelm their surveillance.
If you have not already spent the (less than 10 minutes) reading my Cloudflare Fingerprinting Guide, it's spoon-feeding you the critical information, with easy memes:
[2]
[1] News on Blocking Niche Browsers:

They Update Your Fingerprint Every 5 Minutes | Simplified Privacy

Cloudflare blocking Pale Moon and other browsers
: Not on Firefox or a Chrome derivative? You shall not pass
Every single tech website has news articles on Firefox's changing of their data privacy terms.
If you waste time reading one line of their terms of service, you're a sucker. Mozilla has been doing corrupt spyware for years, and it's never going to change. All the bickering over this is a "time honeypot", in the sense that it wastes your time and captures attention from real solutions.
Mozilla’s only real revenue, is being paid by Google millions of dollars a year to suck. The money is NOT based on users or any kind of success. They get paid to just use Google search, Google backdoors, and shut up. Google's goal is to not have competition to Chromium or their Search. They don't want Mozilla to succeed, it's on purpose their tech sucks.
The real answer is our app's 2nd Linux distro that guts the telemetry and isolates the filesystem and networking stack. This article goes over the core issues with Mozilla, that also apply to Tor:
Web Browsers Can't Resist | Simplified Privacy