Warning for #Android gapps traitors:
Uninstall the application: Android System SafetyCore, which has been automatically installed on most devices. It is used by Google to scan your data, just like Apple has been doing on iOS, but you have the choice to uninstall it. If you don't have it yet, watch out for it being installed silently over the next few days!
https://play.google.com/store/apps/details?id=com.google.android.safetycore
Be careful on GrapheneOS too if you have Google services installed.
While GrapheneOS will stop it from auto installing, it can nag you about installing it. And it won't tell you what it really is. Nor will most online resources.
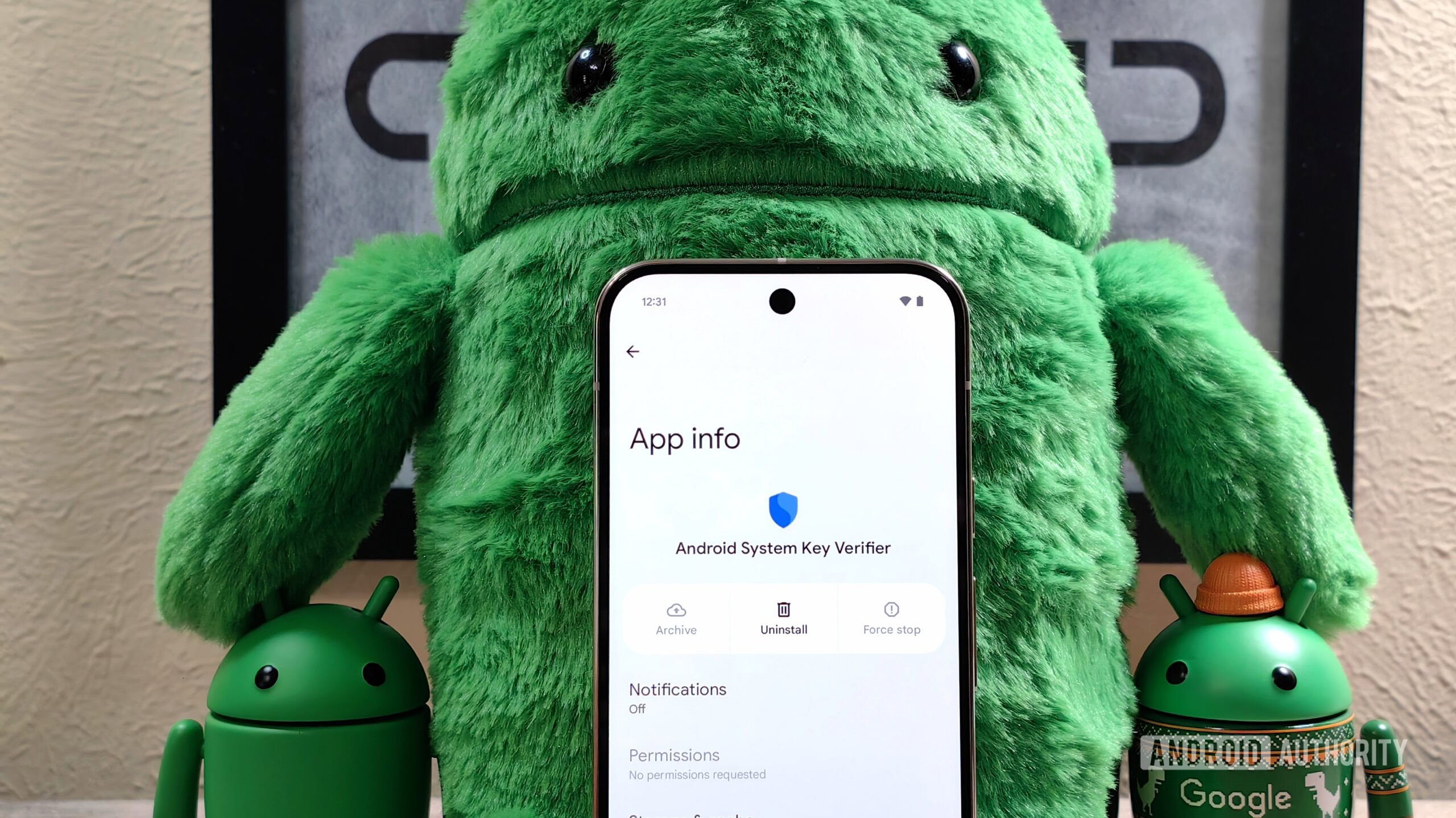
Sandboxed Google Play compatibility layer: stop Play Store from attempting to auto-install some system component packages, such as "Android System SafetyCore" (com.google.android.safetycore) and "Android System Key Verifier" (com.google.android.contactkeys)
The phone is asking me to install this app, anyone knows information about if its truly need it or not? Im with the Google Play Services sandbox install
 If you don't have GrapheneOS, it's going to automatically install itself again at some point after uninstalling it.
Locating the App
Go to Settings → Apps (or Apps & Notifications) → Show system apps. Look for “Android System SafetyCore.”
Check whether the app has any special permissions (e.g., internet access).
Uninstalling or Disabling
In many cases, you can uninstall an update or at least disable the app. Check the available options in the app info.
This is client side scanning. It's a way to spy on your device before it's encrypted.
Other information on the topic:
If you don't have GrapheneOS, it's going to automatically install itself again at some point after uninstalling it.
Locating the App
Go to Settings → Apps (or Apps & Notifications) → Show system apps. Look for “Android System SafetyCore.”
Check whether the app has any special permissions (e.g., internet access).
Uninstalling or Disabling
In many cases, you can uninstall an update or at least disable the app. Check the available options in the app info.
This is client side scanning. It's a way to spy on your device before it's encrypted.
Other information on the topic:

 The functionality provided by Google's new Android System SafetyCore app available through the Play Store is covered here:
The functionality provided by Google's new Android System SafetyCore app available through the Play Store is covered here:
 Neither this app or the Google Messages app using it are part of GrapheneOS and neither will be, but GrapheneOS users can choose to install and use both. Google Messages still works without the new app.
The app doesn't provide client-side scanning used to report things to Google or anyone else. It provides on-device machine learning models usable by applications to classify content as being spam, scams, malware, etc. This allows apps to check content locally without sharing it with a service and mark it with warnings for users.
It's unfortunate that it's not open source and released as part of the Android Open Source Project and the models also aren't open let alone open source. It won't be available to GrapheneOS users unless they go out of the way to install it.
We'd have no problem with having local neural network features for users, but they'd have to be open source. We wouldn't want anything saving state by default. It'd have to be open source to be included as a feature in GrapheneOS though, and none of it has been so it's not included.
Google Messages uses this new app to classify messages as spam, malware, nudity, etc. Nudity detection is an optional feature which blurs media detected as having nudity and makes accessing it require going through a dialog.
Apps have been able to ship local AI models to do classification forever. Most apps do it remotely by sharing content with their servers. Many apps have already have client or server side detection of spam, malware, scams, nudity, etc.
Classifying things like this is not the same as trying to detect illegal content and reporting it to a service. That would greatly violate people's privacy in multiple ways and false positives would still exist. It's not what this is and it's not usable for it.
GrapheneOS has all the standard hardware acceleration support for neural networks but we don't have anything using it. All of the features they've used it for in the Pixel OS are in closed source Google apps. A lot is Pixel exclusive. The features work if people install the apps.
https://xcancel.com/GrapheneOS/status/1888280836426084502
Neither this app or the Google Messages app using it are part of GrapheneOS and neither will be, but GrapheneOS users can choose to install and use both. Google Messages still works without the new app.
The app doesn't provide client-side scanning used to report things to Google or anyone else. It provides on-device machine learning models usable by applications to classify content as being spam, scams, malware, etc. This allows apps to check content locally without sharing it with a service and mark it with warnings for users.
It's unfortunate that it's not open source and released as part of the Android Open Source Project and the models also aren't open let alone open source. It won't be available to GrapheneOS users unless they go out of the way to install it.
We'd have no problem with having local neural network features for users, but they'd have to be open source. We wouldn't want anything saving state by default. It'd have to be open source to be included as a feature in GrapheneOS though, and none of it has been so it's not included.
Google Messages uses this new app to classify messages as spam, malware, nudity, etc. Nudity detection is an optional feature which blurs media detected as having nudity and makes accessing it require going through a dialog.
Apps have been able to ship local AI models to do classification forever. Most apps do it remotely by sharing content with their servers. Many apps have already have client or server side detection of spam, malware, scams, nudity, etc.
Classifying things like this is not the same as trying to detect illegal content and reporting it to a service. That would greatly violate people's privacy in multiple ways and false positives would still exist. It's not what this is and it's not usable for it.
GrapheneOS has all the standard hardware acceleration support for neural networks but we don't have anything using it. All of the features they've used it for in the Pixel OS are in closed source Google apps. A lot is Pixel exclusive. The features work if people install the apps.
https://xcancel.com/GrapheneOS/status/1888280836426084502
Releases | GrapheneOS

GrapheneOS Discussion Forum
android system safety core - GrapheneOS Discussion Forum
GrapheneOS discussion forum
Android Authority
Google's new app will help warn you about nude images in Messages
Google is rolling out Android System SafetyCore, and it'll power the upcoming Sensitive Content Warnings feature in Messages.
Android Authority
Google's new Android app helps you verify you're chatting with the right person
Google is rolling out a new Android System Key Verifier app that helps you verify you're chatting with the right person and not a scammer.

Google Online Security Blog
5 new protections on Google Messages to help keep you safe
Posted by Jan Jedrzejowicz, Director of Product, Android and Business Communications; Alberto Pastor Nieto, Sr. Product Manager Google Messa...