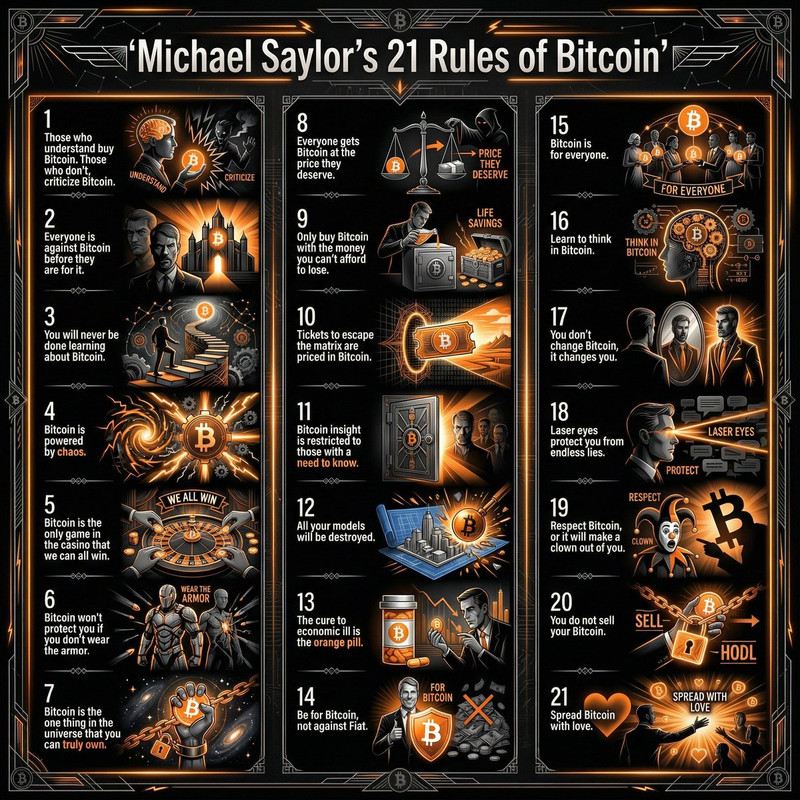
Asked AI - "How Facebook (Meta) can surveil people and build profiles?"
and got nice answer. This applies to other [a]social networks too.
Below is a concise, evidence-based breakdown of common mechanisms Meta uses to collect data and create profiles — for both users and non‑users — and what that profile typically contains.
Data sources
On‑platform activity: posts, likes, shares, comments, stories, reactions, search history, pages/groups you follow, events you RSVP to.
Messenger/Instagram activity: messages, call metadata, DMs, story interactions.
Device and app signals: device IDs, OS, browser, app version, language, timezones, installed apps, battery/connection metadata.
Location: GPS, IP geolocation, Wi‑Fi and Bluetooth signals, check‑ins, location tags, inferred home/work.
Contact lists & uploads: address books synced by users (creates “shadow” links to non‑users).
Pixel and SDK tracking: Facebook Pixel, Conversions API, and SDKs on third‑party websites and apps report page views, clicks, purchases, cart contents, form submissions.
Cookies and cross‑site trackers: first‑ and third‑party cookies, browser fingerprinting, and cross‑site identifiers that follow users across sites.
Ad network and partner data: data brokers, advertisers, measurement partners, CRM uploads, offline event imports (store visits, purchases).
Social graph & interactions: friends, followers, group memberships, mutual connections, tags in photos — used to infer attributes about you.
External signals and public records: scraped public profiles, public posts, business listings, news, or other available datasets.
Key technical methods
Tracking pixels & SDKs: embed code that sends user actions from third‑party sites/apps back to Meta.
Browser fingerprinting: combine small device/browser attributes to identify users without cookies.
Cross‑device matching: link activity across phone, tablet, desktop using logins, device graphs, or hashed identifiers.
Machine learning inference: predict interests, demographics, political views, health, wealth, and purchase intent from behavioral patterns and correlated data.
Data linkage / identity resolution: match emails, phone numbers, hashed identifiers, and contact lists to connect records (creates “shadow profiles” for non‑users).
Lookalike modelling: build audiences by finding people who resemble known users for ad targeting.
What a profile can include
Demographics: age range, gender, language, likely location, inferred ethnicity.
Interests & behaviours: hobbies, pages liked, frequently visited sites, shopping categories, travel habits.
Political, religious, health, sexual orientation (inferred): flagged via behavior and proxies (often sensitive).
Commercial signals: purchase history, propensity to buy, lifetime value estimate.
Social connections: friends, family, workplace, group affiliations.
Device and technical identifiers: device IDs, IP ranges, browser fingerprints.
Engagement scores: how likely you are to click, convert, or engage with specific ad types.
Uses of these profiles
Ad targeting and measurement: serve, optimize, and report ads (custom audiences, lookalikes, retargeting).
Personalization: content ranking, recommendations, friend suggestions, notifications.
Security & fraud detection: anomaly detection, account verification.
Product development & research: train models to improve features and targeting tools.
Special note: shadow profiles and non‑users
Meta can construct profiles for non‑users from others’ address books, tracker signals on websites/apps, and aggregated inferences. Academic research has documented shadow profiles and cross‑site tracking that covers many non‑users.
Mitigations (brief)
Use browser privacy protections (block third‑party cookies, disable trackers), tracker‑blocking extensions, private browsing, and VPNs.
Limit contact uploads to services, avoid logging into sites with Facebook/Meta, opt out of ad personalization where possible, and review app permissions.
For accounts: tighten privacy settings, remove third‑party app access, and limit profile info and tagging.
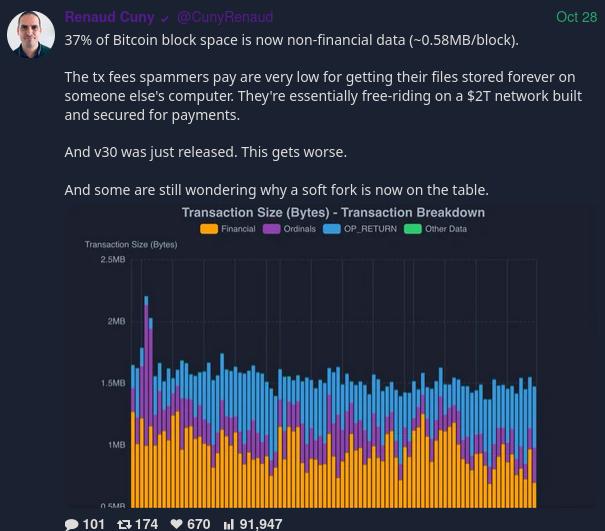
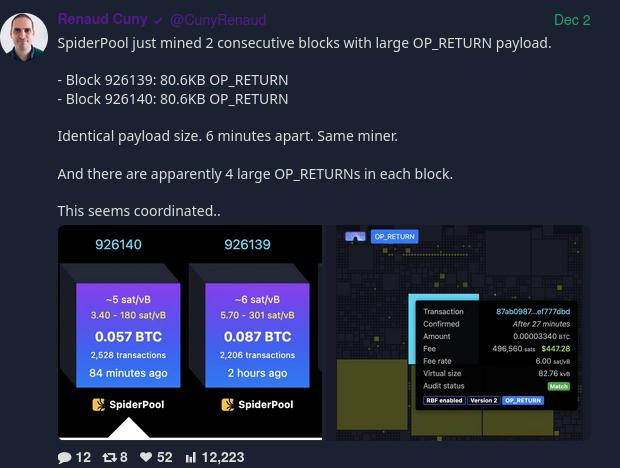
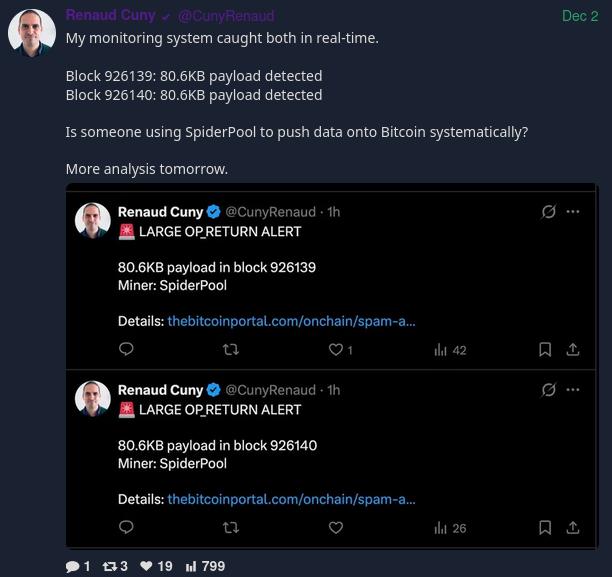 nostr:nevent1qqsflgsv92lel2sumsgv7tpautp7mw9mer4rqva2x30dewejgfr2u3qppemhxue69uhkummn9ekx7mp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszyrhwden5te0dehhxarj9ekk7mf0epp9dj
nostr:nevent1qqsflgsv92lel2sumsgv7tpautp7mw9mer4rqva2x30dewejgfr2u3qppemhxue69uhkummn9ekx7mp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszyrhwden5te0dehhxarj9ekk7mf0epp9dj

 nostr:nevent1qqsflgsv92lel2sumsgv7tpautp7mw9mer4rqva2x30dewejgfr2u3qppemhxue69uhkummn9ekx7mp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszyrhwden5te0dehhxarj9ekk7mf0epp9dj
nostr:nevent1qqsflgsv92lel2sumsgv7tpautp7mw9mer4rqva2x30dewejgfr2u3qppemhxue69uhkummn9ekx7mp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszyrhwden5te0dehhxarj9ekk7mf0epp9dj
 nostr:nevent1qqsf8djkj2nrdjk34fmmvyg0wh0mhezv003xqdj7jz2s9w400zn5d9cppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgcwaehxw309aex2mrp0yhxvmm4de6xz6tw9enx6tca9kgdx
nostr:nevent1qqsf8djkj2nrdjk34fmmvyg0wh0mhezv003xqdj7jz2s9w400zn5d9cppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgcwaehxw309aex2mrp0yhxvmm4de6xz6tw9enx6tca9kgdx nostr:nevent1qqs85r39pqkp0k35qxt47swectc06gdtv80nd64fflsky9av5kadj0sppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0wsx2f5
nostr:nevent1qqsz5wnm7h9r46crm7pgx2xnaztsfz93jylhclsyud4qqa5wp8pkwscppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgkwaehxw309aex2mrp0yhxummnw3ezumn9wshsvra270
nostr:nevent1qqs85r39pqkp0k35qxt47swectc06gdtv80nd64fflsky9av5kadj0sppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0wsx2f5
nostr:nevent1qqsz5wnm7h9r46crm7pgx2xnaztsfz93jylhclsyud4qqa5wp8pkwscppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgkwaehxw309aex2mrp0yhxummnw3ezumn9wshsvra270