Anant Tapadia
anant@bithyve.com
npub18wzt...enfd
Bitcoin Keeper and Bitcoin Tribe
I don’t think anything will be as special as the 100k milestone, not a million not 10 millions. Nothing.
What makes 5th December 2024 special is the pain and ridicule and every hard decision that came before it. I don’t think that will be the case from here on.
Nature is healing ❤️🩹 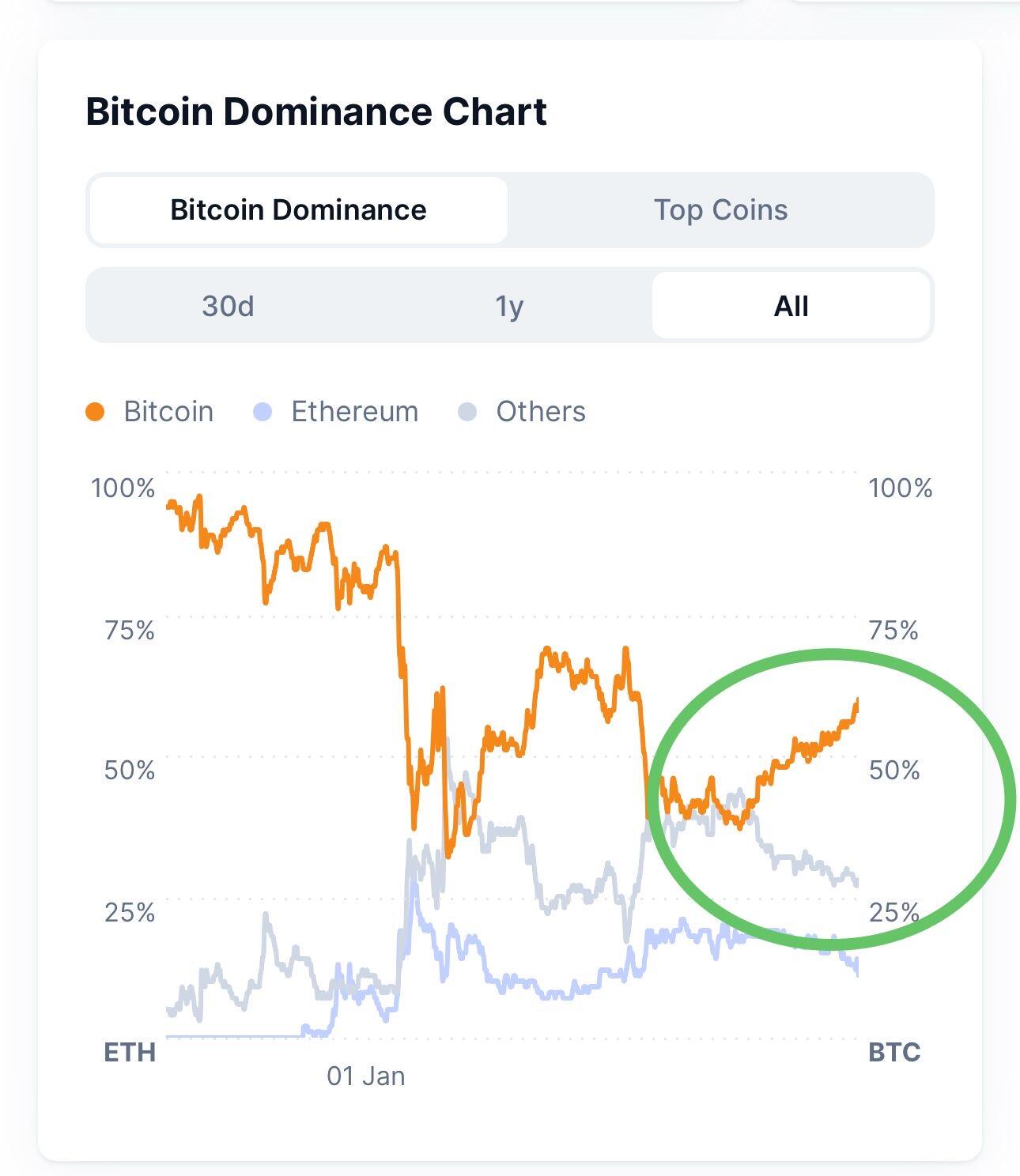

Have been doing some reading into these two and this is what I have found so far:
#Nostr vs #HolePunch
Both are decentralized communication technologies, but they tackle different challenges. How are they different?
*Nostr: The Public Notice Board*
Nostr operates like a public notice board. Users sign messages with their private keys and broadcast them to relays, which then distribute and store the messages. These relays ensure that the message remains accessible even if the user is offline. This makes Nostr ideal for public communication, such as decentralized social media, where you want to share content widely and ensure its availability over time.
However, while Nostr can encrypt the content of direct messages, it doesn’t hide metadata—relays can still see who is communicating and when. Nostr lacks the direct peer-to-peer encryption necessary for truly private communication. Relays merely store and distribute messages without establishing any shared secret between users, which means the privacy of direct communication is limited.
*Hole Punch: The Secure, Peer-to-Peer Messaging System*
Holepunch takes a completely different approach. It’s built for private, peer-to-peer communication without relying on any relays or third-party servers. Instead, it uses Diffie-Hellman key exchange to create a shared secret between two peers, enabling end-to-end encryption. This means that the message is only visible to the intended recipient, with no one else able to see the content or even who is communicating. Since Holepunch establishes direct P2P connections, there’s no metadata leakage—no third party can track when or with whom you’re communicating.
Holepunch is designed for real-time, private communication like messaging, secure file transfers, or live collaboration. Unlike Nostr, it’s not built for broadcasting or asynchronous content distribution but shines when it comes to privacy and security in direct interactions.
*The Complementary Roles*
While Nostr handles public communication efficiently, Holepunch excels in privacy-focused, direct communication. Nostr’s relay system makes it scalable and ideal for broadcasting messages widely across a decentralized network, but it’s not designed for high privacy in one-on-one interactions. Holepunch, on the other hand, is ideal for private conversations that require end-to-end encryption and secure, real-time communication, with no exposure to intermediaries.
Together, they provide a well-rounded solution: Nostr for public broadcasting and Holepunch for private, secure communication. They complement each other, covering both public and personal use cases in the decentralized world.
Start of the end for #ethereum? 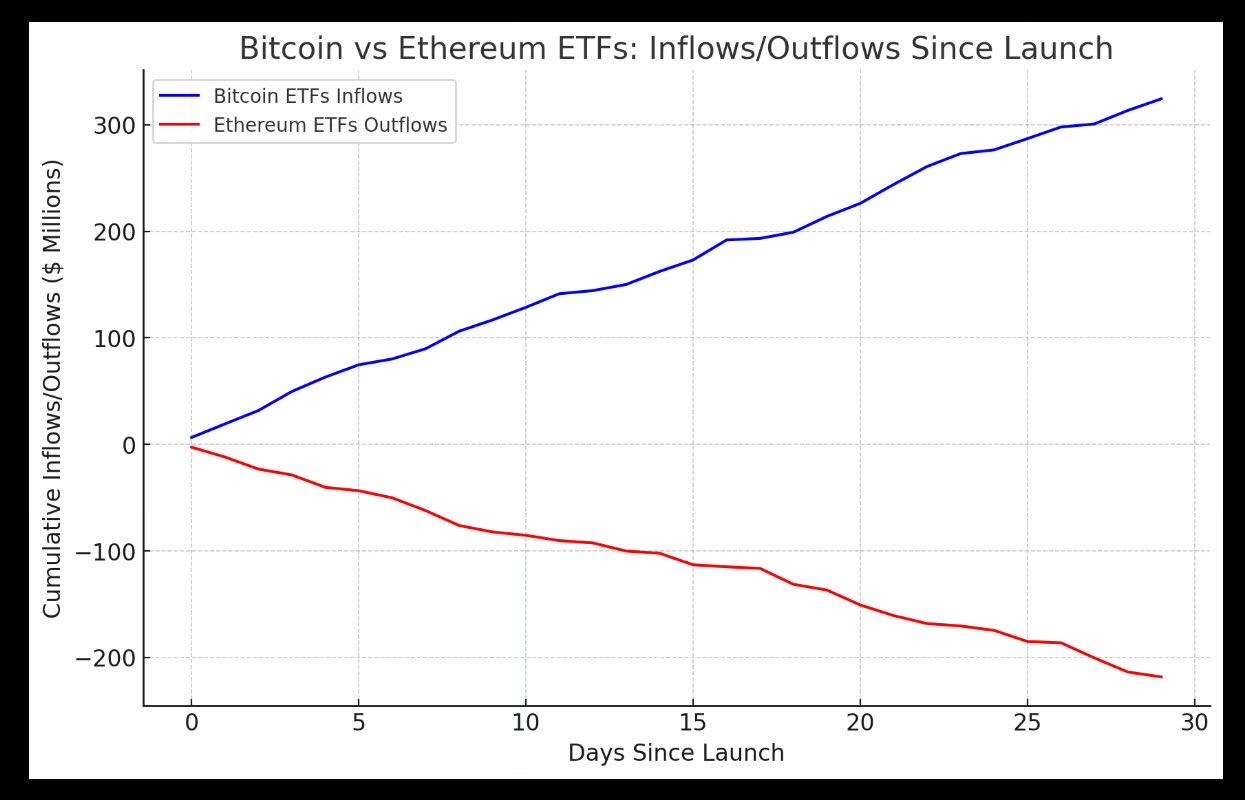

Can someone tell Bitcoin that 58k was only a meme?
I don’t travel to usual places!!! 

### Like PGP, But Better: Apple’s Contact Key Verification
*This is why I believe Apple is net positive for privacy:*
Apple’s Contact Key Verification is like PGP but with far better usability, making secure communication accessible to everyone without the complexity. It lets you confirm that the person you’re messaging is who they say they are, protecting you from potential impersonation or interception.
This feature is part of a broader commitment to privacy across Apple’s ecosystem:
- **End-to-End Encryption** in iMessage and FaceTime ensures only you and your recipient can access your messages and calls.
- **App Tracking Transparency** gives you control over which apps can track your activity across other apps and websites.
- **Mail Privacy Protection** stops email senders from tracking when you open an email and masks your IP address.
- **Privacy Labels** on the App Store let you see how apps handle your data before you download them.
- **On-Device Siri Processing** keeps your voice data on your device, reducing the need to send information to Apple’s servers.
- **Secure Enclave** stores sensitive information like biometric data securely on your device, ensuring it never leaves.
- **Sign in with Apple** allows you to sign into apps while keeping your email private.
While Apple’s code is closed-source, meaning we have to trust their implementation, their track record of resisting pressure to weaken encryption and their commitment to user privacy make them a strong choice for anyone serious about protecting their information. Contact Key Verification is just one example of how Apple is leading the way in making privacy both accessible and effective. 

Glad I was on Nostr way before it was a fad
Who else was here before August 2024? Who do I need to follow?
Lift HEAVY
Current state of US elections? 

@Gigi - just a quick note: I am still doing the squated back stretches you taught us before the hike.
What is a Recovery Key in Bitcoin Keeper?
A simple yet secure and private way to back up your wallets
There are no accounts in Keeper—not when you create a new app or use any of its features. And we want to keep it that way. It is the only way to be operationally efficient, legally safe, and KYC-free over the long term.
App Recovery
So, how do you recover the app when you want to get it on a new phone? Where is the metadata stored, and how is it retrieved?
Enter Recovery Key. Instead of creating a username and password for encryption and retrieval, we use the already existing mechanisms in bitcoin that users are well accustomed to. The Recovery Key is a 12-word BIP-39 seed phrase with a high entropy by definition and is generated on the user's device. This encrypts any app metadata before it is stored on the backend. The user is nudged, encouraged and warned to ensure these words are backed up securely. They are even reminded regularly to perform health checks for the key. Literature and tools for backing up BIP-39 words are abundant in the bitcoin space.
When the app needs to be recovered, the user simply enters their Recovery Key, and the whole app is restored. It is also worth clarifying that this metadata contains no private key.
Mobile Keys
But what about the hot keys? (In Keeper, these are called Mobile Keys). How are they generated and recreated in the recovered app?
Short answer: BIP-85 deterministic entropy. Long form: The magic of BIP-85 is that you can generate multiple seeds from a single parent. The app uses the Recovery Key as the parent to create hot keys. It is done on the user's device when the app is created new or when it is recovered. Individual wallet seed words do not have to be backed up but can be used to create a wallet on another app (w/o having to back them up as the parent is already backed up on Keeper).
BIP-85 allows you to have multiple hot (mobile) keys, but Keeper does not allow you to use more than one hot key in any multisig (obviously). It also does not allow the Recovery Key to be used as a signer in any wallet.
Inheritance
So, how does this work with Inheritance? Is it another thing the user must pass on to their heirs?
<Image showing RK being passed onto the heir or something>
Wallet configuration files (a.k.a. output descriptors or BSMS) are essential to any multisig scheme (Vaults in Keeper). When you recover a Keeper app using the Recover Key, all the multisig vaults are restored along with their configurations. As such, the configuration files are not needed explicitly. So, a single Recovery Key backs up multiple configuration files and changes them dynamically if something changes in a vault (e.g. key rotation). This provides a convenient, secure and private way to back up configuration files.
This, however, is dependent on the Keeper backend, and that is why we also give users the option to back up these files on their own cloud or manually for each vault.
Conclusion
Recovery Key uses bitcoin native ways to backup your app, generate hot keys, and secure multisig configurations. The user simply has to note down the 12-word phrase. This is a big win for UX, security, and privacy. 

Yo
#introductions
Fedi + B4I = match made in bitcoin heaven
Invite code:
fed1149v4kvv003pe7678pppcpn0ewmu9k8lh9tj3272alte9a5cukclkzyelvges5txvuqlym83lmpu7wqptwaehxw309anx2erfd45kuary9enx2erfd45kuapwvf5hgcm0d9hrg6twv35kztn0wfnj7ar5hjztcal2pfl7cyglgqm58q
#bitcoin lessons hidden in Bhagavad Gita. #3
Trust in the Divine and Self: The Gita encourages trust and faith in one's chosen path and the universe's divine order
In Bitcoin, individuals must place trust in none but the decentralized network and cryptographic protocols that ensure the security and integrity of transactions rather than relying on trust in intermediaries or centralized authorities 

#Bitcoin lessons hidden in ₿hagavad Gita. #2
Arjuna's Dilemma: The warrior faces a moral dilemma on the battlefield, unsure whether to fight in the righteous war. This reflects an individual's struggle to make independent choices
Similarly, Bitcoin encourages individuals to make their own financial decisions rather than relying on centralized financial systems that may have conflicting interests 

#bitcoin lessons hidden in Bhagavad Gita
#1 : Lord Krishna emphasizes to Arjuna the importance of personal responsibility and self-mastery
Similar to how bitcoiners promote individual financial sovereignty, where individuals have full control over their funds and need to master basic skills 

What is Nostr? (Not technical answers)